Imagine the scenario: a routine security audit uncovers hundreds of previously unknown assets lurking within your network. This isn't a hypothetical situation; it's a common reality for organizations grappling with the complexities of modern IT infrastructure. The proliferation of cloud services, remote work, and shadow IT has created a sprawling digital footprint that's difficult to manage, let alone secure.
This article delves into the reasons why your IT team might stumble upon a surprisingly large number of unknown assets. We'll explore the challenges of maintaining visibility across your entire attack surface, the risks associated with shadow IT, and the critical role of External Attack Surface Management (EASM) in proactively identifying and mitigating potential threats. Ultimately, you'll understand how solutions like TRaViS can help you regain control of your digital landscape and significantly reduce your organization's risk exposure.
The Expanding Attack Surface: A Breeding Ground for Unknown Assets

The traditional network perimeter is dissolving. Today's organizations rely on a complex web of interconnected systems, cloud services, APIs, and third-party integrations. This expanded attack surface presents a significant challenge for security teams trying to maintain comprehensive visibility. Several factors contribute to the proliferation of unknown assets:
- Cloud Adoption: The ease of provisioning cloud resources often leads to 'shadow IT,' where departments or individual employees spin up services without IT oversight. These resources can quickly become forgotten or unmanaged, creating security blind spots.
- Remote Work: The shift to remote work has blurred the lines between corporate and personal devices. Employees may use personal devices to access company resources, or install unauthorized software, further expanding the attack surface.
- Mergers and Acquisitions: Integrating new companies into your existing IT infrastructure can be a complex process. Often, unknown assets from the acquired company remain undiscovered for extended periods.
- API Proliferation: Modern applications rely heavily on APIs to communicate with each other. Poorly documented or unsecured APIs can become entry points for attackers.
Consider a healthcare organization that rapidly adopted cloud-based telehealth services during the pandemic. Without proper governance, different departments may have independently implemented their own solutions, resulting in a fragmented and difficult-to-manage infrastructure with numerous unknown assets. This lack of visibility can expose sensitive patient data to potential breaches. TRaViS helps organizations discover these hidden cloud assets by continuously scanning for misconfigurations and vulnerabilities, ensuring that all exposed resources are properly secured.
The Dangers of Shadow IT: A Hacker's Playground
Shadow IT refers to IT-related hardware, software, and services used by employees without explicit approval from the IT department. While shadow IT can sometimes improve productivity, it introduces significant security risks:
- Lack of Security Controls: Shadow IT assets often lack the same security controls as sanctioned IT resources, making them vulnerable to exploitation.
- Compliance Violations: Shadow IT can lead to violations of industry regulations like HIPAA, PCI DSS, and GDPR, resulting in hefty fines and reputational damage.
- Data Leakage: Sensitive data stored on shadow IT systems is at a higher risk of leakage due to inadequate security measures.
- Increased Attack Surface: Each shadow IT asset represents an additional entry point for attackers to gain access to your network.
For example, an employee in the finance department might use an unauthorized file-sharing service to exchange sensitive financial documents with external partners. This service may not have the same level of security as the company's approved file-sharing platform, potentially exposing confidential information to unauthorized access. TRaViS's shadow IT discovery capabilities can identify these unauthorized services and alert security teams to potential risks, enabling them to take corrective action before a breach occurs. Furthermore, TRaViS helps enforce security policies and prevent future shadow IT deployments by providing insights into user behavior and recommending alternative, secure solutions.
External Attack Surface Management (EASM): Illuminating the Shadows
External Attack Surface Management (EASM) is a proactive approach to cybersecurity that focuses on identifying and managing all internet-facing assets that could be targeted by attackers. EASM solutions continuously scan the internet to discover your organization's external attack surface, including websites, web applications, APIs, cloud services, and other exposed assets. Key benefits of EASM include:
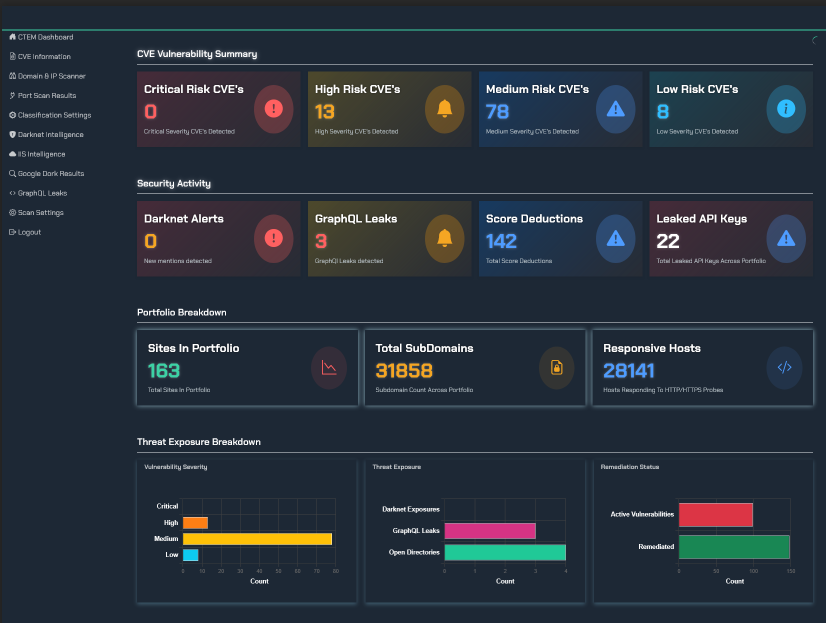
- Comprehensive Visibility: EASM provides a complete view of your external attack surface, including assets that may have been previously unknown or forgotten.
