APIs (Application Programming Interfaces) are the backbone of modern applications, enabling seamless data exchange and functionality across diverse systems.
However, this reliance on APIs has also made them a prime target for cyberattacks. As we look ahead, understanding the evolving API security threats is crucial for developers, security teams, and organizations of all sizes. Ignoring these risks can lead to data breaches, financial losses, and reputational damage.

This article delves into the top 10 API security threats that developers must be aware of in 2025. We'll explore each risk in detail, providing actionable insights and strategies to mitigate them effectively.
Whether you're a CISO, a SOC team member, an ethical hacker, or an MSSP, this guide will equip you with the knowledge to protect your APIs and safeguard your organization's critical assets. Furthermore, we will discuss how TRaViS can help organizations proactively manage their API security posture and reduce their attack surface.
1. Broken Object Level Authorization (BOLA)
Broken Object Level Authorization (BOLA), also known as Insecure Direct Object References (IDOR), remains a persistent and critical API security threat. BOLA vulnerabilities occur when an API allows users to access objects or data that they are not authorized to view or modify. Attackers can exploit these vulnerabilities by manipulating object IDs or parameters in API requests to gain unauthorized access to sensitive information.
Why BOLA is a Top Threat in 2025:
- Prevalence: BOLA vulnerabilities are common due to inadequate authorization checks in API implementations.
- Impact: Successful BOLA exploits can lead to unauthorized access to user accounts, financial data, and other confidential information.
- Complexity: Identifying and mitigating BOLA vulnerabilities can be challenging, especially in complex API ecosystems.
Example:
Consider an API endpoint that retrieves user profile information using the following URL:
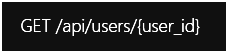
If the API does not properly validate whether the requesting user is authorized to access the profile information for the specified user_id, an attacker could simply change the user_id parameter to access other users' profiles.
Mitigation Strategies:
- Implement robust authorization checks: Verify that the requesting user has the necessary permissions to access the requested object.
- Use indirect object references: Replace direct object IDs with opaque, unguessable identifiers.
- Implement access control lists (ACLs): Define granular access control policies for each object.
- Regularly audit API endpoints: Conduct thorough security testing to identify and remediate BOLA vulnerabilities.
How TRaViS Helps:
TRaViS's External Attack Surface Management (EASM) platform helps organizations discover and monitor all their external-facing APIs, including shadow APIs and zombie APIs. By continuously scanning for vulnerabilities and misconfigurations, TRaViS can identify potential BOLA vulnerabilities and provide actionable insights to remediate them before they are exploited. TRaViS also integrates with existing security workflows, allowing security teams to efficiently manage and prioritize API security risks.
2. Broken Authentication
Broken authentication vulnerabilities arise when APIs fail to properly authenticate users, allowing attackers to impersonate legitimate users or gain unauthorized access to sensitive resources. Weak password policies, flawed session management, and reliance on default credentials are common causes of broken authentication.
Why Broken Authentication is a Top Threat in 2025:
- Evolving Attack Techniques: Attackers are constantly developing new techniques to bypass authentication mechanisms.
- Increased Complexity: Modern applications often rely on multiple authentication methods, increasing the attack surface.
- Impact: Successful broken authentication attacks can lead to account takeovers, data breaches, and financial fraud.
Example:
An API that uses a weak password policy (e.g., allowing short or easily guessable passwords) is vulnerable to brute-force attacks. Attackers can use automated tools to try different password combinations until they successfully gain access to a user account.
Mitigation Strategies:
- Implement strong password policies: Enforce minimum password length, complexity requirements, and regular password resets.
- Use multi-factor authentication (MFA): Require users to provide multiple forms of authentication, such as a password and a one-time code.
- Implement secure session management: Use strong session identifiers, set appropriate session timeouts, and invalidate sessions upon logout.
- Regularly audit authentication mechanisms: Conduct penetration testing to identify and remediate authentication vulnerabilities.
