In the intricate, interconnected world of modern software, Application Programming Interfaces (APIs) are the unsung heroes. They are the invisible glue that allows different applications to talk to each other, powering everything from your favorite mobile apps to complex enterprise systems and cloud services. They facilitate the rapid development and deployment that businesses crave. But within this powerful ecosystem, a silent, insidious threat often lurks: Shadow APIs.

What exactly is a Shadow API? Imagine your organization as a grand, meticulously planned city. Every road, every bridge, every connection point is documented, regulated, and monitored. Now, imagine a hidden, undocumented alleyway or a secret tunnel that developers, perhaps with the best intentions, built to speed up traffic or connect a new district. No one officially knows about it, it's not on any map, and critically, it's not patrolled by the city's security. This is the essence of a Shadow API: an API endpoint that exists within your infrastructure but is unknown, undocumented, and unmanaged by your central IT or security teams.
Are you absolutely certain every single digital doorway in your organization is accounted for and secured?
The Genesis of the Unseen: How Shadow APIs Emerge
Shadow APIs don't typically materialize out of thin air with malicious intent. More often than not, they are born from expediency and the fast-paced nature of modern development.
- Rapid Development Cycles: In the agile world of DevOps, developers are under immense pressure to deliver features quickly. Sometimes, a quick fix or a temporary endpoint is created to test functionality or integrate with a new service. This "temporary" solution, however, can easily become permanent and forgotten, existing outside of formal API governance and security reviews.
- Decentralized Teams and "API Sprawl": Large organizations often have numerous development teams working independently. Each team might create APIs for their specific needs, without a centralized mechanism for discovery or approval. This leads to what's known as "API sprawl," where the sheer volume of APIs makes comprehensive tracking incredibly challenging.
- Legacy Systems and Technical Debt: Older systems, often poorly documented, might contain legacy APIs that were never formally decommissioned or integrated into modern API management. When new systems interact with these old ones, new "shadow" connections can be inadvertently created.
- Third-Party Integrations: When integrating with external vendors or services, their APIs might create endpoints on your network that are not fully understood or managed by your internal teams.
- Developer Convenience: Sometimes, a developer might create an API to access a specific dataset or function, not realizing the security implications of bypassing established protocols. This could be a personal API for a small task that then gains wider, unintended usage.
The result of these common scenarios is a growing attack surface that is completely invisible to your traditional security tools and processes. You can't secure what you don't even know exists.
The Catastrophic Risks of the Undiscovered
The dangers posed by Shadow APIs are not theoretical; they are responsible for a significant number of breaches and data exposures. Because these APIs operate outside of official oversight, they often lack fundamental security controls:
- No Authentication or Weak Authentication: Many Shadow APIs might have been created without proper authentication mechanisms, or they might use outdated, easily guessable credentials. An attacker discovering such an endpoint has a direct, unchallenged path into your systems.
- Lack of Authorization and Least Privilege: Even if authenticated, a Shadow API might grant excessive permissions. It could allow an attacker to access sensitive data or perform actions far beyond what a legitimate user of that API should be able to do. This violates the critical principle of "least privilege."
- Unpatched Vulnerabilities: Unlike managed APIs that receive regular security updates and patching, Shadow APIs are often neglected. They can harbor known vulnerabilities that attackers can easily exploit using widely available tools.
- Data Exposure: A Shadow API might inadvertently expose sensitive data—customer records, financial information, intellectual property—because it wasn't designed with data privacy in mind or subjected to proper data classification.
- Compliance Violations: If sensitive data is exposed through a Shadow API, your organization faces severe compliance penalties and reputational damage under regulations like GDPR, HIPAA, or PCI DSS. How can you demonstrate compliance when you don't even know all your data access points?
- Denial of Service (DoS) Attacks: Unmanaged APIs might lack rate limiting or other protective measures, making them vulnerable to DoS attacks that can disrupt your services and impact business continuity.
