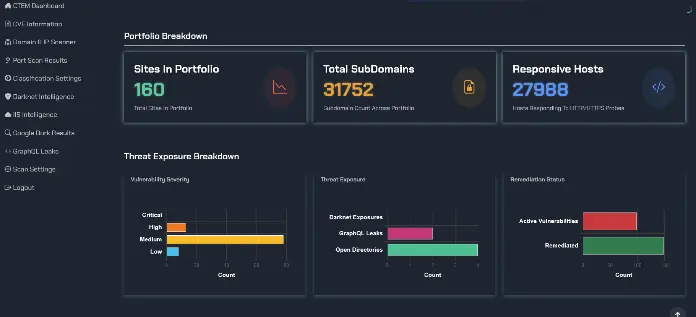
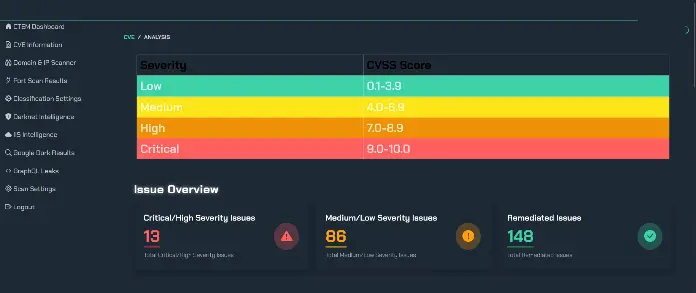
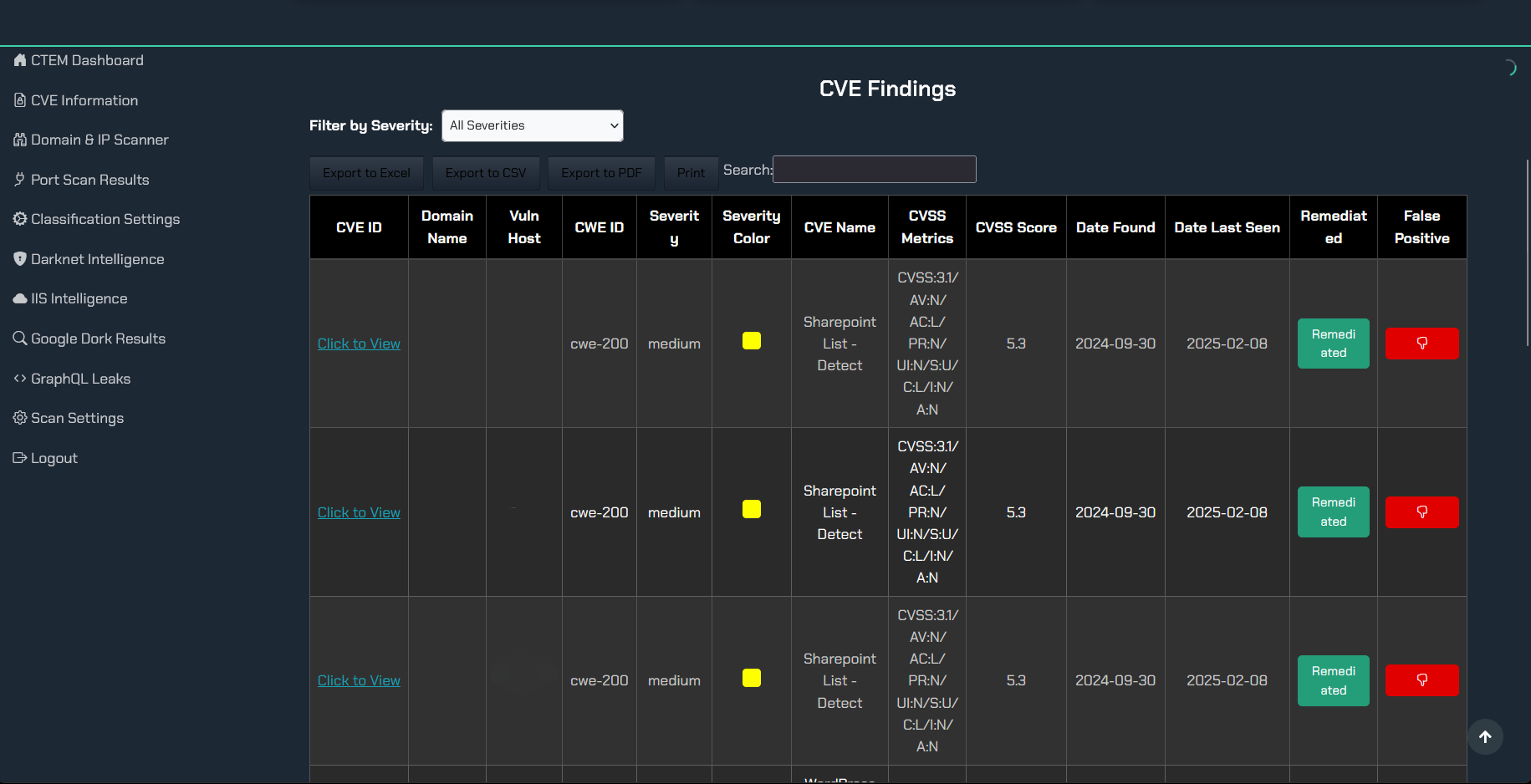
Think what you don't know can't hurt you? In cybersecurity, the opposite is true. If you can’t see an asset or vulnerability, rest assured attackers will. Organizations today are struggling to keep up with their expanding digital footprints. That’s why attack surface management (ASM) has gone from a nice-to-have to a must-have in modern cybersecurity strategy. After all, how can you protect what you can't even see?
Picture this: you get an alert about a breach, only to discover it came through a forgotten server or an exposed API that nobody tracked. As a CISO or IT administrator, discovering an attack came via an unknown asset is the ultimate nightmare scenario. Visibility into your infrastructure isn’t just a buzzword – it’s your first line of defense. In this article, we’ll break down what ASM is, why you need it, the key threats and tools in this space, and how to bolster your security strategy (with a hint of sarcasm along the way).
What is Attack Surface Management (ASM)?

Attack Surface Management is the continuous process of discovering, inventorying, and monitoring all of your organization’s IT assets – known and unknown – to identify and mitigate security risks across your entire attack surface. In plain English, it's about finding every digital door, window, and hidden tunnel into your systems and making sure they're secure. This comprehensive approach covers a lot of ground, including:
- External assets (domains, APIs, cloud services) – basically anything facing the public internet that attackers could see and probe.