How TRaViS Helps:
TRaViS helps organizations strengthen their API authentication mechanisms by identifying weak or misconfigured authentication schemes. TRaViS can also detect the use of default credentials and other authentication vulnerabilities, providing actionable recommendations to improve API security posture. By continuously monitoring the external attack surface, TRaViS helps organizations proactively identify and remediate authentication-related risks before they are exploited.
3. Injection Attacks
Injection attacks occur when attackers inject malicious code or commands into an API, causing it to execute unintended actions. SQL injection, command injection, and cross-site scripting (XSS) are common types of injection attacks.
Why Injection Attacks are a Top Threat in 2025:
- Ubiquity: Injection vulnerabilities are prevalent in APIs that do not properly validate user input.
- Severity: Successful injection attacks can lead to data breaches, server compromise, and denial-of-service (DoS) attacks.
- Evolving Techniques: Attackers are constantly developing new injection techniques to bypass security controls.
Example:
An API that uses user-supplied input in a SQL query without proper sanitization is vulnerable to SQL injection. An attacker could inject malicious SQL code into the input field, allowing them to bypass authentication, access sensitive data, or even modify the database.
Mitigation Strategies:
- Validate and sanitize all user input: Ensure that all user-supplied input is properly validated and sanitized before being used in API logic.
- Use parameterized queries or prepared statements: These techniques prevent attackers from injecting malicious code into SQL queries.
- Implement input validation on the server-side: Do not rely solely on client-side validation, as it can be easily bypassed.
- Regularly scan for injection vulnerabilities: Use automated tools to scan APIs for common injection vulnerabilities.
How TRaViS Helps:
TRaViS's EASM platform helps organizations identify and remediate injection vulnerabilities in their APIs. By continuously scanning for common injection patterns and misconfigurations, TRaViS can provide actionable insights to prevent successful injection attacks. TRaViS also integrates with existing security workflows, allowing security teams to efficiently manage and prioritize injection-related risks.
4. Rate Limiting and Resource Exhaustion
APIs that lack proper rate limiting and resource management are vulnerable to denial-of-service (DoS) attacks and resource exhaustion. Attackers can flood the API with requests, overwhelming the server and making it unavailable to legitimate users.
Why Rate Limiting and Resource Exhaustion are a Top Threat in 2025:
- Increased API Usage: As APIs become more widely used, the risk of resource exhaustion increases.
- Sophisticated Botnets: Attackers can use sophisticated botnets to launch large-scale DDoS attacks.
- Cloud Vulnerabilities: Cloud-based APIs are particularly vulnerable to resource exhaustion due to the elastic nature of cloud resources.
Example:
An API that does not limit the number of requests from a single IP address is vulnerable to a DDoS attack. An attacker could use a botnet to flood the API with requests, overwhelming the server and making it unavailable to legitimate users.
Mitigation Strategies:
- Implement rate limiting: Limit the number of requests that can be made from a single IP address or user within a given time period.
- Use caching: Cache frequently accessed data to reduce the load on the server.
- Implement resource quotas: Limit the amount of resources that can be consumed by a single user or application.
- Use a content delivery network (CDN): Distribute API traffic across multiple servers to reduce the impact of DDoS attacks.
How TRaViS Helps:
TRaViS helps organizations protect their APIs from rate limiting and resource exhaustion attacks by identifying APIs that lack proper rate limiting and resource management. TRaViS can also detect suspicious traffic patterns and potential DDoS attacks, providing actionable insights to mitigate these risks. By continuously monitoring the external attack surface, TRaViS helps organizations proactively identify and remediate resource exhaustion vulnerabilities before they are exploited.
5. Security Misconfiguration
Security misconfiguration vulnerabilities arise when APIs are not properly configured, leaving them vulnerable to attack. Common security misconfigurations include default credentials, unnecessary features enabled, and permissive access control policies.
