Your Attack Surface is Bigger Than You Think. Here’s How to Handle It.
Let’s skip the pleasantries. You have assets connected to the internet that you don’t know about. It’s not a question of if, but how many. This ever-expanding digital footprint, your "attack surface," creates daunting challenges for even the most seasoned security teams. Proactively finding and neutralizing threats across this chaotic landscape isn't just a goal; it's the only way to stay ahead. This is the very problem External Attack Surface Management (EASM) was designed to solve.
Whether you're a CISO navigating budget meetings, a SOC analyst drowning in alerts, an ethical hacker probing for weaknesses, or an MSSP safeguarding clients, this guide will provide clarity. We'll delve into how a sophisticated EASM tool like TRaViS offers more than just another dashboard; it delivers comprehensive visibility, intelligent vulnerability prioritization, and a streamlined path to genuinely reducing your organization's risk exposure.
So, What is External Attack Surface Management (EASM), Really?
At its heart, External Attack Surface Management is the continuous process of discovering, analyzing, and securing your organization’s entire external-facing digital footprint. This includes all the internet-facing assets that an attacker could potentially target—websites, APIs, cloud services, network infrastructure, you name it. The crucial difference from traditional security measures lies in its perspective. EASM adopts an "outside-in" view, effectively seeing your organization through the eyes of an adversary. And what a difference that perspective makes.
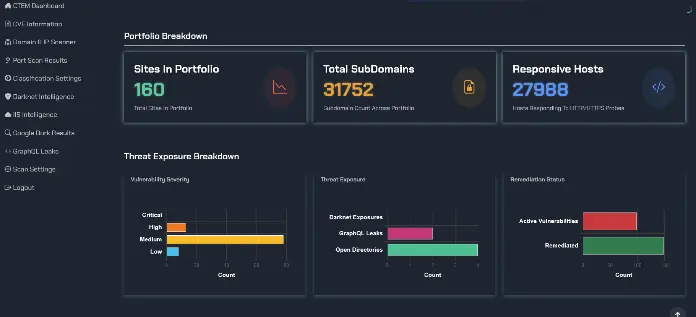
A truly effective EASM strategy is a dynamic, ongoing cycle. It begins with relentless Asset Discovery, hunting down not just your known, sanctioned assets, but also the forgotten servers and unsanctioned cloud instances known as "shadow IT." This isn't a trivial matter; in fact, a recent report from Gartner highlights that attack surface expansion is a major trend, with organizations often blind to significant portions of their exposure.
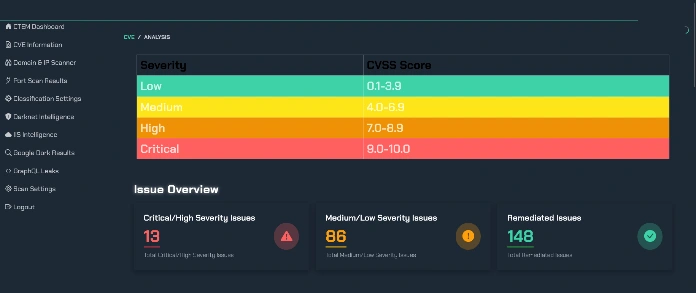
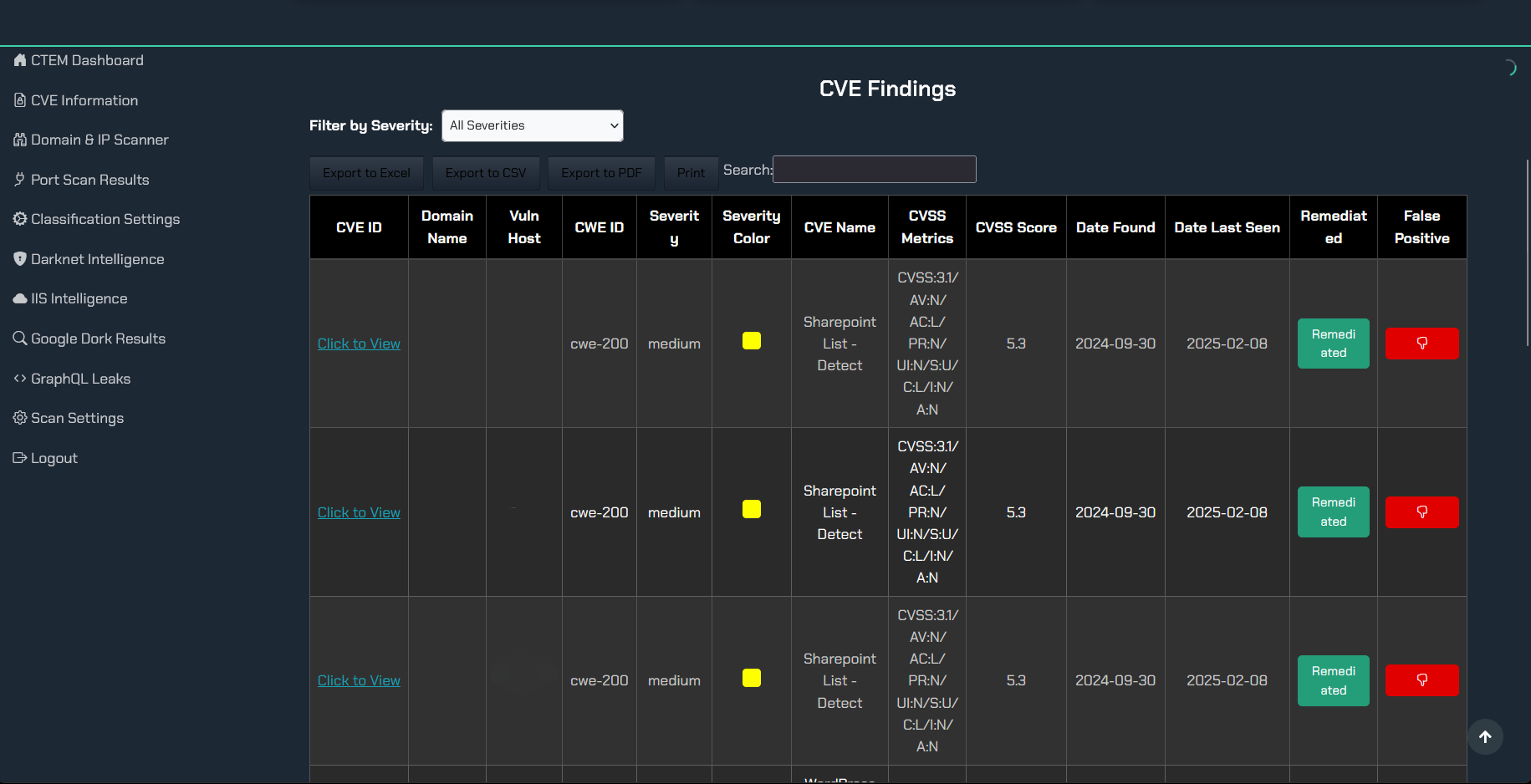
Once an asset is found, it undergoes a rigorous Vulnerability Assessment to unearth security weaknesses, from critical misconfigurations to outdated software. But a simple list of flaws is just noise. The magic happens with Risk Prioritization. By analyzing the potential business impact and the real-world exploitability of each vulnerability, EASM helps you focus your remediation efforts where they count. All of this is underpinned by Continuous Monitoring, because your attack surface changes daily. It's this proactive, holistic approach that provides clear, Remediation Guidance to systematically shrink your exposure.
