In today's hyper-connected world, the cost of a data breach is staggering. IBM's 2023 Cost of a Data Breach Report pegs the average cost at a whopping $4.45 million. However, organizations with mature threat intelligence programs experienced significantly lower costs, averaging $2.2 million less than those without. This dramatic difference underscores the critical importance of proactive threat intelligence, especially within the realm of External Attack Surface Management (EASM).
This article delves into the power of cybersecurity threat intelligence, exploring how it can be leveraged to proactively identify and mitigate vulnerabilities, reduce your attack surface, and ultimately, save your organization millions. We'll examine the key components of an effective threat intelligence strategy, including dark web monitoring, vulnerability management, and how a comprehensive EASM platform like TRaViS can provide the visibility and insights needed to stay ahead of emerging threats.
Understanding the Landscape: Why Threat Intelligence Matters for EASM

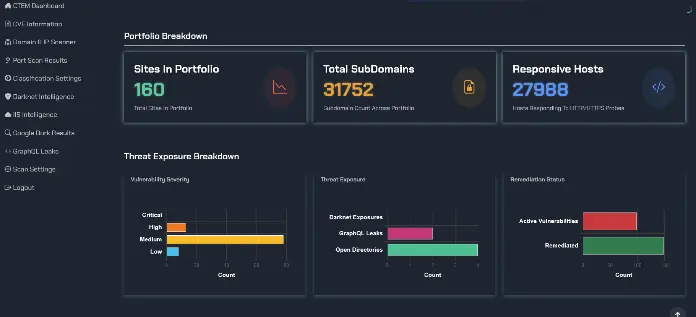
External Attack Surface Management (EASM) is all about understanding your organization's digital footprint from an attacker's perspective. It involves identifying all internet-facing assets, including websites, applications, cloud services, and network infrastructure. Without comprehensive visibility, vulnerabilities can remain hidden, creating entry points for malicious actors. This is where threat intelligence becomes invaluable.

Threat intelligence provides the context and insights needed to prioritize vulnerabilities and focus remediation efforts on the areas of greatest risk. It goes beyond simply identifying vulnerabilities; it helps you understand how those vulnerabilities are likely to be exploited, who is likely to exploit them, and what the potential impact could be. For example, knowing that a specific vulnerability is actively being exploited by a ransomware group targeting the healthcare sector allows a hospital's SOC team to prioritize patching that vulnerability immediately, potentially preventing a devastating ransomware attack. TRaViS provides continuous monitoring of your external attack surface, correlating identified assets with real-time threat intelligence feeds. This allows for proactive identification of vulnerabilities before they can be exploited.
Dark Web Monitoring: Uncovering Hidden Threats Before They Emerge
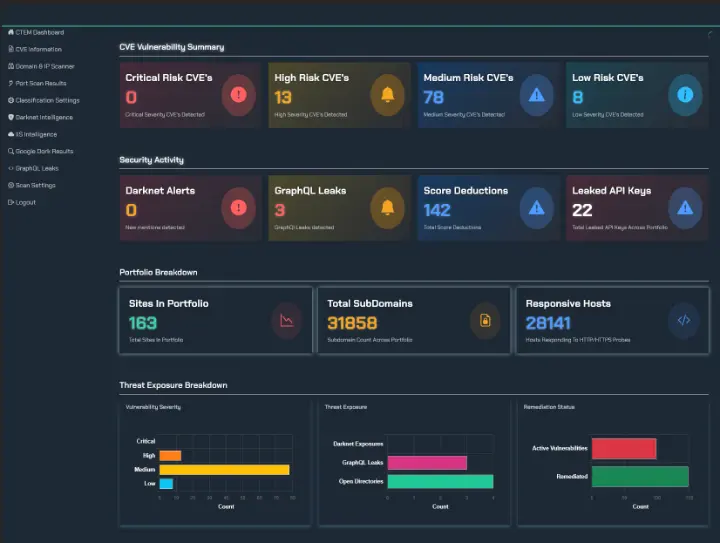
The dark web is a breeding ground for cybercriminals, where stolen data is bought and sold, attack plans are hatched, and emerging vulnerabilities are discussed. Monitoring the dark web is a crucial component of any robust threat intelligence program. By actively searching for mentions of your organization, its assets, or its employees, you can gain early warning of potential attacks.
Dark web monitoring can uncover a variety of threats, including:
- Compromised credentials: Usernames and passwords leaked in data breaches are often traded on the dark web. Identifying compromised credentials allows you to proactively reset passwords and prevent account takeover attacks.
- Data leaks: Sensitive data stolen from your organization may be offered for sale on dark web marketplaces. Detecting data leaks allows you to take steps to mitigate the damage and notify affected individuals.
