Businesses are constantly seeking ways to streamline operations and boost productivity. However, this drive for efficiency has given rise to a phenomenon that's keeping IT professionals up at night: Shadow IT. This seemingly innocuous term refers to the use of unauthorized or undocumented assets outside the oversight of the IT team, and it's rapidly becoming one of the most significant security risks facing organizations today.
But what exactly is Shadow IT, and why should you be concerned? Let's dive deep into this digital underworld and uncover the potential dangers lurking in the shadows of your company's tech infrastructure.
Understanding Shadow IT
.jpeg?access_token=a5bf63a6-0462-4f21-8493-f12e715fb56d)
Shadow IT refers to any technology, software, or hardware that employees use without the knowledge or approval of the IT department. This can include everything from cloud-based productivity tools and file-sharing services to personal devices used for work purposes. While these unofficial solutions may seem harmless or even beneficial at first glance, they can open up a Pandora's box of security vulnerabilities.
The Rise of Shadow IT
The proliferation of Shadow IT is not a new phenomenon, but it has accelerated dramatically in recent years. Several factors have contributed to this trend:
- Cloud-based services: The ease of accessing and implementing cloud-based solutions has made it simpler for employees to adopt new tools without IT involvement.
- Remote work: The shift to remote and hybrid work models has increased the need for flexible, accessible tools, leading many employees to seek out their own solutions.
- Bring Your Own Device (BYOD) policies: As more companies allow employees to use personal devices for work, the line between authorized and unauthorized technology becomes blurred.
- Desire for efficiency: Employees often turn to Shadow IT when they feel that official tools are inadequate or too slow to implement.
- Lack of awareness: Many employees simply don't understand the security implications of using unauthorized tools or services.
The Hidden Dangers of Shadow IT
.jpeg?access_token=411294ad-d8ab-492c-8eee-3961a676bfcb)
While Shadow IT may seem like a harmless way for employees to boost productivity, it poses several significant risks to your organization:
- Data breaches: Unauthorized applications and services may not meet your company's security standards, potentially exposing sensitive data to cyber threats.
- Compliance violations: Many industries have strict regulations regarding data handling and storage. Shadow IT can lead to inadvertent violations of these regulations, resulting in hefty fines and legal consequences.
- Loss of control: When employees use unauthorized tools, IT teams lose visibility and control over company data, making it difficult to protect and manage information effectively.
- Inefficiency and redundancy: Multiple employees or departments may unknowingly adopt different solutions for the same problem, leading to inefficiencies and unnecessary costs.
- Integration issues: Unauthorized tools may not integrate well with official systems, causing data silos and hindering collaboration.
- Malware and ransomware risks: Unsanctioned applications may not receive regular security updates, making them vulnerable to malware and ransomware attacks.
Real-World Consequences
.jpeg?access_token=1af394c1-5a06-41b7-8039-1608ae1acb35)
The dangers of Shadow IT aren't just theoretical. Numerous organizations have faced severe consequences due to unauthorized technology use. For example:
1. Financial Institution Using Unauthorized Messaging Apps (2019)
- Employees at major financial institutions, including Bank of America and Citigroup, used unauthorized messaging platforms like WhatsApp to discuss sensitive business matters. This resulted in regulatory violations and fines totaling $1.8 billion imposed by the SEC and CFTC for non-compliance with record-keeping requirements
2. HIPAA Violation in Healthcare
- A healthcare provider faced significant penalties after employees used personal email accounts to send patient data, violating HIPAA regulations. Common violations include emailing protected health information (PHI) without encryption or using non-compliant email services, which can lead to fines and corrective action plans
3. Tech Company Data Breach via Personal Cloud Storage
-
A tech company suffered a data breach when an employee's
personal cloud storage account, used for work purposes, was
compromised. This incident highlights the risks of unapproved tools like
personal OneDrive accounts being used for sensitive company data
These examples demonstrate how Shadow IT can lead to regulatory fines, compliance failures, and data breaches across industries.