- Gateway to Lateral Movement: Once an attacker compromises a Shadow API, it can serve as a pivot point to move deeper into your network, potentially reaching critical systems and data that would otherwise be well-protected.
These hidden pathways are a dream for malicious actors. They represent the path of least resistance, allowing them to bypass your expensive, meticulously designed perimeter defenses entirely.
Unmasking the Shadows: The Imperative of API Discovery
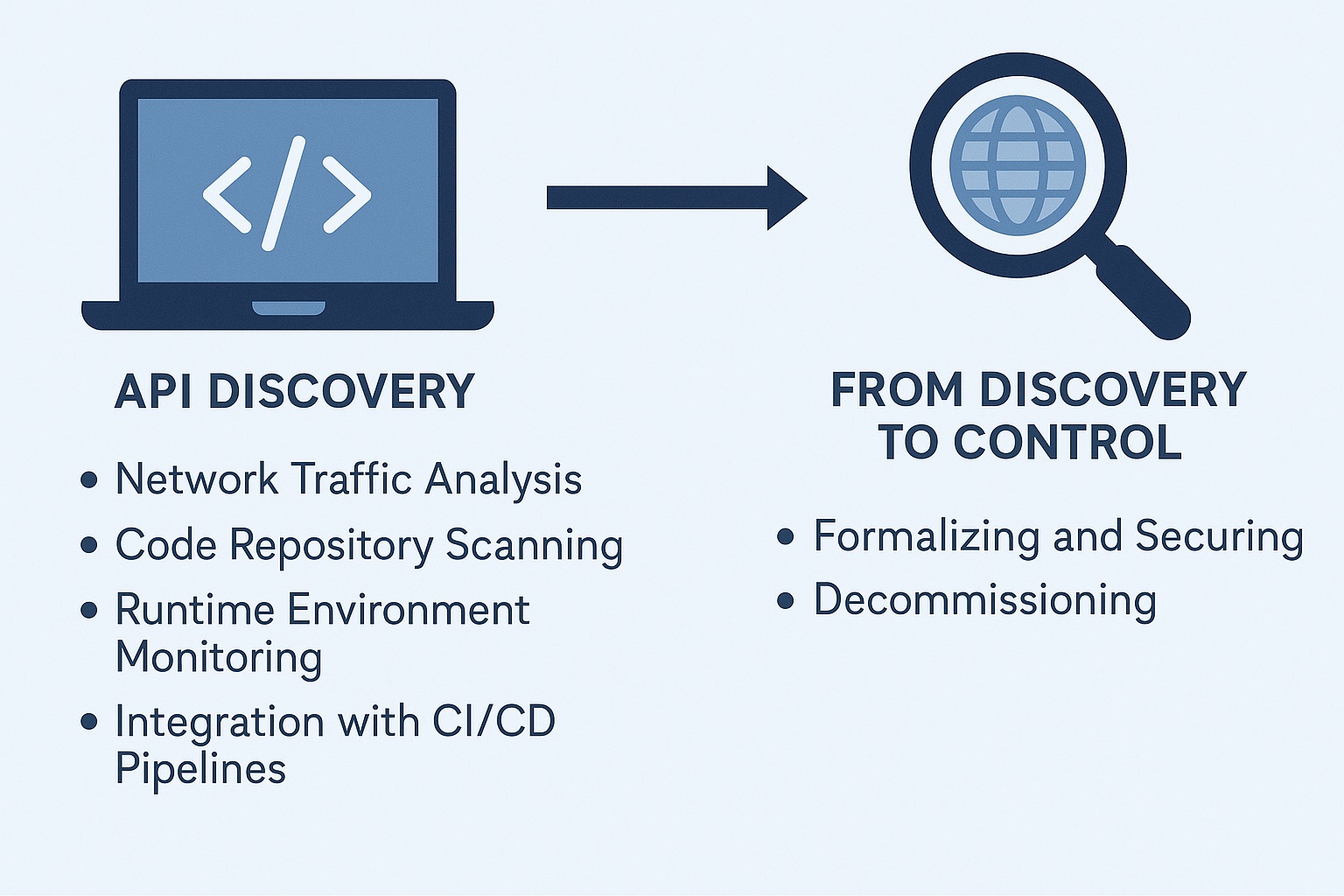
The first, and arguably most critical, step in combating Shadow APIs is discovery. You cannot secure what you cannot see. This goes beyond traditional network scanning and requires specialized capabilities to identify APIs that might not be formally documented or integrated into your API gateways.