Why Security Misconfiguration is a Top Threat in 2025:
- Complexity: Modern APIs are complex and require careful configuration to ensure security.
- Human Error: Security misconfigurations are often the result of human error or oversight.
- Evolving Threats: New security misconfigurations are constantly being discovered as APIs evolve.
Example:
An API that uses default credentials for administrative access is vulnerable to attack. An attacker could use these default credentials to gain unauthorized access to the API and perform malicious actions.
Mitigation Strategies:
- Follow security best practices: Implement secure configuration practices for all APIs.
- Disable unnecessary features: Disable any features that are not required for the API to function.
- Implement least privilege access control: Grant users only the minimum level of access required to perform their tasks.
- Regularly audit security configurations: Conduct regular security audits to identify and remediate security misconfigurations.
How TRaViS Helps:
TRaViS helps organizations identify and remediate security misconfigurations in their APIs. By continuously scanning for common misconfigurations and vulnerabilities, TRaViS can provide actionable insights to improve API security posture. TRaViS also integrates with existing security workflows, allowing security teams to efficiently manage and prioritize security misconfiguration risks. This includes identifying exposed API keys, misconfigured CORS policies, and other common configuration issues that can lead to security breaches. TRaViS's proactive approach ensures that security teams are aware of potential vulnerabilities before they can be exploited.
6. Improper Assets Management
In 2025, a significant API security threat stems from improper asset management. This includes a lack of visibility into all APIs, including shadow APIs and zombie APIs, as well as inadequate inventory management. Organizations often struggle to maintain an accurate and up-to-date inventory of their APIs, leading to overlooked vulnerabilities and potential attack vectors.
Why Improper Assets Management is a Top Threat in 2025:
- Lack of Visibility: Without a comprehensive inventory, organizations are unaware of all their APIs, making it impossible to secure them effectively.
- Shadow APIs: Undocumented and unmanaged APIs, often created by developers without security oversight, pose a significant risk.
- Zombie APIs: APIs that are no longer in use but remain active can be exploited by attackers.
Example:
A large enterprise has hundreds of APIs, but only a fraction are documented and actively managed. A shadow API, created for a specific project and then forgotten, contains a critical vulnerability. An attacker discovers this API and exploits the vulnerability to gain access to sensitive data.
Mitigation Strategies:
- Implement an API discovery process: Use automated tools to identify all APIs, including shadow and zombie APIs.
- Maintain a comprehensive API inventory: Keep an up-to-date inventory of all APIs, including their purpose, owner, and security posture.
- Regularly audit and decommission unused APIs: Identify and decommission zombie APIs to reduce the attack surface.
- Implement API governance policies: Establish clear policies for API development, deployment, and management.
How TRaViS Helps:
TRaViS's EASM platform provides complete visibility into an organization's external attack surface, including all APIs. TRaViS automatically discovers and inventories all APIs, including shadow and zombie APIs, providing a comprehensive view of the API landscape. By continuously monitoring APIs for vulnerabilities and misconfigurations, TRaViS helps organizations proactively manage their API assets and reduce their attack surface. This ensures that security teams have the information they need to prioritize and address the most critical risks.
Conclusion
As we move towards 2025, API security threats will continue to evolve and become more sophisticated. Organizations must prioritize API security and implement robust security measures to protect their critical assets. By understanding the top 10 API security threats and implementing the mitigation strategies outlined in this article, developers and security teams can significantly reduce their risk exposure. Leveraging tools like TRaViS's EASM platform can provide the visibility and control needed to proactively manage API security and stay ahead of emerging threats. Proactive monitoring, continuous vulnerability scanning, and robust security configurations are essential for maintaining a strong API security posture.

Learn more about API Security Services:
Ready to proactively protect your APIs from evolving threats? Schedule a demo with TRaViS today and discover how our EASM platform can provide complete visibility into your external attack surface and help you remediate critical vulnerabilities before they are exploited.