Strategies for Addressing Shadow IT
While completely eliminating Shadow IT may be unrealistic, there are several strategies organizations can employ to mitigate its risks:

Conduct regular audits:
Implement tools and processes to regularly scan your network for unauthorized applications and devices.

Educate
employees:
Raise awareness about the risks of Shadow IT and provide training on proper technology use and security protocols.

Improve
communication:
Promote dialogue between IT and other teams to address user needs and prevent unauthorized solutions.

Set up an approval process:
Create a streamlined process for employees to request and receive approval for new tools and technologies.

Adopt a flexible IT strategy:
Be open to evaluating and adopting new technologies that meet employee needs while maintaining security standards.

Use monitoring tools:
Implement solutions that can detect and alert IT teams to the use of unauthorized applications or services.

Offer
alternatives:
Provide officially sanctioned alternatives to popular Shadow IT tools to meet employee needs within a secure environment.

Create clear
policies:
Develop and communicate clear guidelines on the use of personal devices and cloud services for work purposes.
The Role of EASM in Combating Shadow IT

External Attack Surface Management (EASM) platforms like TRaViS can play a crucial role in identifying and mitigating the risks associated with Shadow IT. Here's how:
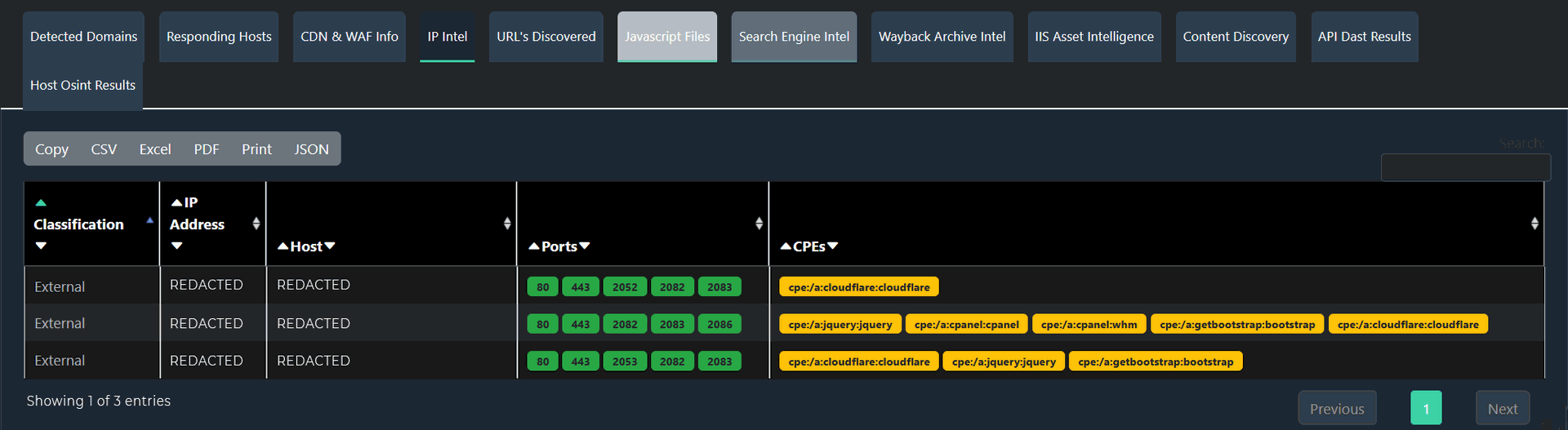
Comprehensive asset discovery:
EASM solutions can continuously scan and identify all internet-facing assets associated with your organization, including those that may have been implemented without IT approval.
Vulnerability detection:
By regularly assessing your external attack surface, EASM tools can identify potential vulnerabilities in both authorized and unauthorized assets.