- Attack planning: Cybercriminals may discuss their plans to target your organization on dark web forums. Identifying these discussions allows you to prepare your defenses and potentially disrupt the attack.
- Vulnerability exploitation: Discussions about exploiting specific vulnerabilities may appear on the dark web. This allows you to prioritize patching those vulnerabilities before they are exploited in the wild.
TRaViS integrates dark web monitoring capabilities, providing real-time alerts when your organization is mentioned on the dark web. This allows you to take immediate action to mitigate potential threats. For example, if TRaViS detects that employee credentials from your organization are being sold on a dark web marketplace, you can immediately reset those passwords and implement multi-factor authentication to prevent account takeover attacks.
Vulnerability Management: Prioritizing and Remediating Critical Weaknesses
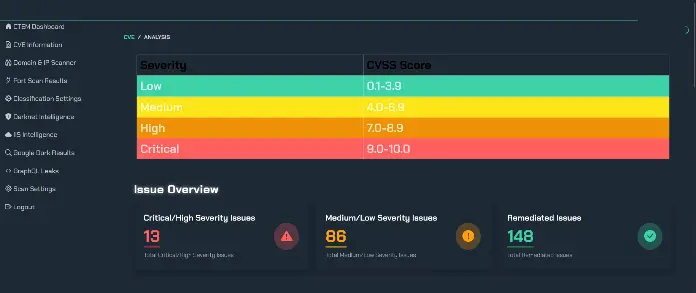
Vulnerability management is the process of identifying, assessing, and remediating vulnerabilities in your systems and applications. Threat intelligence plays a crucial role in prioritizing vulnerabilities and focusing remediation efforts on the areas of greatest risk. Not all vulnerabilities are created equal. Some vulnerabilities are more likely to be exploited than others, and some vulnerabilities have a greater potential impact on your organization.
Threat intelligence can help you prioritize vulnerabilities by providing information about:
- Exploitability: Is the vulnerability actively being exploited in the wild? Are there publicly available exploits?
- Severity: What is the potential impact of the vulnerability if it is exploited?
- Targeting: Is the vulnerability being targeted by specific threat actors?
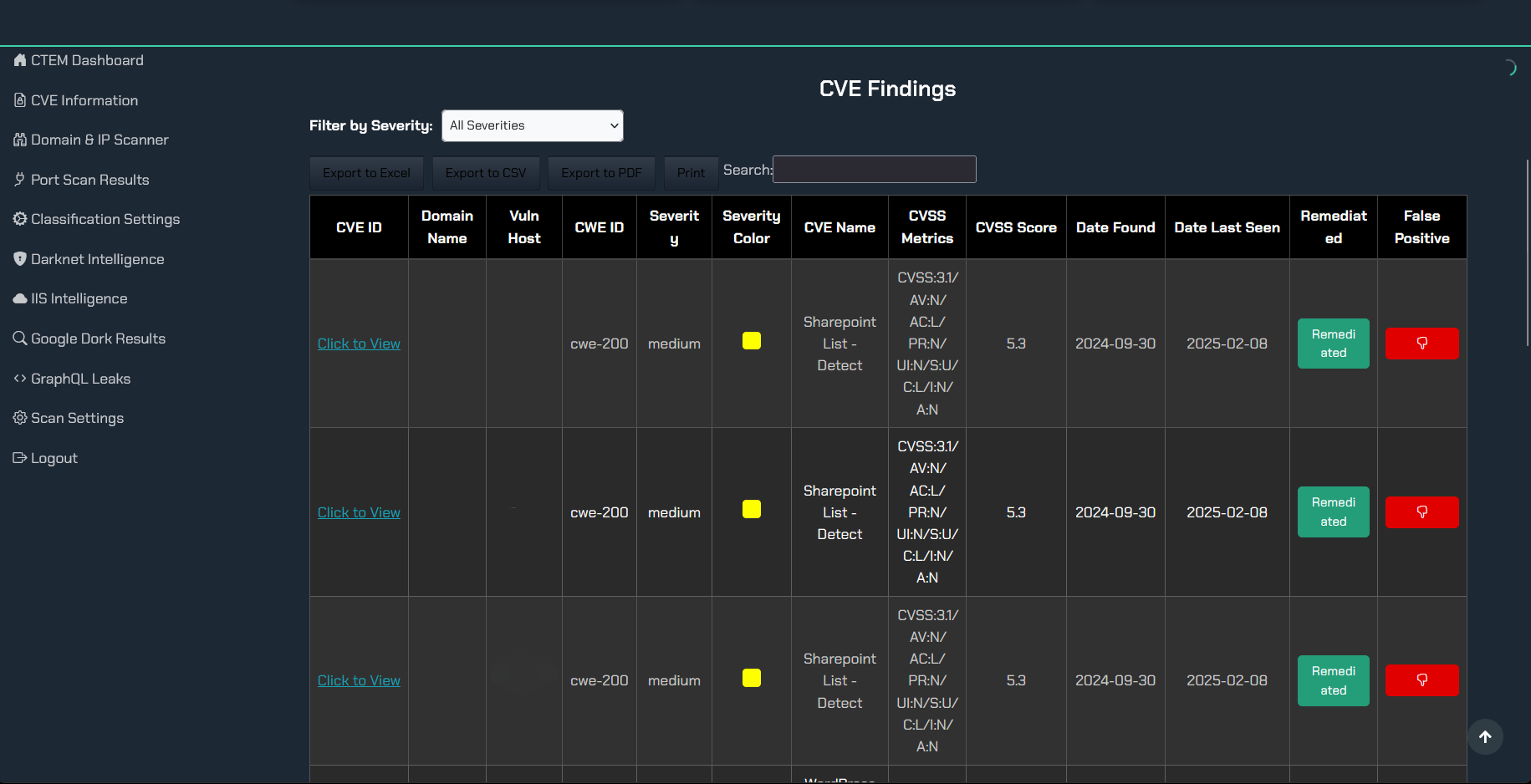
By combining vulnerability scanning with threat intelligence, you can focus your remediation efforts on the vulnerabilities that pose the greatest risk to your organization. For instance, TRaViS's vulnerability management capabilities, combined with its threat intelligence feeds, allow security teams to quickly identify and prioritize critical vulnerabilities that are actively being exploited. This ensures that limited resources are focused on the most pressing threats, reducing the overall risk exposure.
Consider a scenario where a critical vulnerability is discovered in a widely used web application framework. Without threat intelligence, a security team might treat this vulnerability as just another item on their patching list. However, with threat intelligence, they might learn that this vulnerability is actively being exploited by ransomware groups targeting financial institutions. This information would allow them to prioritize patching this vulnerability immediately, potentially preventing a devastating ransomware attack. TRaViS helps security teams stay ahead of these types of threats by providing real-time alerts about actively exploited vulnerabilities.
Building a Proactive Defense: Integrating Threat Intelligence with EASM

The true power of threat intelligence lies in its integration with other security tools and processes, particularly EASM. By combining threat intelligence with EASM, you can create a proactive defense that is constantly adapting to the evolving threat landscape.
