You know, it’s truly astonishing how many organizations operate with a silent, stealthy saboteur lurking within their digital walls: Shadow IT. We're talking about the unsanctioned hardware, rogue software, and clandestine cloud services employees spin up without so much as a nod to the IT department. While it might seem like harmless resourcefulness on the surface, make no mistake—this digital freelancing carves out a massive blind spot in your organization's attack surface, often accounting for a staggering 99% of the risks security teams remain blissfully unaware of. If that doesn't make your eye twitch, perhaps you're in the wrong line of work. This hidden infrastructure, my friends, is a direct highway to critical vulnerabilities, devastating data breaches, thorny compliance violations, and, naturally, some rather significant financial hemorrhaging.
So, let's pull back the curtain on this pervasive problem, shall we? This isn't just a casual stroll; we’re diving deep into the alarming proliferation of Shadow IT, dissecting its inherent dangers, and, most critically, unveiling how cutting-edge External Attack Surface Management (EASM) solutions—like our very own TRaViS—are nothing short of a godsend for CISOs, SOC teams, ethical hackers, and MSSPs desperate to reclaim dominion over their sprawling digital footprint. We’ll expose the secrets to unearthing these elusive assets, meticulously assessing their inherent risk, and crafting bulletproof strategies to defuse the ticking time bombs they represent, all in the noble pursuit of a more secure and resilient enterprise.
The Elephant in the Room: Unpacking Shadow IT's Alarming Reach

It’s often said that ignorance is bliss, but in cybersecurity, it's more like a one-way ticket to a very public and utterly embarrassing incident. Shadow IT, frankly, is far more deeply ingrained than most organizations are willing to admit. Think about it: conventional wisdom suggests companies possess visibility into merely a fraction of their actual IT assets. The colossal bulk of this "dark" infrastructure—often a bewildering menagerie of unapproved cloud applications, phantom servers, and unmanaged devices—serves as an exquisite breeding ground for security vulnerabilities. And just in case you thought this was merely a quaint problem for the mom-and-pop shop down the street, wake up! Large enterprises, with their labyrinthine decentralized operations and impossibly diverse technology stacks, are particularly vulnerable. It's almost as if the more moving parts you have, the more opportunities there are for things to go wildly, wonderfully wrong.
Imagine, if you will, a scenario: a marketing team, bless their creative hearts, decides to circumvent official channels, opting for an unapproved cloud storage service to share their latest campaign masterpieces. This service, charming as it may be, quite likely lacks the ironclad security controls of your organization's meticulously vetted platform, inadvertently exposing sensitive customer data for all the digital world to see. Or perhaps a sales team, eager to hit their quotas, adopts a shiny new CRM tool without a whisper to IT, leading to a cascade of compliance nightmares and potential data leakage. Multiply these seemingly isolated acts of "ingenuity" across every department, every satellite office, and what you get is a gargantuan, intricate web of Shadow IT, dramatically inflating your attack surface. It’s like discovering your house has a dozen extra doors you didn’t know about, all unlocked, and leading to your most prized possessions.
For CISOs, the sheer magnitude of the Shadow IT predicament is, quite rightly, a source of constant low-grade anxiety. Without comprehensive visibility, how does one even begin to accurately assess risk, judiciously prioritize security expenditures, or, dare I say, enforce anything resembling consistent security policies? This palpable lack of control inevitably leads to a delightful array of consequences:
- Elevated Vulnerability to Cyberattacks: Unpatched software, passwords so weak they're practically an open invitation, and misconfigured systems are, shall we say, a common staple in these Shadow IT enclaves. It’s a buffet for threat actors, really.
- Data Breaches and Compliance Calamities: Sensitive data, when unceremoniously dumped in unapproved digital nooks, faces an exponentially greater risk of exposure and, naturally, a swift violation of stringent regulations like HIPAA, PCI DSS, and GDPR. Because who needs peace of mind when you can have a regulatory fine?
- Resources Down the Drain: Redundant IT spending and gloriously inefficient resource allocation are almost guaranteed byproducts of unchecked Shadow IT. It’s like paying for three streaming services when you only watch one, but with exponentially higher stakes.
- Operational Headaches: The glaring lack of integration between these clandestine Shadow IT systems and your meticulously approved IT infrastructure can cripple collaboration and throw a wrench into productivity. It's truly a marvel to behold.