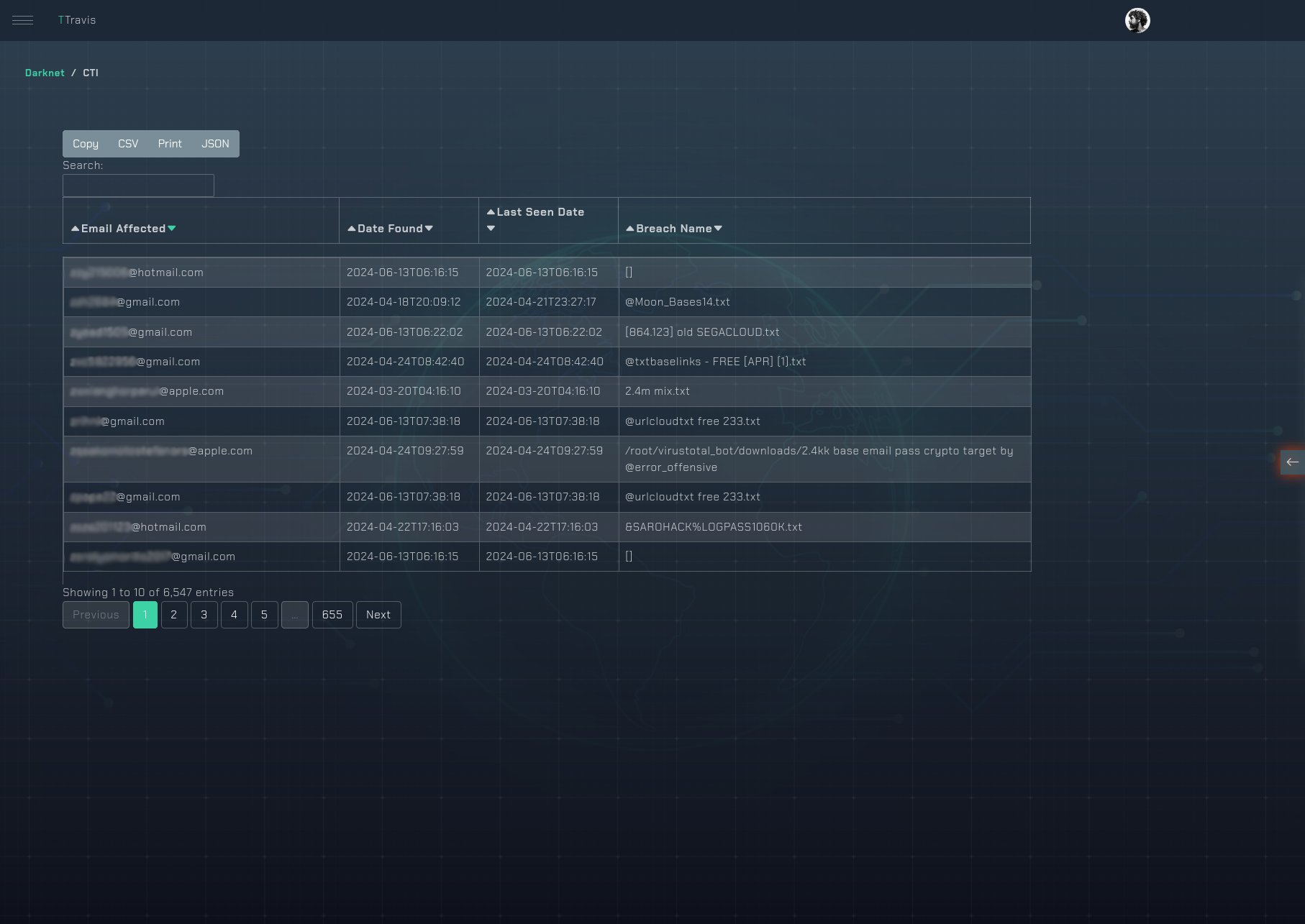
Dark web monitoring:
Some EASM platforms, including TRaViS, offer dark web scanning capabilities, which can help detect if any company data has been exposed through unauthorized channels.