- Internal networks (endpoints, databases, on-prem servers) – the behind-the-firewall systems that, if neglected, could be exploited by insiders or malware that sneaks past your perimeter.
- Cloud environments (misconfigurations, shadow IT in AWS/Azure/GCP) – because an open S3 bucket or misconfigured cloud app can bite you just as hard as any on-prem issue (the cloud isn’t automatically safe, surprise!).
- Third-party risks (vendors, supply chain partners) – exposures that come from the systems of your partners and suppliers. A weak link in your supply chain can quickly become your problem.
- Human factors (phishing, credential leaks, insider threats) – yes, employees and users are part of your attack surface too (like it or not, people will always be the wildcard in security).
In short, ASM is all about visibility across all these areas. If you don’t know an asset or exposure exists, you can’t secure it. So what happens if you lack that visibility? The statistics speak for themselves.
Why is Attack Surface Management Important?

Think your security team has everything under control? Think again. Here are some eye-opening stats that underscore why ASM and visibility are critical:
- 67% of organizations have significant blind spots due to shadow IT and misconfigured cloud assets. (Translation: parts of your network may as well be invisible to you.)
- 75% of breaches originate from unmanaged or unknown assets. In other words, the biggest threats often come from things you didn’t even know you had.
- 50%+ of internet-facing vulnerabilities are found in cloud environments. (Moving to the cloud without proper oversight can be like swapping one big front door for dozens of little side windows left open.)
- 80% of security teams say they can’t keep up with their rapidly expanding attack surface. (Overwhelmed IT staff, join the club.)