The Plot Thickens: Why Shadow IT Isn't Going Anywhere Soon

To genuinely wrestle Shadow IT into submission, one must first grasp the underlying forces propelling its relentless expansion. It’s not just a random act of defiance; several potent factors fuel this digital free-for-all. And no, it’s not always pure malice or incompetence; sometimes, it’s simply the path of least resistance.
Let's be real, the sheer ease of access to cloud services is a major culprit. The world is awash with ridiculously affordable, ridiculously user-friendly cloud applications, making it child’s play for employees to bypass the IT gatekeepers and procure their own bespoke solutions. Think Google Workspace, Dropbox, or Slack – all fantastic tools, but when adopted without formal approval, they become a security blind spot the size of a small moon. Then there’s the notorious "perceived IT bottlenecks." Employees, with their inherent need for speed and efficiency, often resort to Shadow IT when they feel the IT department is moving at the pace of continental drift, unresponsive to their urgent demands, or simply too rigid with their tech standards. When legitimate processes are seen as cumbersome, alternative, less secure routes magically appear.
And speaking of a lack of understanding, a significant portion of this problem stems from a simple lack of awareness and proper training. Many employees are blissfully oblivious to the inherent security risks woven into the fabric of Shadow IT. They genuinely might not grasp the profound importance of sticking to approved tools or diligently following established security protocols. It’s not malice; it's just, well, a profound lack of enlightenment. Add to this the trend of decentralized decision-making within organizations, where individual departments or teams possess the autonomy to handpick their own technology solutions, leading inevitably to a fragmented, disparate IT landscape. It’s like every team getting to design their own section of a puzzle; eventually, the pieces just don't fit.
And then, as if we needed more fuel for the fire, came the rise of remote work. The rapid, often chaotic, pivot to employees working from anywhere and everywhere has undeniably turbocharged the growth of Shadow IT. Employees, often relying on personal devices and a patchwork of unapproved applications to get their jobs done, inadvertently amplify the risk of data breaches and nasty security incidents. It’s a brave new world, and sometimes, it’s also a rather insecure one.
Tackling these deeply rooted causes demands a nuanced, multi-faceted approach, one that looks beyond mere prohibition:
- Streamlining IT Procurement: Make it genuinely easier, and crucially, faster, for employees to legitimately acquire approved technology solutions. Because if it's too hard to do it right, they'll just do it their own way.
- Improving IT Responsiveness: Respond to user needs with alacrity and efficacy. Prove that IT isn't just a cost center but a responsive enabler of business.
- Comprehensive Security Awareness Training: Educate, enlighten, and empower employees about the very real dangers of Shadow IT and the indispensable value of adhering to security policies. Ignorance, in this case, is definitely not bliss.
- Establishing Crystal-Clear Technology Standards: Define, with unambiguous clarity, which technology solutions are approved and what the guidelines for their usage are. Ambiguity is the enemy of security.
- Implementing Robust Security Controls: Don't just talk the talk; enforce security policies with conviction and diligently monitor for any unauthorized IT activity. A bit of digital policing goes a long way.
Your Digital Bloodhound: How TRaViS Unleashes EASM to Hunt Down Shadow IT
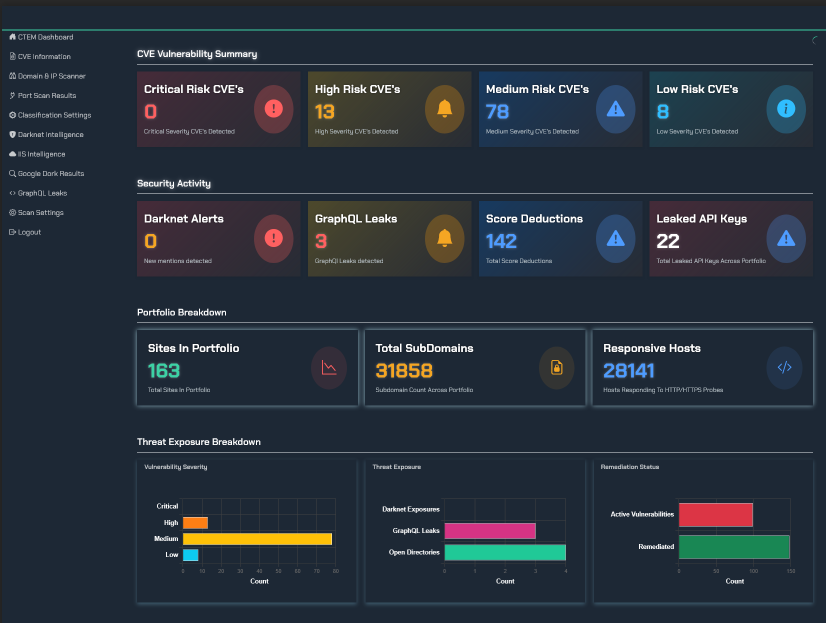
This is where the magic, or rather, the meticulous science of External Attack Surface Management (EASM) truly shines, offering a potent, systematic approach to unearthing and wrangling Shadow IT. EASM solutions are the tireless sentinels, perpetually scanning an organization's external-facing digital assets, meticulously pinpointing vulnerabilities and potential attack vectors that, more often than not, lie cunningly concealed within the very fabric of Shadow IT infrastructure. And when it comes to comprehensive Shadow IT discovery, TRaViS, our proactive, AI-enhanced EASM platform, stands in a league of its own.