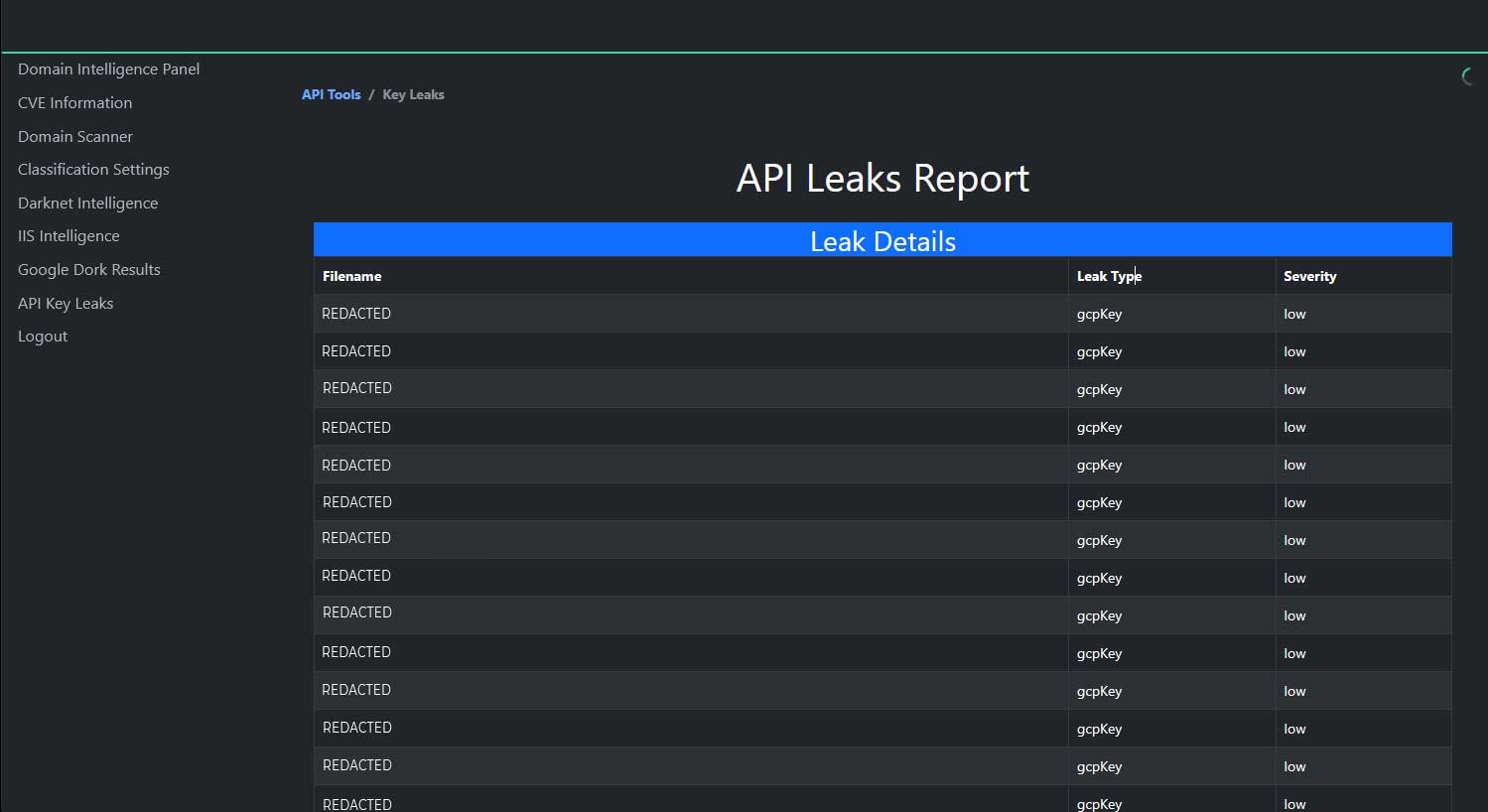
API key detection:
EASM solutions can identify exposed API keys, which are often a result of Shadow IT practices and can lead to significant security breaches if left unchecked.