Numbers don’t lie: lack of visibility leads directly to security incidents. This is exactly why attack surface management—and the cybersecurity visibility it delivers—is so important. Instead of playing whack-a-mole with endless alerts, ASM gives you a fighting chance to see and prioritize risks before attackers do.
Types of Attack Surface Management
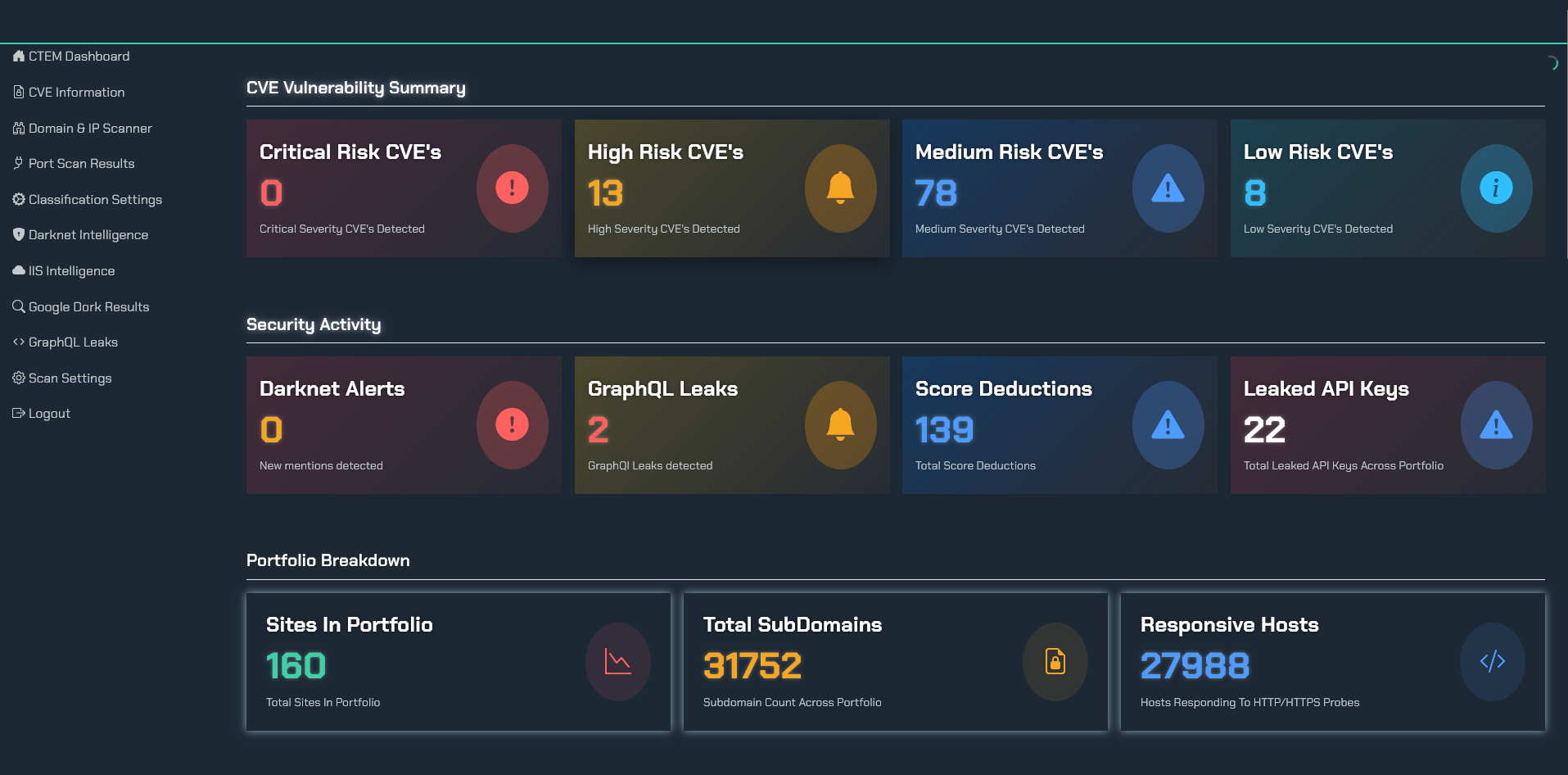
Attack surface management isn’t one-size-fits-all. In practice, it breaks down into a few categories, each focusing on a different slice of your environment’s risk:
-
External ASM (External Attack Surface Management) – Monitors your public-facing assets (web domains, SSL certificates, APIs, cloud services) so you know what an attacker sees when they look at your organization from the outside. This helps you catch exposed assets or misconfigurations before the bad guys do.
