APIs (Application Programming Interfaces) serve as the crucial communication bridge between different software components. While REST has long been the dominant paradigm for building APIs, a more recent contender, GraphQL, has rapidly gained traction for its flexibility and efficiency. This article delves into what GraphQL is, why developers are increasingly adopting it, the potential security risks it introduces, and how a tool like TRaViS can be instrumental in identifying and mitigating these vulnerabilities.
What is GraphQL?
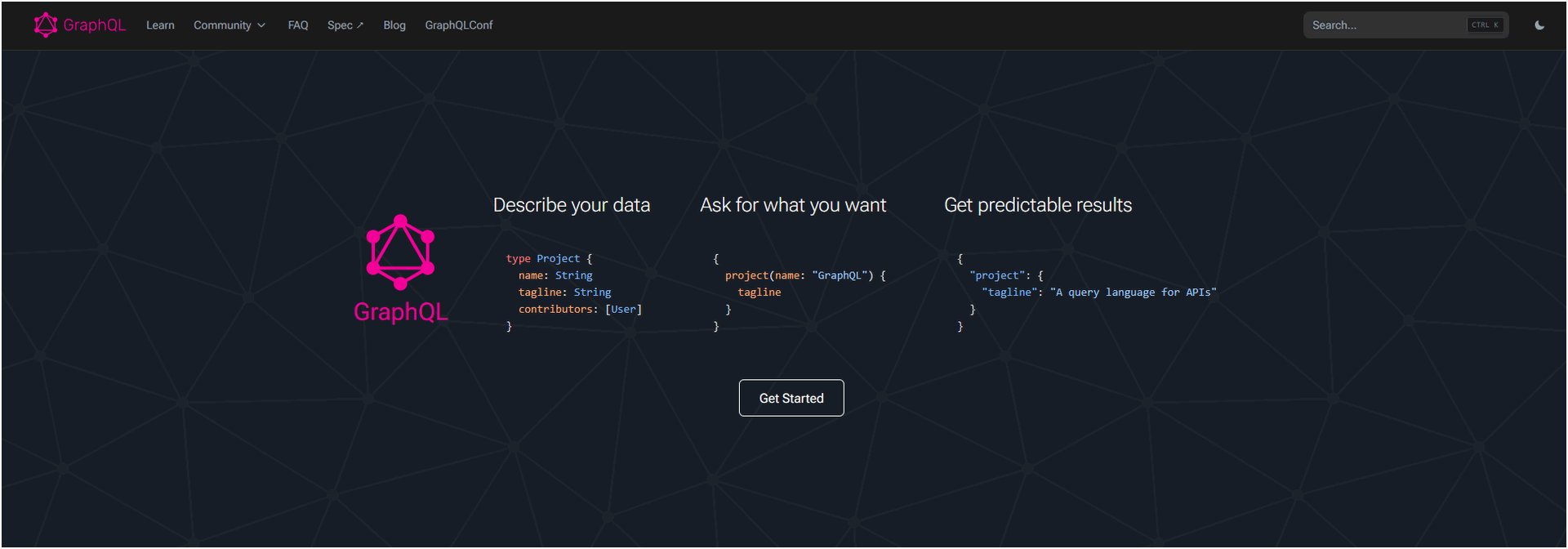
At its core, GraphQL is a query language for your API, and a server-side runtime for executing queries using a type system you define for your data. Developed by Facebook in 2012 and open-sourced in 2015, it offers a fundamentally different approach to data fetching compared to traditional REST APIs.
Instead of having multiple, fixed endpoints that return a pre-defined set of data (as is common with REST), GraphQL exposes a single endpoint. Clients then send precisely structured queries to this endpoint, specifying exactly what data they need and in what shape. The server, guided by a strongly-typed schema you define, then fetches only that requested data.
Think of it like this:
- REST: You go to a restaurant with a fixed menu. You order "Appetizer 1," and you get everything listed under it, even if you only wanted one ingredient. If you then want "Main Course 2," you make a separate order.
- GraphQL: You go to a restaurant where you can tell the chef exactly what ingredients you want from different dishes, and they'll prepare it all in one go, with no extra ingredients you didn't ask for.
This "ask for what you need, get exactly that" philosophy is a game-changer.
Why is GraphQL Used?
GraphQL's popularity stems from several key advantages:
-
Efficiency (Reduced Over-fetching and Under-fetching):
- Over-fetching: In REST, an endpoint might return more data than the client actually needs, leading to wasted bandwidth and processing.
- Under-fetching: Conversely, a client might need data from multiple REST endpoints, requiring several requests and increasing latency.
- GraphQL elegantly solves both by allowing clients to specify their data requirements precisely in a single request. This is particularly beneficial for mobile applications where network constraints are more critical.
- Over-fetching: In REST, an endpoint might return more data than the client actually needs, leading to wasted bandwidth and processing.
-
Faster Development Cycles: The strong type system and introspection capabilities (more on this later) make it easier for frontend and backend teams to collaborate. Frontend developers can understand the API's capabilities without constant communication with the backend, leading to quicker iteration.
-
API Evolution Without Versioning: As application requirements change, adding new fields to a GraphQL schema doesn't require creating new API versions. Existing clients simply ignore the new fields, while new clients can immediately leverage them. This contrasts sharply with REST, where API versioning can become a significant management overhead.