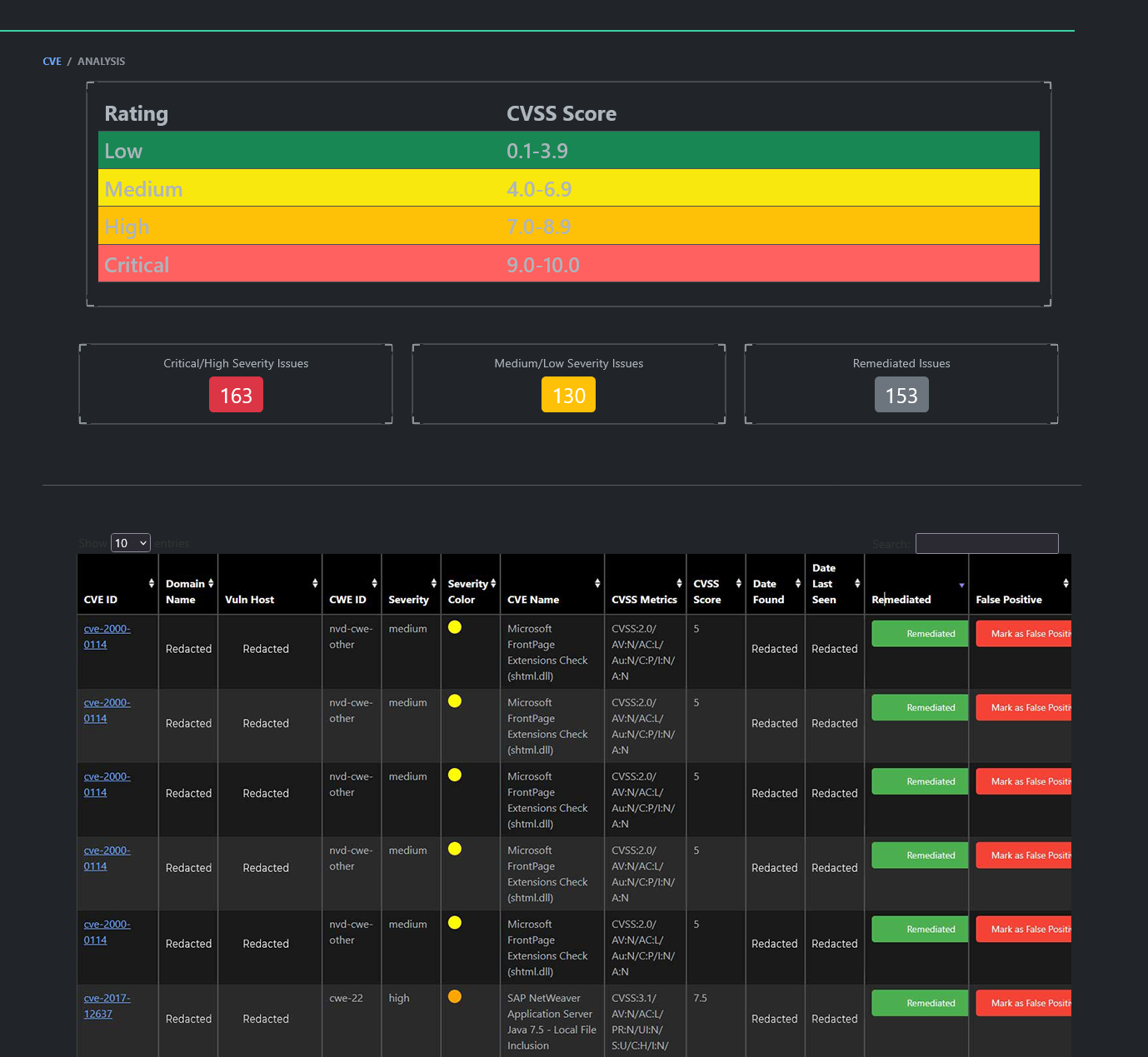
Continuous monitoring:
The continuous monitoring capabilities of EASM platforms ensure that new Shadow IT assets are quickly identified and assessed for potential risks.