Here's how:
- Automated Discovery and Assessment: EASM platforms like TRaViS automatically discover and assess your external attack surface, identifying all internet-facing assets and potential vulnerabilities. Integrating threat intelligence feeds into this process allows for automated prioritization of vulnerabilities based on real-time threat data.
- Proactive Remediation: Threat intelligence can be used to trigger automated remediation actions, such as patching vulnerable systems or blocking malicious IP addresses. This allows you to respond to threats quickly and effectively, even before they can cause damage.
- Improved Security Awareness: Threat intelligence can be used to educate employees about the latest threats and how to avoid becoming victims of cyberattacks. This helps to create a culture of security awareness throughout your organization.
- Enhanced Incident Response: Threat intelligence can be used to improve incident response by providing context about the attacker, their motives, and their tactics. This allows you to respond to incidents more effectively and minimize the damage.
For example, imagine a scenario where TRaViS identifies a new server exposed to the internet with a known vulnerability. Simultaneously, TRaViS's threat intelligence feed indicates that this vulnerability is being actively exploited by a botnet. The platform can automatically trigger a remediation action, such as isolating the server from the network, to prevent the botnet from compromising the system. This proactive approach significantly reduces the risk of a successful attack.
Managed Security Service Providers (MSSPs) can leverage TRaViS to provide enhanced threat intelligence services to their clients. By integrating TRaViS with their existing security tools and processes, MSSPs can offer proactive threat detection, vulnerability management, and incident response services, helping their clients to stay ahead of the evolving threat landscape.
Conclusion
Investing in cybersecurity threat intelligence is no longer a luxury; it's a necessity. The $2.2 million difference in data breach costs between organizations with and without mature threat intelligence programs speaks volumes. By integrating threat intelligence with your External Attack Surface Management (EASM) strategy, you can proactively identify and mitigate vulnerabilities, reduce your attack surface, and protect your organization from costly data breaches.
TRaViS offers a comprehensive AI Enhanced - EASM platform that seamlessly integrates threat intelligence, providing you with the visibility and insights needed to stay ahead of emerging threats.
From dark web monitoring to vulnerability management, TRaViS empowers security teams to proactively defend their organizations and reduce their risk exposure significantly.
Get Started
Ready to reduce your risk exposure and save millions? Schedule a demo of TRaViS today and discover how our AI-enhanced EASM platform can provide complete visibility into your external attack surface and help you proactively identify and remediate critical vulnerabilities.