-
Internal ASM – Focuses on internal networks and systems (endpoints, internal servers, databases) to guard against insider threats and malware that breaches the perimeter. Just because an asset is inside your firewall doesn’t mean it’s automatically safe.
-
Cloud ASM – Digs into cloud infrastructure to detect misconfigurations, unsecured resources, and shadow IT in services like AWS, Azure, and Google Cloud. (Just because it’s “in the cloud” doesn’t mean it’s not your responsibility — cloud assets can be just as vulnerable if mismanaged.)
-
Third-Party ASM – Assesses risks stemming from third parties: your vendors, partners, and supply chain. A partner’s weak security practices can open the door to your network, so this category monitors and grades external organizations’ cyber risk to help plug any indirect holes.
-
Human ASM – Addresses the human element of your attack surface. This includes things like phishing simulations, credential leak monitoring, and user security training. People are part of your attack surface, whether it’s an employee using "Password123" or someone falling for a phishing email, so you’d better account for human risk in your ASM program.
Each “flavor” of ASM above contributes to the bigger picture: a 360-degree view of your attack surface. Together, they ensure that whether an asset lives on-prem, in the cloud, in your supply chain, or between an employee’s ears, you have visibility and can manage the risk.
Top Attack Surface Threats in 2025
.png?access_token=9bb3fedc-0d43-46c9-857c-0a0bbe2a90fa)
Knowing your assets is step one. Step two is understanding what threats are coming after those assets. So, what nasty surprises might be lurking across your attack surface today? Here are the top cyber threats ASM is designed to uncover and mitigate (circa 2025):
- Mimic Domains & Phishing Sites – Attackers are cloning legitimate websites and domains of organizations to trick users into divulging credentials or clicking malware. Think of it as the evil twin of your company’s site luring your customers or employees. If your brand has a web presence, chances are someone might be faking it
- Exposed Cloud Assets – Misconfigured cloud storage buckets, leaky APIs, and unmanaged cloud instances are rampant. An AWS S3 bucket left open to the public or an API with no authentication can leak data or provide easy access. (These cloud goof-ups are the modern equivalent of leaving the vault open — except it’s your data in there.)
- Open Ports & Unpatched Services – Unsecured open ports, outdated software, and unpatched vulnerabilities on internet-facing servers are basically welcome mats for ransomware and other attacks. It’s like leaving your front door unlocked and hoping no one tries it. Spoiler: attackers try those doors every day.
- Leaked Code & Credentials – Developers accidentally publishing sensitive code or config files to GitHub, employees reusing passwords that get dumped on Pastebin or the dark web... These leaked credentials and secrets are a goldmine for hackers. (Your dev’s throwaway test code from two years ago with an embedded password could be an attacker's ticket in. Yikes.)
- Early-Stage Attack Signals – Reconnaissance activities such as network probing, domain spoofing, or attackers registering lookalike domains often precede a major breach. These are the subtle, early warning signs that someone is poking around your attack surface, looking for a way in. If you catch the “knock at the door” early (say, a fake domain that resembles yours), you can act before the real attack comes knocking.
Staying on top of these threats is challenging, no doubt. Each of these tactics is continually evolving. However, recognizing them is half the battle—if you know what you’re up against, you can take targeted action to defend against it.