How does TRaViS manage this impressive feat, you ask? Well, it's a symphony of cutting-edge capabilities:
- Automated Asset Discovery: TRaViS is the digital equivalent of a bloodhound with a supercomputer brain. It automatically sniffs out every single internet-facing asset tethered to your organization, from sprawling websites and intricate applications to ephemeral cloud services and foundational network infrastructure. This isn't just about what you think you have; it’s about revealing everything, including those assets that have conveniently sidestepped official documentation or IT department management.
- Advanced Scanning Techniques: It employs a veritable arsenal of sophisticated scanning techniques designed to pinpoint vulnerabilities and misconfigurations hiding within those Shadow IT assets. This includes the mundane yet critical—detecting unpatched software and embarrassingly weak passwords—all the way to the more alarming—uncovering overtly exposed data.
- Threat Intelligence Integration: TRaViS doesn't just discover; it anticipates. By seamlessly integrating with the latest threat intelligence feeds, it identifies nascent threats specifically targeting Shadow IT assets. This empowers your security teams to preemptively address vulnerabilities long before some less scrupulous individual decides to exploit them. It’s like having a crystal ball, but for cybersecurity.
- Risk Prioritization, Because Not All Fires Are Equal: In the chaotic world of cybersecurity, not every vulnerability demands immediate, hair-on-fire attention. TRaViS intelligently prioritizes risks, assessing their severity and potential blast radius on your organization. This is a game-changer, allowing security teams to channel their finite energies and resources toward the most critical vulnerabilities, ensuring maximum impact with minimum fuss.
- Continuous Monitoring: The Vigilant Watcher: Our digital landscape is a constantly shifting beast. TRaViS acts as a tireless, continuous monitor of your external attack surface, perpetually scanning for newly emergent Shadow IT assets and evolving threats. This guarantees your security teams are perpetually abreast of the very latest risks, preventing any unpleasant surprises.
By casting such an all-encompassing net of visibility over the external attack surface, TRaViS empowers organizations to do something truly revolutionary:
- Identify and eliminate Shadow IT assets: It's about discovering and then systematically excising those unauthorized hardware pieces, software installations, and cloud services that are acting as digital freeloaders.
- Decimate the risk of data breaches: Imagine the peace of mind knowing that sensitive data, previously marooned in precarious Shadow IT environments, is now actively protected.
- Elevate compliance: Ensuring that every single IT asset, sanctioned or otherwise, meticulously adheres to relevant regulatory mandates. Because auditors, bless their hearts, love compliance.
- Optimize security spending: Stop throwing darts blindfolded. TRaViS helps you channel your security resources precisely where they’ll make the most tangible impact, on the vulnerabilities that truly matter.
For a tangible example, picture this: TRaViS flags a rogue cloud server, innocently hosting sensitive customer data, inadvertently spun up by a well-meaning but woefully unsupervised developer. By detecting this rather significant Shadow IT asset, TRaViS hands your organization the power to swoop in, secure the server with immediate prejudice, and avert a potentially catastrophic data breach. Or, consider another scenario: TRaViS flags an outdated WordPress installation, quietly humming along on some long-forgotten subdomain—a veritable open invitation for known exploits. TRaViS doesn't just point out the ancient software; it delivers precise remediation steps, allowing you to patch that gaping vulnerability with remarkable alacrity. It’s like having your own expert forensic team, but on speed dial, 24/7.
