What if a single oversight could hand hackers the keys to your app’s most sensitive data—user emails, payment details, even private business logic? That’s the reality of GraphQL introspection, a feature that’s a developer’s dream but a security nightmare when left unchecked. Every day, companies unknowingly expose their systems, and breaches at giants like GitLab and Shopify prove it’s not a question of if, but when. Ready to lock the door before it’s too late?
What Is GraphQL and Why Does Security Matter?
If you’ve ever wondered how modern apps fetch data so efficiently, GraphQL might be the answer. It’s a powerful query language that lets developers ask for exactly the data they need—no more, no less. Think of it like ordering from a menu: you pick what you want, and the kitchen (the server) delivers it fast. This flexibility has made GraphQL a favorite for companies like Facebook, Shopify, and GitLab.
But here’s the catch: GraphQL has a feature called introspection that, while helpful during development, can become a massive security risk if left on in a live, public-facing environment (known as "production"). Introspection lets anyone peek at the "menu" of your app’s data—revealing what’s available, how it’s structured, and even sensitive details like user emails or payment info. For hackers, this is like handing over a treasure map to your system.
In this guide, we’ll break down the dangers of exposing sensitive data through GraphQL introspection, show real-world examples of where it’s gone wrong, and give you step-by-step tips to secure your GraphQL API. Whether you’re a beginner or a seasoned developer, you’ll learn why you should always disable schema exposure in production and how to keep your app safe.
What Is GraphQL Introspection? A Simple Explanation
.jpeg)
Think of building a house. You hand your architect a tool that reveals every room, door, and window on the blueprint. That’s essentially what GraphQL introspection gives developers—a built-in way to explore everything inside an API.
In simple terms, an API (Application Programming Interface) is like a waiter that takes your order (data requests) and brings it to your table (the app). With introspection, developers can send special queries like __schema or __type to ask the API:
- What kinds of data exist? (e.g., User, Order, Payment)
- What fields are available? (e.g., email, phoneNumber, address)
- What can I do with this data? (i.e., available queries and mutations)
This is incredibly useful during development. Tools like GraphiQL or Postman use introspection to provide real-time suggestions as you type—like autocomplete for your API.
But once your app is live? Leaving introspection open is like leaving your house unlocked with a giant sign that says, “Here’s the floorplan—help yourself.” Malicious actors can map out your API structure, identify sensitive fields, and look for weak spots.
How Exposed GraphQL Schemas Get Exploited: A Real-Life Example
Let’s look at a common scenario with a GraphQL mutation (a way to change data, like updating a password).
Here’s an example:
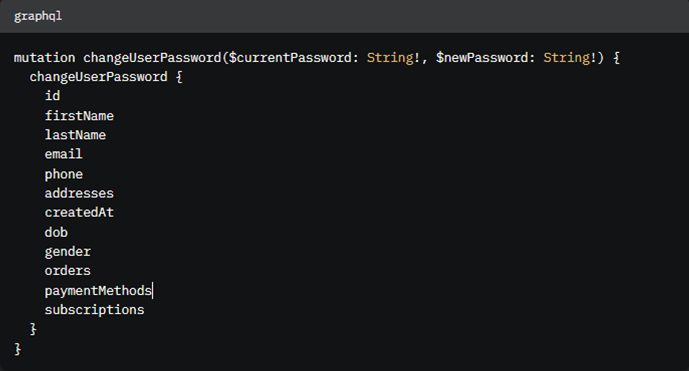
What’s Happening Here?
- The user types their current password and a new one.
- The server updates the password and sends back a bunch of info about the user—like their name, email, phone number, birthday, and even shopping orders.
If introspection is enabled, anyone can see this mutation exists and what it returns. A hacker could:
- Guess Passwords: Try common passwords in the currentPassword field to break into accounts.
- Steal Data: Grab sensitive details like email or paymentMethods for identity theft or fraud.
- Cause Chaos: Change user info without permission.
This isn’t just theory—it’s happened before.
3 Real-World Cases: When GraphQL Introspection Went Wrong
Here are three examples where leaving introspection on led to trouble:
- GitLab (2018): GitLab, a platform for coding projects, had a GraphQL API that exposed its schema. Hackers could see hidden fields like internalNotes and projectSecrets, which weren’t meant for public eyes. GitLab fixed this by turning off introspection in production. (Source: "GraphQL Security Best Practices," Salt Security, 2020).
- Shopify (2020): Shopify’s GraphQL API accidentally left introspection on, revealing fields like customerPaymentInstruments (payment details) and privateMetafields (secret store data). This could’ve let attackers steal financial info. Shopify patched it after a report. (Source: "API Security Report," OWASP, 2021).
- Facebook (2017): Early GraphQL use at Facebook exposed internal user data through introspection. This wake-up call pushed them—and the industry—to secure APIs better. (Source: "GraphQL: A Data Query Language," Facebook Engineering Blog, 2017).