- Vulnerability Identification: EASM tools automatically identify vulnerabilities in your external assets, such as outdated software, misconfigurations, and exposed credentials.
- Risk Prioritization: EASM helps you prioritize remediation efforts by identifying the most critical vulnerabilities and assets that pose the greatest risk to your organization.
- Threat Intelligence: EASM integrates with threat intelligence feeds to identify emerging threats and vulnerabilities that could impact your external attack surface.
TRaViS is a powerful EASM platform that leverages AI and machine learning to provide unparalleled visibility into your external attack surface. Unlike traditional vulnerability scanners, TRaViS continuously monitors your attack surface for changes and automatically discovers new assets as they are deployed. This proactive approach allows you to identify and remediate vulnerabilities before they can be exploited by attackers. TRaViS also provides detailed reports and dashboards that help you track your progress and demonstrate compliance with industry regulations.
API Security: Protecting Your Digital Connections
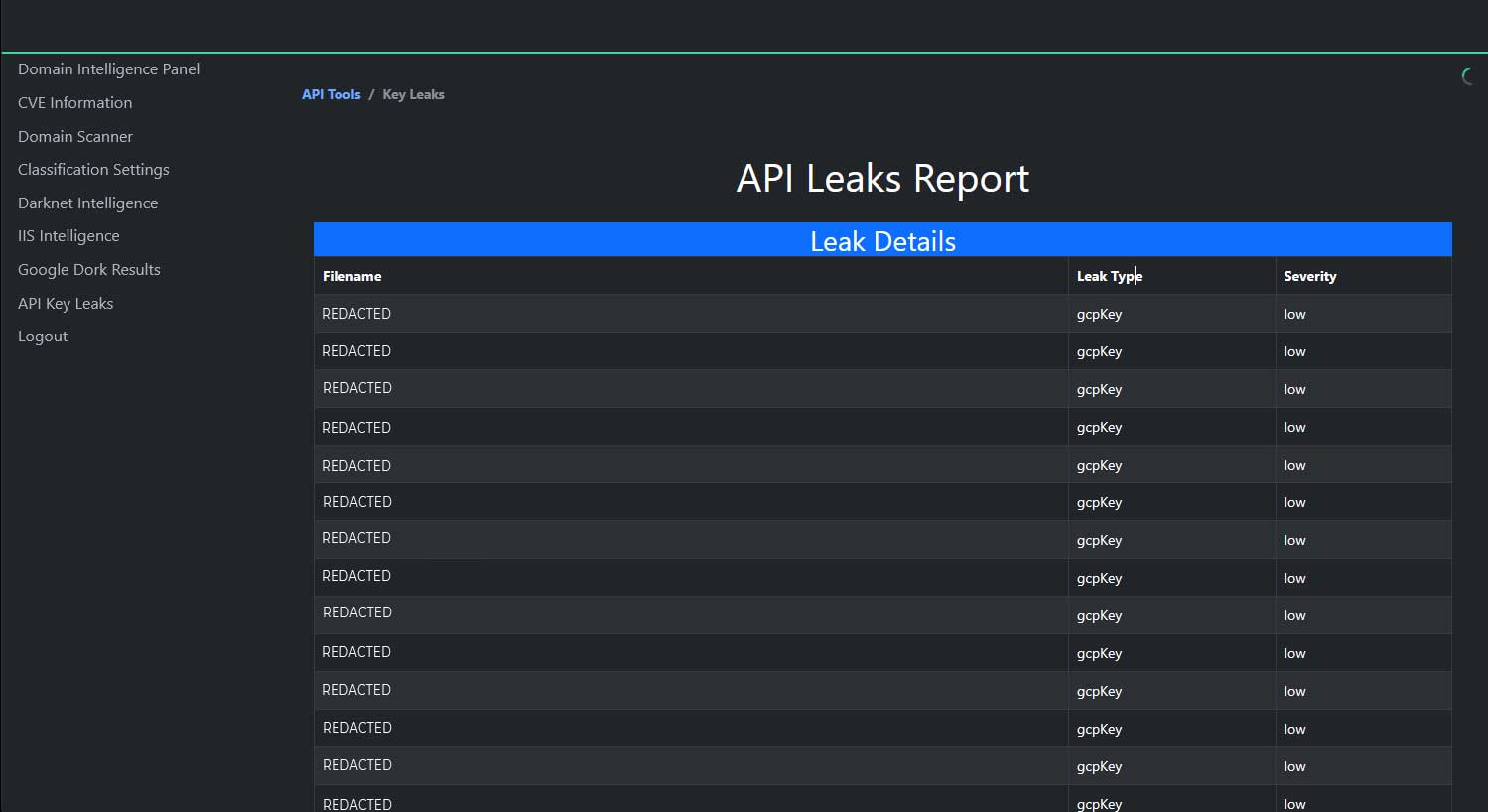
APIs are the backbone of modern applications, enabling seamless communication between different systems and services. However, poorly secured APIs can be a major security risk. Common API security vulnerabilities include:
- Broken Authentication: Weak or missing authentication mechanisms can allow attackers to bypass security controls and gain unauthorized access to sensitive data.
- Injection Attacks: APIs can be vulnerable to injection attacks, such as SQL injection and command injection, which can allow attackers to execute arbitrary code on the server.
- Data Exposure: APIs may expose sensitive data that should be protected, such as personally identifiable information (PII) or financial data.
- Rate Limiting Issues: Lack of rate limiting can allow attackers to flood APIs with requests, causing denial-of-service (DoS) attacks.
Consider an e-commerce company that exposes customer data through an API without proper authentication. An attacker could exploit this vulnerability to gain access to customer accounts and steal sensitive information. TRaViS's API security capabilities can automatically discover and assess the security of your APIs, identifying vulnerabilities such as broken authentication, injection flaws, and data exposure risks. By integrating API security into your EASM strategy, you can ensure that your digital connections are protected from malicious attacks. TRaViS also provides recommendations for remediating API vulnerabilities, helping you improve your overall security posture.