Charting the Course: Crafting a Bulletproof Shadow IT Management Strategy
Now, discovering Shadow IT is, to be perfectly blunt, merely the opening act. To truly master this lurking risk, organizations must meticulously construct and implement a holistic Shadow IT management strategy. This isn't a suggestion; it’s an absolute imperative. And this strategy, should you choose to accept it, must encompass the following critical elements:
- Establish Unambiguous Policies and Procedures:
Begin by drafting, disseminating, and rigorously enforcing crystal-clear policies and procedures governing all technological usage within the organization. These guidelines must explicitly delineate approved technology solutions, meticulous usage guidelines, and unwavering security requirements. No more guessing games, folks. - Implement Ironclad Access Controls: Enforce stringent access controls to erect impenetrable barriers against unauthorized access to sensitive data and systems. And for the love of all that is secure, deploy multi-factor authentication (MFA) everywhere humanly possible to utterly neutralize the perennial threat of password-based attacks.
- Vigilantly Monitor Network Traffic: Keep a hawk's eye on all network traffic, tirelessly scanning for any tell-tale signs of unauthorized IT activity. Deploying network intrusion detection systems (NIDS) and robust security information and event management (SIEM) systems will empower you to detect suspicious digital peregrinations before they escalate.
- Conduct Regular, Rigorous Security Audits: Don't just cross your fingers and hope. Conduct frequent, thorough security audits designed to ferret out elusive Shadow IT assets and comprehensively assess their prevailing security posture. Leverage vulnerability scanners and, yes, even enlist the dark arts of penetration testing to systematically identify any inherent weaknesses lurking within your Shadow IT infrastructure.
- Provide Perpetual Security Awareness Training: Education is not a one-and-done event. Provide ongoing, dynamic security awareness training to consistently educate employees about the ever-evolving risks of Shadow IT and the fundamental importance of meticulously adhering to security policies. It's about fostering a culture of vigilance.
- Cultivate Collaboration Between IT and Business Units: Break down those silos! Actively foster an environment of open, ongoing collaboration between IT and various business units. This ensures that technological solutions are not just meeting the business's pressing needs but are also staunchly adhering to your organization’s unwavering security standards. A little teamwork goes a long way.
- Leverage EASM Tools for Continuous, Unblinking Monitoring: This isn't a one-time scan; it's a perpetual commitment. Harness the formidable power of EASM platforms like TRaViS for ceaseless monitoring of your external attack surface. This relentless vigilance ensures that any newly emerging Shadow IT assets or burgeoning threats are swiftly identified and decisively addressed.
By meticulously implementing these best practices, organizations aren't just making incremental improvements; they're fundamentally shifting the paradigm, dramatically reducing the inherent risks associated with Shadow IT and elevating their overall security posture to an entirely new level. This isn't just about minimizing potential damage; it’s about actively cultivating a deeply ingrained culture of security awareness and shared responsibility across the entire organizational landscape. It’s about, dare I say, adulting in the digital realm.
Conclusion: Taming the Digital Wild West
Let’s be unequivocally clear: Shadow IT stands as a formidable, often unseen, adversary to enterprise security, spawning hidden vulnerabilities and expanding the attack surface with unnerving efficiency. The profound lack of visibility into these unsanctioned digital assets is a direct conduit to devastating data breaches, crippling compliance violations, and, predictably, agonizing financial setbacks. By deeply understanding the underlying catalysts of Shadow IT and, critically, by implementing a meticulously crafted, robust management strategy, organizations can—and indeed, must—reassert complete control over their intricate digital footprint. And here’s the kicker: deploying proactive EASM solutions, like the unparalleled
TRaViS, is not just helpful; it is absolutely indispensable for meticulously discovering, judiciously assessing, and definitively mitigating the myriad risks inexorably linked with Shadow IT. This ensures nothing less than a more secure, more resilient, and ultimately, far more prosperous enterprise. TRaViS's AI-powered asset discovery and tireless continuous monitoring capabilities provide precisely the kind of razor-sharp visibility absolutely essential to effectively combat this pervasive, often exasperating, threat. It’s time to stop playing hide-and-seek with your own infrastructure and get serious.
Ready to See What's Lurking?
Are you prepared to finally seize command of your attack surface and systematically obliterate those elusive Shadow IT risks? Excellent! Schedule a demo of TRaViS today and witness firsthand how our AI-enhanced EASM platform can grant you not just complete visibility, but truly proactive threat management. Because in this game, what you don't know absolutely can hurt you.