True API discovery involves a multi-faceted approach:
- Network Traffic Analysis: Monitoring network traffic for API calls (HTTP/S, GraphQL, REST, SOAP) can reveal communication patterns that indicate the presence of unknown APIs.
- Code Repository Scanning: Automated tools can scan your code repositories (Git, SVN, etc.) for API definitions, endpoints, and associated configurations that might have been deployed without formal registration.
- Runtime Environment Monitoring: Continuously monitoring your application runtime environments – whether in the cloud, on-premises, or in containers – for active API endpoints.
- Integration with CI/CD Pipelines: Embedding API discovery and security checks directly into your Continuous Integration/Continuous Deployment (CI/CD) pipelines can help catch Shadow APIs before they even reach production.
This process of continuous, comprehensive API discovery is not a one-time project. It's an ongoing commitment, as new APIs are constantly being created and existing ones evolve. Just as a city needs regular surveys to update its maps, your digital infrastructure needs continuous API discovery to maintain a complete inventory.
From Discovery to Control: Managing Your API Ecosystem
Once discovered, Shadow APIs must be brought under management. This involves a clear strategy for either:
- Formalizing and Securing: Integrating the discovered API into your official API management platform, applying proper authentication, authorization, rate limiting, and continuous monitoring. This means applying the principle of Zero Trust to all API interactions.
- Decommissioning: If the API is no longer needed or poses an unacceptable risk, it must be securely decommissioned, ensuring all related data and access points are removed. This includes removing old versions of APIs that are no longer supported, often referred to as "Zombie APIs."
This is where true API governance comes into play. It's about establishing clear policies, processes, and tools to ensure that all APIs are designed securely, documented, managed throughout their lifecycle, and continuously monitored for threats.
Building a Resilient API Security Posture
Addressing Shadow APIs is a cornerstone of a robust API security strategy. It requires a combination of technology, processes, and cultural shifts within your organization.
- Implement an API Gateway: A centralized API Gateway acts as the single entry point for all API traffic, allowing you to enforce security policies, authentication, authorization, and rate limiting uniformly.
- Automate API Security Testing: Incorporate automated security testing (SAST, DAST, IAST) into your development pipelines to identify vulnerabilities in APIs early.
- Leverage Dedicated API Security Platforms: Specialized API security solutions go beyond traditional WAFs to understand API logic, detect anomalies, and protect against API-specific attacks, including those targeting Shadow APIs.
- Foster a Security-First Development Culture: Educate developers about the risks of unmanaged APIs and empower them with secure coding practices and tools. Encourage collaboration between development and security teams.
- Continuous Monitoring and Threat Intelligence: Monitor API traffic for suspicious patterns, unusual access attempts, and anomalies that might indicate an attack or the presence of a new, unmanaged endpoint.
The modern enterprise runs on APIs. They are the circulatory system of your digital business. Leaving any part of that system unmapped and unmonitored is an invitation to disaster. The risk isn't just about what you know, but about what you don't know. The true master understands that visibility is the first line of defense.
This is precisely where specialized expertise becomes invaluable. TravisASM helps organizations gain comprehensive visibility into their API ecosystem, identifying and mitigating the risks posed by Shadow APIs and unmanaged endpoints. They provide the tools and guidance to transition from an unknown attack surface to a fully controlled and secured API environment, ensuring your digital pathways are not only efficient but impenetrable.
Ready to shine a light on your invisible backdoors?
Don't let hidden APIs become your next major breach. Subscribe to our insights or book a demo with TravisASM today and master your API security posture.

Learn More Today!