We've previously explored the first five tenets of NIST Special Publication 800-207, which lays out the foundational principles of a Zero Trust Architecture (ZTA). Today, we complete our deep dive by focusing on the crucial final two tenets: Tenet 6 (The enterprise monitors and measures the integrity and security posture of all owned and associated assets) and Tenet 7 (All resource authentication and authorization are dynamic and strictly enforced before access is allowed).
These tenets emphasize continuous verification and adaptive control, which are hallmarks of a mature ZTA.
Tenet 6: Monitor and Measure Asset Integrity and Security Posture
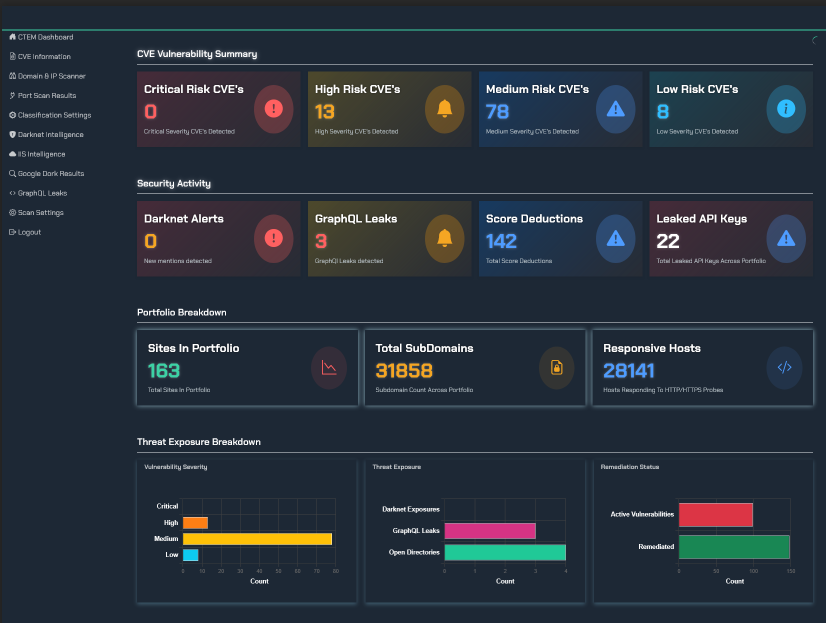
This tenet underscores the idea that trust is not a one-time assessment. Instead, the security posture and integrity of every asset (endpoints, applications, data, network components, etc.) must be continuously monitored and measured. This includes both enterprise-owned assets and any associated assets (e.g., BYOD, partner systems) that interact with enterprise resources.
Key Aspects of Tenet 6:
- Continuous Monitoring: Implementing systems that constantly gather telemetry about asset health, configuration, vulnerabilities, and behavior.
- Security Posture Assessment: Regularly evaluating assets against defined security baselines and policies.
- Integrity Checks: Verifying that assets have not been tampered with or compromised (e.g., checking file integrity, boot process integrity).
- Data-Driven Decisions: Using the collected monitoring data to inform access decisions, risk assessments, and incident response.
- Automated Response: Where possible, automating responses to detected deviations in security posture (e.g., isolating a compromised endpoint).
Why is this critical? Attackers constantly seek to compromise assets. Continuous monitoring allows an organization to detect these compromises (or attempts) early and understand the current risk associated with an asset before it accesses resources. Without this, an asset that was secure yesterday might be a significant threat today.
TRaViS and Tenet 6: TRaViS directly supports Tenet 6 by providing comprehensive visibility into the security posture of assets across the enterprise. Our EASM capabilities help identify and monitor owned and associated assets, detect misconfigurations, and assess vulnerabilities. This continuous insight is vital for making informed, dynamic access decisions as prescribed by ZTA.
Tenet 7: All Resource Authentication and Authorization are Dynamic and Strictly Enforced

Building directly on Tenet 6, Tenet 7 states that the act of authenticating and authorizing access to a resource is not a static, one-off event. It must be dynamic, meaning it can change based on the real-time assessment of the requesting asset's (and user's) security posture, among other contextual factors. Furthermore, these checks must be strictly enforced before any access is granted.
Key Aspects of Tenet 7:
- Policy Enforcement Point (PEP): A logical component that makes access decisions based on policies defined by a Policy Engine (PE) and informed by a Policy Administrator (PA).
- Dynamic Policies: Access policies that can adapt based on changing conditions, such as:
- The security posture of the user's device (from Tenet 6).
- User behavior analytics.
- Time of day or geographic location.
- Sensitivity of the resource being requested.
- Re-authentication/Re-authorization: Requiring users or assets to re-verify their identity and authorization if risk levels change or for access to particularly sensitive resources.
- Least Privilege Enforcement: Ensuring that even authenticated and authorized entities are only granted the minimum necessary access to perform their task.
Why is this critical? Static access controls are brittle. A user or device that was trustworthy an hour ago might not be now. Dynamic authentication and authorization allow the ZTA to respond to evolving risks and ensure that access is always appropriate for the current context.
TRaViS and Tenet 7: TRaViS facilitates the implementation of Tenet 7 by providing the crucial asset posture data needed by Policy Engines to make dynamic access decisions.
The Culmination of Zero Trust Principles
Tenets 6 and 7, working in tandem, represent the operational core of a Zero Trust Architecture. They move ZTA from a theoretical model to a living, breathing security framework that continuously assesses risk and adapts its controls accordingly. By diligently monitoring asset security and dynamically enforcing access, organizations can significantly reduce their attack surface and build a more resilient security posture.
This concludes our deep dive into NIST's Seven Tenets of Zero Trust. We hope this series has provided valuable insights for your ZTA journey!
.png)