Consider a financial institution that uses TRaViS and discovers a forgotten subdomain running an old, vulnerable web application. The platform immediately flags several critical flaws, enabling the security team to patch the system before it becomes the source of a headline-making data breach. Without that outside-in EASM perspective, would that vulnerability have ever been found?
Why Traditional Vulnerability Tools Are No Longer Enough

For years, security teams have relied on traditional vulnerability management solutions, and they certainly have their place. However, in the face of modern, distributed environments, these tools often provide a dangerously incomplete picture. Their fundamental limitation is that they were built to look inward, scanning known assets within the corporate network, which leaves massive blind spots.
The shortcomings of these legacy approaches are clear. They typically have a limited scope, blissfully unaware of the shadow IT and external-facing resources that EASM is built to find. They often lack business context, flagging a low-impact vulnerability with the same urgency as a critical one on a payment server. This, coupled with often manual processes and a fundamentally reactive posture, means teams are often finding problems long after an attacker could have. Let's not even get started on the integration challenges that leave security stacks feeling more like a collection of disjointed silos than a cohesive defense system.
EASM was born from these limitations. It doesn't replace internal vulnerability management; it complements it by providing that missing, all-important external view. A healthcare provider, for example, might diligently run internal scans that give its network a clean bill of health. Yet, those scans would completely miss a misconfigured cloud storage bucket leaking sensitive patient data. It's an EASM platform like TRaViS that would spot that external exposure from an attacker's point of view, preventing a potential HIPAA violation and a devastating breach. This distinction is so crucial that government agencies like CISA publish guidance that implicitly underscores the need for a comprehensive view beyond traditional scanning.
A Practical Guide to Implementing EASM
Rolling out an EASM program doesn't have to be a monumental undertaking. It’s a strategic process that, when done correctly, delivers immediate value.
Your journey should begin by defining a scope, but start small and smart. Focus on your most critical business assets first, then gradually expand your program's reach. The next logical step is to choose the right EASM tool. You need a platform whose capabilities align with your needs—look for robust asset discovery, high-fidelity vulnerability assessment, and intelligent risk prioritization. A solution like the TRaViS platform, with its proactive, AI-enhanced engine, is designed to provide that complete visibility and help teams pinpoint critical vulnerabilities from day one.