How to Strengthen Your ASM Strategy
Reading about all these risks might have you wondering, how on earth can we keep up? The good news is that a robust ASM strategy, combined with the right tools, can dramatically improve your security posture. Here are some key strategies to strengthen your attack surface management (and overall cybersecurity) approach:
-
Automated Asset Discovery – Use automated scanners and discovery tools to continuously map all your assets, including those “rogue” shadow IT systems that pop up without approval. If you’re still relying on manual inventories or spreadsheets to track assets, it’s time to upgrade — you simply won’t catch everything.
-
Vulnerability Prioritization – Prioritize and patch the most critical risks first. Not all vulnerabilities are created equal, and you can’t patch everything yesterday. Smart ASM means focusing on the high-risk holes (think exposed databases or critical CVEs) before attackers exploit them. It’s the difference between fixing the one window that’s actually broken versus installing new locks on every single one “just in case.”
-
Zero Trust Enforcement – Implement a Zero Trust model across your environment. This means enforcing least-privilege access controls and requiring multi-factor authentication (MFA) for users and devices by default. In other words, trust nothing and verify everything trying to connect to your network. By assuming every user or device could be hostile until proven otherwise, you shrink the attack surface accessible to an intruder.
-
Threat Intelligence Integration – Feed real-time threat intelligence into your ASM process. This could involve subscribing to threat feeds, dark web monitoring for your data, or integrating with threat intel platforms. The idea is to get early warnings about new attack techniques or indicators of compromise (IoCs) relevant to your assets. It’s like having a radar that alerts you when there’s suspicious activity on the horizon, so you’re not caught flat-footed.
-
AI-Driven Monitoring – Leverage machine learning and AI to detect anomalies and predict attack patterns across your attack surface. Modern attacks often involve automated, sophisticated tactics, so let algorithms sift through the deluge of data to flag what looks fishy. When hackers are using automation and AI to attack, you’ll want AI on your side too, acting as your tireless security sentry that never sleeps.