These cases show that GraphQL introspection vulnerabilities aren’t rare—they’re a real threat.
5 Major Risks of Leaving GraphQL Introspection Enabled
When your schema (the API’s blueprint) is exposed, here’s what can go wrong:
- Data Snooping (Enumeration): Hackers can list every type and field—like finding a directory of user emails or order histories. Even if they can’t access it yet, they know what to target.
- Breaking In (Unauthorized Access): If some fields (e.g., paymentMethods) are meant only for admins, exposing them helps hackers find weak spots to exploit.
- Messing with Data (API Abuse): With mutations like changeUserPassword, attackers could change passwords or other info by guessing inputs, locking users out or stealing accounts.
- Tricking the System (Business Logic Exploitation): Knowing fields like storeCredit or discountCode lets hackers manipulate your app’s rules—like giving themselves free money.
- Legal Trouble (Regulatory Violations): Fields like dob (date of birth) or gender might break privacy laws like GDPR (Europe) or CCPA (California) if exposed, leading to fines.
Why It’s Scary: Hackers don’t need to guess blindly—they get a full map of your data.
Why You Must Disable GraphQL Introspection in Production
Turning off introspection is like locking your house and hiding the key. Here’s why it’s a must:
- Fewer Targets: Hackers can’t see your schema, so they’re stuck guessing.
- No Data Leaks: Sensitive fields stay hidden from prying eyes.
- Safer Logic: Your app’s rules (e.g., how discounts work) aren’t exposed.
- Protection from Changes: Mutations become harder to abuse without schema knowledge.
- Legal Peace: You avoid accidentally sharing regulated data.
How to Secure Your GraphQL API: Step-by-Step Best Practices
Securing your GraphQL API doesn’t have to be hard. Here’s a beginner-friendly guide:
Turn Off Introspection in Production Use this code with Apollo Server (a popular GraphQL tool):
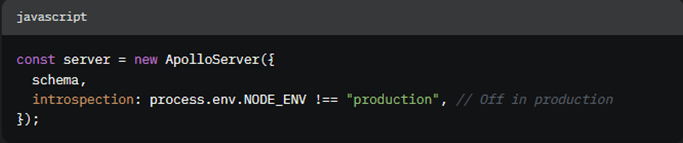
What It Does: Introspection only works in “development” mode (when you’re building), not “production” (when users access it).
Control Who Sees What (Authorization)
- Add rules so only logged-in users see their own data.
- Use RBAC (Role-Based Access Control): Admins see more than regular users.
- Example: Only let managers query paymentMethods.
Hide Sensitive Fields (Field-Level Permissions)
- Block fields like dob or orders unless the user has permission.
- Think of it like a VIP list—only certain people get in.
Watch Your API (Monitoring)
- Tools like Apollo Studio track what queries people send.
- Spot weird activity, like someone asking for tons of data at once.
Limit Overuse (Rate Limiting and Complexity)
- Cap how many requests someone can make (e.g., 100 per minute).
- Stop huge queries that could crash your server (a “denial-of-service” attack).
Add a Shield (Web Application Firewall)
- A WAF filters out bad requests before they reach your API.
Update Regularly
- Keep tools like Apollo or Graphene fresh with security fixes.
How TRaViS Can Help You Find and GraphQL Vulnerabilities

Still worried about missing a hidden GraphQL flaw? Enter TRaViS, a cutting-edge tool from Seron Security, designed to sniff out security risks like exposed introspection in your APIs. Think of TRaViS as your personal security guard—it scans your GraphQL setup, flags vulnerabilities (like an open schema), and gives you clear, actionable steps to lock it down. Whether it’s spotting an enabled __schema query or a misconfigured mutation, TRaViS has your back.
In a world where breaches like GitLab and Shopify show the stakes, TRaViS empowers you to stay one step ahead of attackers. It’s built for innovators who refuse to settle for “good enough” security—and it’s ready to analyze your API today.
Conclusion: Don’t Let GraphQL Introspection Sink Your App
GraphQL is a game-changer, but leaving introspection on in production is like leaving your front door wide open—with a sign listing everything inside. Real breaches at GitLab, Shopify, and Facebook prove the dangers of GraphQL schema exposure. By disabling introspection, setting strict permissions, and keeping an eye on your API, you can stop hackers in their tracks and protect your users’ data.
Don’t expose your schema in production—it’s a risk you can’t afford. And with tools like TRaViS, you don’t have to guess if you’re safe.
Ready to take control and secure your GraphQL API like a pro? You’re not just a developer—you’re a guardian of innovation. Don’t let criminals outsmart you. Try TRaViS now and see how it uncovers vulnerabilities others miss. Click here to start your free scan and join the elite who build smarter, safer systems. Your app—and your users—deserve the best. Act today!
Book a Consultation
Call us or fill out the form below!