Once your tool is in place, you’ll configure asset discovery by providing seed domains and other known starting points, then let it loose to map your true footprint. From there, you will run assessments and, most importantly, prioritize vulnerabilities based on actual risk, not just a raw severity score. This allows you to orchestrate remediation efficiently.
The real power, however, comes from making this a continuous loop. Continuously monitor your attack surface for changes and automate as much of the process as possible to improve efficiency and reduce human error. Finally, integrate your EASM tool with your existing security ecosystem—your SIEM, SOAR, and ticketing systems—to ensure that its insights are not just interesting, but actionable. A great example is an e-commerce company that uses TRaViS to automate its EASM program. By integrating it with their ticketing system, newly discovered critical vulnerabilities are automatically assigned to the right development team, with remediation progress tracked seamlessly.
The Tangible Benefits of a True EASM Platform like TRaViS
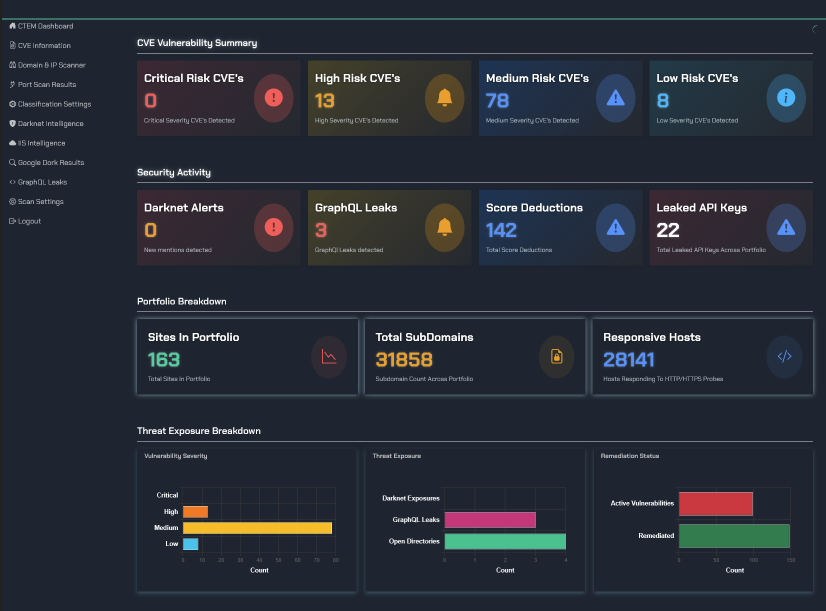
Investing in a dedicated EASM tool isn't just about ticking a compliance box; it's about generating tangible security outcomes. A proactive, AI-enhanced platform like TRaViS delivers a suite of benefits that directly strengthen your defensive posture and, frankly, make your life easier.
The primary advantage is achieving complete visibility. TRaViS is engineered to discover every external-facing asset, obliterating the blind spots created by shadow IT. This leads directly to proactive vulnerability identification, as the platform continuously scans for weaknesses and misconfigurations, allowing you to fix them before they can be exploited. But it doesn't just find problems; its AI-enhanced analysis prioritizes them based on genuine risk, ensuring your team isn't wasting time on trivialities. This is critical, as a 2024 analysis by Forbes points out that the sheer volume of data makes intelligent filtering a necessity. The platform then provides automated remediation guidance and seamlessly integrates with your existing workflows to streamline the entire process from detection to resolution.
This translates into specific advantages for everyone on the team:
- For CISOs: It provides a comprehensive, board-ready view of the organization's true risk exposure and security posture.
- For SOC Teams: It enables a shift from reactive firefighting to proactive vulnerability remediation, drastically reducing the likelihood of major incidents.
- For Ethical Hackers: It serves as a powerful reconnaissance tool to discover hidden assets and map potential attack vectors for testing.
- For MSSPs: It allows you to offer a premium, comprehensive EASM service that provides demonstrable value and security to your clients.
Conclusion
External Attack Surface Management is no longer a luxury for the paranoid; it is an indispensable pillar of any modern cybersecurity strategy. Gaining total visibility of your external assets, proactively identifying the flaws that matter, and intelligently prioritizing your response is the only sustainable way to reduce risk in the face of constant change. An AI-enhanced EASM tool like TRaViS gives you the power to discover and remediate the critical vulnerabilities that other tools were never designed to see. In today's threat landscape, investing in EASM is one of the most strategic decisions you can make to protect your organization.
Get Started
Ready to finally see your entire external attack surface? Sign up for a free demo of TRaViS today and discover how our AI-enhanced EASM platform can help you identify and remediate critical vulnerabilities before they are exploited.