- Proactive Takedowns – Don’t just play defense – go on the offense against threats targeting you. For example, actively hunt down and takedown phishing sites or fraudulent domains impersonating your brand, and get leaked credentials removed from paste sites or black markets. If a malicious domain is hosting a fake version of your login page, work with authorities or use services to shut it down. Think of it as cutting off the attacker’s tools before they can be used against you.
By implementing the above, you transform ASM from a passive inventory exercise into an active defense mechanism. It’s all about being proactive: finding and fixing issues before they turn into breaches, and responding to threats before they fully unfold. Sure, it’s impossible to eliminate every risk (we’re not selling 100% magic shields here), but you can drastically reduce your exposure and respond faster than the attackers expect.
What TRaViS ASM Solves (Without the Tool Sprawl)
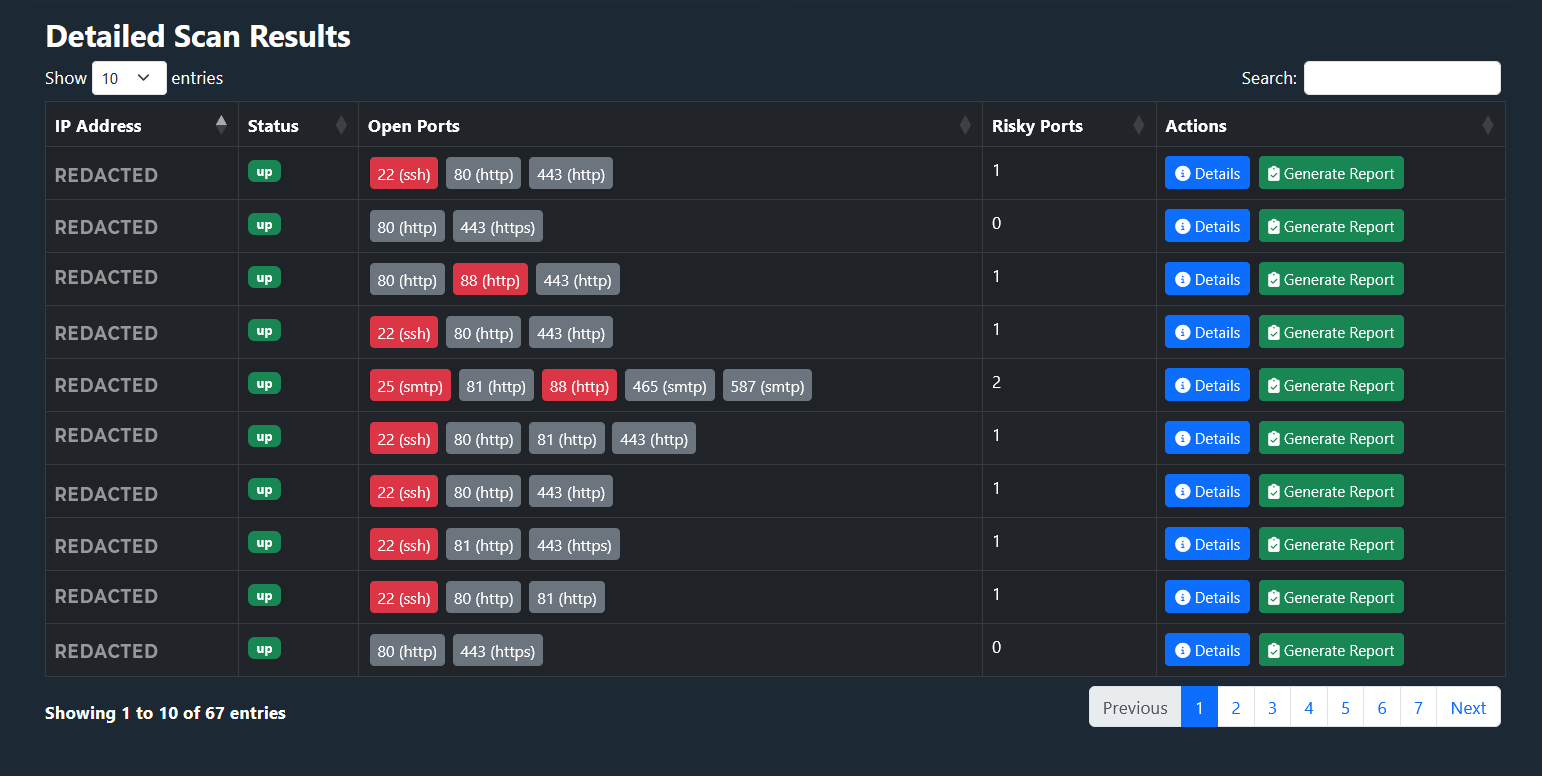
Now, if you’re thinking all of this sounds like a lot to manage—asset discovery, cloud misconfigurations, vendor risk, exposed credentials, and let’s not forget that random developer who left test code in production—you’re not wrong. Most companies end up stacking five or six tools just to keep up. That’s why TRaViS ASM was built differently.
TRaViS ASM doesn’t ask you to choose between visibility, control, or simplicity. It’s one unified platform that handles the most critical parts of Attack Surface Management so you can stop duct-taping tools together and start getting actual results.
Here’s how TRaViS handles the entire attack surface puzzle:
🔍 External ASM (EASM) Capabilities
- Internet-facing asset discovery – Finds domains, subdomains, servers, APIs, and forgotten cloud resources.
- API vulnerabilities & key exposure detection – Scans for exposed API keys, tokens, and vulnerable endpoints.
- Brand & domain monitoring – Alerts on mimic domains or brand abuse that may be used in phishing attacks.
- Dark web monitoring – Tracks stolen credentials or leaked data tied to your organization on the dark web.
☁️ Cloud ASM & Misconfiguration Management
- Cloud service exposure – Detects open storage buckets, unprotected interfaces, and public cloud misconfigurations.
- Misconfigured code detection – Scans your cloud-based assets and surfaces specific misconfigurations with suggested fixes.
- Continuous scanning – No agents. No manual triggers. Just nonstop analysis of your evolving cloud surface.
🧱 Internal ASM & Vulnerability Discovery
- Credential exposure alerts – Identifies exposed or reused credentials internally and externally.
- SAST/DAST integration – Pairs with your existing security tools to identify risks in both static code and dynamic environments.