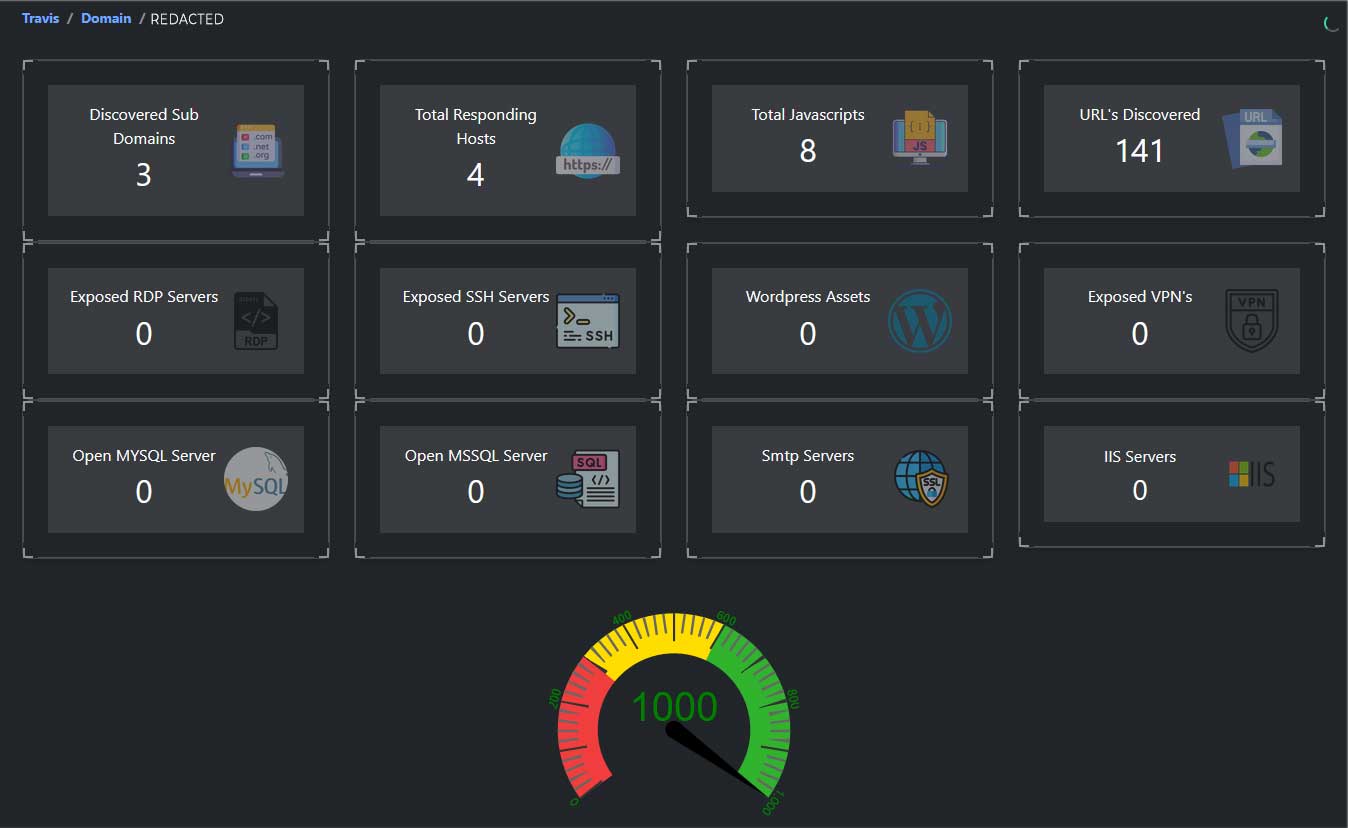
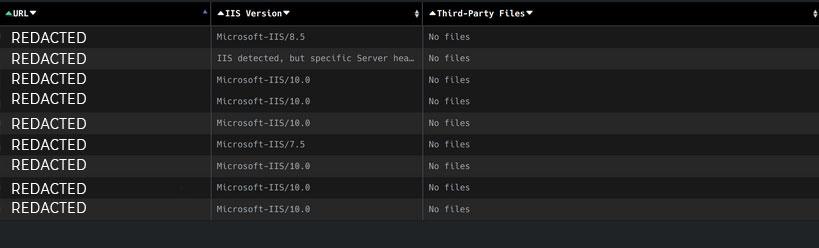
Integration with existing security tools:
EASM solutions can integrate with your existing security infrastructure, providing a more comprehensive view of your organization's security posture.
