On March 21, 2025, a severe security flaw in Next.js, dubbed CVE-2025-29927, sent shockwaves through the developer community. Rated a critical 9.1 out of 10 on the CVSS scale, this vulnerability exposes Next.js applications to unauthorized access by allowing attackers to bypass middleware-based authorization checks. If you’re running a Next.js app, here’s everything you need to know—who’s affected, how it works, and what you can do to stay secure.
What Is CVE-2025-29927?
Next.js is a powerful React framework loved by developers for its simplicity in building full-stack web applications. One of its key features is middleware, which lets you intercept and process HTTP requests—for example, to enforce login requirements or restrict access to certain pages. CVE-2025-29927 reveals a flaw in this system: attackers can bypass these protections by manipulating a specific HTTP header, x-middleware-subrequest.
This header is an internal tool Next.js uses to manage subrequests and avoid infinite loops. However, before the fix, middleware didn’t properly validate whether this header came from a legitimate internal source or an external attacker. By adding x-middleware-subrequest: true to a request, a malicious user could trick the middleware into skipping security checks, potentially accessing sensitive data or functionality.
Timeline
- February 27, 2025: Disclosed to the Next.js team via GitHub.
- March 14, 2025: Next.js began triaging.
- March 21, 2025: Published as CVE-2025-29927 with patches released.
Who Is Affected?
Not every Next.js app is at risk, but many are. You’re vulnerable if:
- You’re using an affected version: Any Next.js version before 14.2.25 (for the 14.x branch) or 15.2.3 (for the 15.x branch). This includes older versions like 11.1.4 through 13.5.6, though no official patch exists for those yet.
- You rely on middleware for security: If your app uses middleware to enforce authentication or authorization (e.g., checking cookies or tokens), this flaw could undermine those protections.
- You self-host your app: Applications running with next start or a custom server setup are exposed. If you’re hosted on Vercel, Netlify, or similar platforms that filter requests before they hit Next.js, you’re in the clear—those environments automatically mitigate the issue.
Big enterprises, small startups, and solo developers alike could be impacted if they meet these criteria. With Next.js powering millions of sites, the scope is significant.
How Does It Work?
Imagine your app has a protected route, /dashboard, where middleware checks for a valid user session. Normally, an unauthenticated user gets blocked. But with CVE-2025-29927, an attacker could send a request like this:

If your middleware doesn’t explicitly reject this header, it assumes the request is an internal sub request (like one triggered by Next.js itself) and skips the authorization check. Suddenly, the attacker is in—without credentials or permission.
The vulnerability earned its “Critical” label because it’s easy to exploit (low complexity), works over the internet, and requires no special privileges or user interaction. The potential damage? Exposure of private data or tampering with app functionality.
How to Fix It
The good news: Next.js acted fast. Here’s how to protect your application:
- Upgrade to Next.js version 14.2.25 or 15.2.3 (or later). These releases, rolled out on March 21, 2025, patch the vulnerability by ensuring middleware properly handles the x-middleware-subrequest header.
- Run npm install [email protected] or npm install [email protected] (adjust for your package manager) and redeploy.
Update Immediately
- If upgrading isn’t an option yet, block external requests with the x-middleware-subrequest header before they reach your Next.js app. You can do this with a reverse proxy (like Nginx) or server-level rules. For example, in Nginx:
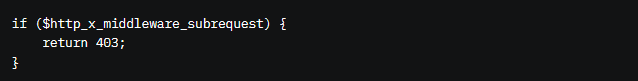
Temporary Workaround (If You Can’t Update)
Alternatively, add this check to your middleware:
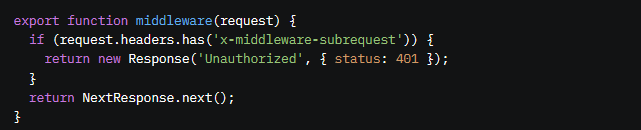
Verify Your Setup
- After patching, test your app to ensure middleware still enforces security as expected.
- Check your logs for suspicious requests with the x-middleware-subrequest header—a sign someone might’ve tried to exploit this.
Additional Tips and Insights
- Monitor for Exploitation: There’s no evidence of this being exploited in the wild yet, but Next.js’s open-source nature means attackers could reverse-engineer the fix. Set up alerts for unusual header activity in your logs.
- Older Versions: If you’re stuck on pre-14.x versions (e.g., 13.5.6 or earlier), no official patch exists yet, though a backport for 12.x was mentioned by Next.js. Consider the workaround or plan an upgrade.
- Credit Where It’s Due: Kudos to security researchers Allam Rachid (zhero___) and Allam Yasser (inzo_) for responsibly disclosing this flaw on February 27, 2025. The Next.js team triaged it by March 14 and shipped fixes a week later.
Why This Matters
This isn’t just a technical glitch—it’s a wake-up call. Middleware is a cornerstone of Next.js security, and a bypass like this shows how even robust frameworks can have subtle weaknesses. Posts on X and developer forums show a mix of alarm and relief: alarm at the severity, relief at the swift patch. One X user called it “trivially easy to bypass,” while another noted it’s “overhyped” for hosted apps—a fair point, but self-hosters can’t afford to shrug it off.
Final Thoughts
CVE-2025-29927 is a serious threat, but it’s manageable with quick action. Update your Next.js version today, or apply the workaround if you’re delayed. If you’re on Vercel, breathe easy—you’re already safe. Either way, this is a reminder to keep your dependencies current and double-check your security assumptions. Stay vigilant, and keep building awesome apps!