- Real-time Data with Subscriptions: GraphQL offers "subscriptions," a mechanism for clients to receive real-time updates from the server whenever specific data changes. This is invaluable for applications requiring live data feeds, like chat applications, dashboards, or notifications.
Potential Risks of GraphQL APIs

While powerful, GraphQL's flexibility can also introduce new security considerations or amplify existing ones if not handled properly. Some common risks include:
-
Introspection Abuse: GraphQL's introspection feature allows clients to query the API's schema to discover all available types, fields, and operations. While incredibly useful for developers, if left enabled in a production environment, it can expose sensitive information about your backend, including internal fields, data structures, and even business logic. This provides attackers with a "treasure map" to your API.
-
Denial of Service (DoS) Attacks:
- Complex Queries: GraphQL allows deeply nested queries, which can lead to a single request triggering an exorbitant amount of work on the server, consuming excessive CPU or memory. An attacker could craft such a query to intentionally overload the server.
- Batching Attacks: GraphQL often supports sending multiple queries in a single HTTP request (batching). While efficient, this can be abused to send a large number of expensive operations in one go, similar to a DoS attack.
- Alias Overloading: Attackers can use aliases to repeatedly query the same field with different names within a single request, again increasing server load.
- Complex Queries: GraphQL allows deeply nested queries, which can lead to a single request triggering an exorbitant amount of work on the server, consuming excessive CPU or memory. An attacker could craft such a query to intentionally overload the server.
-
Injection Attacks: Like any API, GraphQL is susceptible to injection vulnerabilities such as:
- SQL Injection: If user input is not properly sanitized and validated before being used in database queries.
- Cross-Site Scripting (XSS): If unsanitized user-provided data is reflected in the API's responses and then rendered in a client-side application.
- Command Injection: If user input is used in system commands without proper sanitization.
- SQL Injection: If user input is not properly sanitized and validated before being used in database queries.
-
Broken Authentication and Authorization: Misconfigurations in authentication mechanisms can allow attackers to bypass login procedures. Similarly, insufficient authorization checks at the field or object level can enable unauthorized users to access, modify, or delete data they shouldn't.
-
Excessive Data Exposure: While GraphQL aims to prevent over-fetching, poorly designed schemas or inadequate access controls can still lead to the API returning more data than intended for a particular user or role, potentially exposing sensitive information.
-
Lack of Rate Limiting: Without proper rate limiting, attackers can brute-force credentials, enumerate data, or launch DoS attacks by sending an excessive number of requests.
- Verbose Error Messages: Detailed error messages, while helpful for debugging, can inadvertently leak sensitive information about the backend infrastructure, database schemas, or internal logic to attackers.
How TRaViS Finds GraphQL Leaks

This is where dedicated security tools like TRaViS (developed by Seron Security) become indispensable. TRaViS is designed to specifically identify and flag GraphQL-related vulnerabilities by focusing on the unique characteristics of GraphQL APIs.
-
Introspection Detection and Analysis:
- TRaViS actively queries the GraphQL endpoint to determine if introspection is enabled in a production environment.
- If introspection is found, it will then leverage this capability to fully map out the GraphQL schema. This includes identifying all available queries, mutations, subscriptions, types, and fields, even those not explicitly exposed in documentation.
- By analyzing the discovered schema, TRaViS can identify potentially sensitive fields that should not be publicly accessible (e.g., internal IDs, user passwords, financial data).
- TRaViS actively queries the GraphQL endpoint to determine if introspection is enabled in a production environment.
-
Automated Vulnerability Scanning: TRaViS employs a range of techniques to identify common GraphQL vulnerabilities:
- Broken Authentication and Authorization Checks: While some authorization issues require deeper context, TRaViS can identify common patterns of misconfigured access controls, such as allowing unauthenticated access to sensitive mutations or queries, or identifying roles that have excessive privileges.
- Sensitive Data Exposure: By analyzing the schema and potential query results, TRaViS can flag fields or data patterns that appear to be sensitive and might be inadvertently exposed.
- Error Message Analysis: It scrutinizes error messages returned by the GraphQL API for overly verbose information that could aid an attacker.
- Broken Authentication and Authorization Checks: While some authorization issues require deeper context, TRaViS can identify common patterns of misconfigured access controls, such as allowing unauthenticated access to sensitive mutations or queries, or identifying roles that have excessive privileges.
-
Continuous Monitoring and Asset Discovery: TRaViS, as part of a comprehensive External Attack Surface Management (EASM) solution, continuously monitors your public-facing assets. This includes discovering new GraphQL endpoints that might be deployed without proper security considerations.
-
Actionable Reporting: Upon detecting vulnerabilities, TRaViS provides detailed reports with actionable insights, guiding developers and security teams on how to remediate the identified leaks and strengthen their GraphQL API security posture.
Conclusion
GraphQL offers compelling advantages for modern API development, providing flexibility, efficiency, and a streamlined developer experience. However, its unique architecture also demands a proactive and specialized approach to security.
Tools like TRaViS are vital for organizations leveraging GraphQL, acting as a crucial line of defense by automatically identifying introspection vulnerabilities, potential DoS vectors, injection flaws, and sensitive data leaks. By integrating such solutions into their security pipeline, businesses can harness the power of GraphQL while ensuring their APIs remain secure against new emerging threats.