By leveraging EASM tools like TRaViS, organizations can gain better visibility into their entire IT ecosystem, including Shadow IT elements, and take proactive steps to mitigate associated risks.
Embracing a Collaborative Approach
.jpeg?access_token=7d7def70-8fc7-4adc-a27c-a87f125127d8)
While the risks of Shadow IT are significant, it's important to recognize that its prevalence often stems from legitimate employee needs and desires for efficiency. Rather than adopting a purely restrictive approach, organizations should strive to create an environment where IT and other departments work collaboratively to meet business needs securely.
This collaborative approach might include:
- Regular feedback sessions between IT and other departments to discuss technology needs and challenges.
- Involving end-users in the evaluation and selection of new tools and technologies.
- Creating a culture of innovation that encourages employees to bring new ideas and solutions to the IT team.
- Implementing a "sandbox" environment where employees can safely test new tools before they're approved for wider use.
- Offering incentives for employees who identify and report potential Shadow IT risks.
By fostering this type of collaborative environment, organizations can harness the innovative spirit that often drives Shadow IT while maintaining the necessary security controls.
The Future of Shadow IT

As technology continues to evolve at a rapid pace, the challenge of Shadow IT is likely to persist. However, emerging trends and technologies may help organizations better manage this risk:
- AI and machine learning: Advanced AI algorithms can help detect anomalous behavior and unauthorized tool usage more effectively.
- Zero Trust architectures: This security model, which assumes no user or device is trustworthy by default, can help mitigate the risks associated with Shadow IT.
- Unified endpoint management: As the lines between personal and work devices blur, unified endpoint management solutions will become increasingly important in managing and securing all devices accessing corporate resources.
- Cloud access security brokers (CASBs): These tools can provide visibility and control over cloud service usage, helping to manage Shadow IT in cloud environments.
- Security orchestration, automation, and response (SOAR): SOAR platforms can help automate the detection and response to Shadow IT risks, improving efficiency and reducing response times.
Wrapping It Up
.jpeg?access_token=e0bda64f-d2ea-41ca-87b6-f7b4822e61d2)
Shadow IT represents a significant and growing challenge for organizations of all sizes. While it often arises from employees' desire to work more efficiently, the security risks it poses cannot be ignored. By understanding the drivers behind Shadow IT, implementing comprehensive detection and management strategies, and fostering a collaborative approach to technology adoption, organizations can harness the innovative potential of their workforce while maintaining a robust security posture.
Remember, the key to effectively managing Shadow IT lies not in eliminating it entirely, but in bringing it out of the shadows and into the light of proper oversight and security. By leveraging advanced tools like EASM platforms and adopting a proactive, collaborative approach to technology management, organizations can turn the potential threat of Shadow IT into an opportunity for innovation and growth.
Staying ahead of security threats requires vigilance, adaptability, and a willingness to embrace new solutions. By addressing the challenge of Shadow IT head-on, you can ensure that your organization remains secure, compliant, and ready to face the technological challenges of tomorrow.
Book a Demo
See how TRaViS can help mitigate some of these issues.