Real-World Impact: Case Studies and Statistics
The consequences of neglecting your external attack surface can be significant. According to a recent study by Ponemon Institute, the average cost of a data breach is $4.24 million. Many of these breaches are caused by vulnerabilities in external-facing assets that could have been identified and remediated with an effective EASM solution.
- Case Study: Financial Institution: A financial institution implemented TRaViS and discovered over 500 previously unknown assets, including outdated web servers, misconfigured cloud storage buckets, and exposed databases. By remediating these vulnerabilities, the institution significantly reduced its risk of a data breach and improved its compliance posture.
- Statistic: Healthcare Provider: A healthcare provider experienced a ransomware attack that exploited a vulnerability in an unpatched web application. The attack resulted in the theft of sensitive patient data and significant financial losses. With TRaViS, healthcare providers can proactively identify and patch vulnerabilities in their external assets, preventing similar attacks.
- MSSP Success: A Managed Security Service Provider (MSSP) leveraged TRaViS to enhance its service offerings. By providing clients with comprehensive EASM, the MSSP was able to identify critical vulnerabilities and reduce client risk exposure. This led to increased customer satisfaction and new business opportunities.
These examples highlight the importance of proactively managing your external attack surface and the value of EASM solutions like TRaViS in mitigating potential threats.
Conclusion
In the intricate world of digital technology today, maintaining visibility across your entire attack surface is more critical than ever. The proliferation of cloud services, remote work, and shadow IT has created a breeding ground for unknown assets, which can significantly increase your organization's risk of a data breach. By implementing a proactive EASM strategy and leveraging solutions like TRaViS, you can regain control of your digital footprint, identify and remediate vulnerabilities before they are exploited, and protect your organization from costly cyberattacks. Don't let unknown assets become your weakest link.
Get Started
Ready to uncover the hidden risks in your external attack surface? Schedule a demo of TRaViS today and discover how our AI-powered EASM platform can help you proactively identify and remediate critical vulnerabilities that other tools miss.