- Prioritization engine – Ranks vulnerabilities using an algorithm that factors in exploitability, business impact, and asset sensitivity.
🤝 Third-Party & Supply Chain Exposure
- New asset detection – Instantly flags when a new system, domain, or vendor component becomes visible to attackers.
- External service exposure – Monitors and scores risks from third-party tools or connected platforms.
- Vendor-related credential leaks – Identifies credentials associated with third-party tools that appear in leaks or dark web sources.
🧠 All-In-One Dashboard (So You’re Not Juggling Ten Tools)
- One view to rule them all – See all findings, alerts, priorities, and recommendations in a clean, user-friendly interface.
- AI-powered remediation guidance – Get plain-English guidance on how to fix issues, down to the line of code or config.
- Customizable reporting – Build client-facing or executive-ready reports with your logo, or export detailed logs for audits.
- Flexible integrations – Works with the tools you already use (e.g., Slack, ticketing systems, possibly even ConnectWise).
⚙️ Developer & SMB-Friendly Extras
- Unlimited scans and seats – Whether you’re 5 people or 5,000, TRaViS doesn’t penalize growth.
- Lightweight setup – No complicated onboarding. No agents. Just results.
-
Affordable starting price – Begins at $99/month, making it accessible without sacrificing capability.
How to Choose the Right ASM Solution
.jpeg)
Faced with so many tools, how do you pick the one (or few) that fit your organization best? Consider these tips when evaluating Attack Surface Management solutions:
-
Know your focus area. Whether your organization is cloud-heavy (lots of AWS/Azure services, containers, etc.) or your main worry is external threats (phishing, rogue domains, etc.), TRaViS is designed to provide comprehensive visibility across your entire attack surface. It's built to adapt to your unique infrastructure, from cloud environments to external exposures, ensuring you have the targeted insights you need.
-
Consider third-party risk. If a big chunk of your risk comes from vendors and partners, TRaViS offers robust capabilities to extend your attack surface monitoring to third-party exposures. Gain valuable insights into the risks introduced by your supply chain, giving you a complete picture of your extended attack surface.
-
Think about breadth vs. depth. Do you need a comprehensive platform that covers external, internal, and cloud (an all-in-one ASM solution)? TRaViS delivers broad coverage across all these domains, providing a unified view of your attack surface. This eliminates the need for multiple disparate tools, streamlining your security operations with an integrated approach.
-
Integration and workflow. The best tool is one that plays nice with your current security stack. TRaViS is built for seamless integration with your existing SIEM, SOAR, or ITSM workflows. This ensures that discovered issues flow directly into your team’s existing processes, enhancing efficiency and reducing manual effort. Beyond just a platform, TRaViS is designed to act as a force multiplier for your security team, offering the kind of comprehensive visibility and actionable intelligence you need.
Key Consideration: Whichever vendor you consider, make sure it offers automated asset discovery, risk prioritization, and easy integration with your existing tools. This is precisely where TRaViS excels. Our goal is to reduce noise and highlight what matters most, acting as a true force multiplier for your security team, not just another noisy dashboard.
Closing Remarks

The bottom line? If you’re not actively managing your attack surface, you’re basically leaving the front door open for attackers — and maybe a few side doors and windows, too. In cybersecurity, visibility is non-negotiable; it truly is your first line of defense. All the firewalls, AI detectors, and incident response plans in the world won’t help if you never noticed the unlocked door in the first place.
The good news is that gaining this visibility across your attack surface is very achievable with the right approach and tools. By investing in attack surface management, you empower your security team to find and fix issues before they turn into full-blown incidents. It’s about taking back control of your sprawling digital ecosystem one asset at a time.
Ready to shine a light on all the shadowy corners of your IT landscape? TRaViS ASM is one example of a platform designed to do exactly that – helping you identify risks across your network, cloud, and beyond, so you’re never in the dark. Consider subscribing to our cybersecurity newsletter for more insights (and a few witty security tips) delivered to your inbox. And if you’re keen to see attack surface management in action, why not give TRaViS ASM a try? After all, when it comes to protecting your organization, seeing really is believing.