Introduction
What is CTEM (Continuous Threat Exposure Management)?
What is EASM (External Attack Surface Management)?
What is ASM (Attack Surface Management)?
Key Differences Between CTEM, EASM, and ASM
Core Functionality
- Use Cases
- Role in Vulnerability Management
- Integration with Other Tools
TRaViS ASM: A Comprehensive Cybersecurity Solution
Real-World Examples
Why CTEM, EASM, and ASM Are Essential for CISOs
Frequently Asked Questions (FAQs)
Conclusion
Call-to-Action
Introduction
In today's cybersecurity landscape, organizations face an ever-growing array of external and internal threats. With complex digital footprints and the rapid pace of technological change, solutions like CTEM (Continuous Threat Exposure Management), EASM (External Attack Surface Management), and ASM (Attack Surface Management) are becoming indispensable. However, for many cybersecurity professionals, understanding the differences between these approaches is crucial for building a robust security posture.
In this guide, we will delve into the specifics of each methodology, highlight their differences, and explain how TRaViS ASM, an advanced platform from Seron Security, integrates these technologies to provide organizations with a unified solution for managing their cybersecurity risks.
What is CTEM (Continuous Threat Exposure Management)?
Continuous Threat Exposure Management (CTEM) is an innovative approach to identifying, prioritizing, and managing threats on a continuous basis. Unlike traditional, periodic vulnerability assessments, CTEM focuses on ongoing threat intelligence and security assessments to keep an organization ahead of potential cyberattacks.
CTEM’s key features include:
- Continuous monitoring of your attack surface.
- Proactive risk management based on real-time intelligence.
- Prioritization of vulnerabilities to ensure that high-risk threats are addressed first.
- Integration with threat intelligence feeds to detect emerging threats before they become critical.
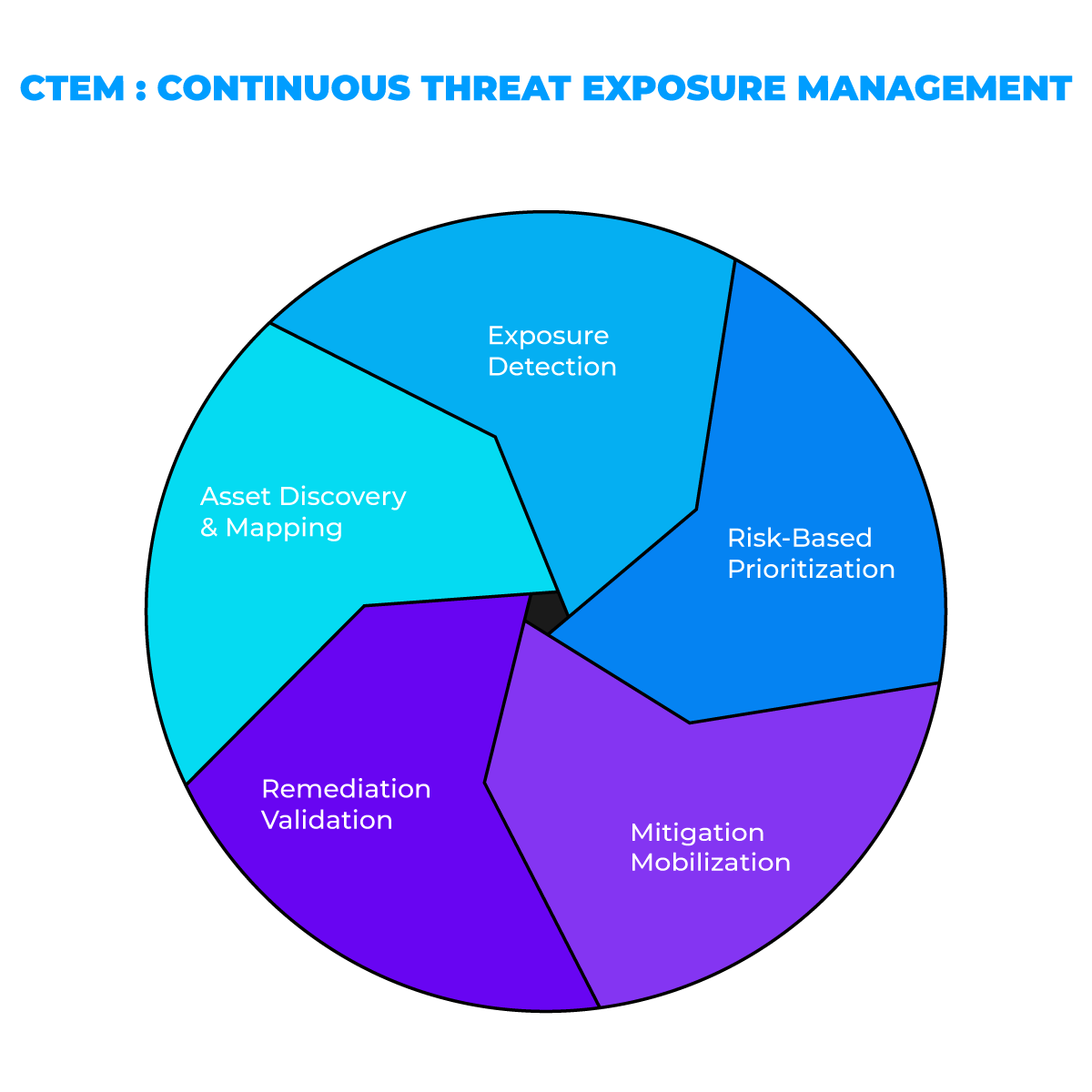
TRaViS Continuous Threat Exposure Management (CTEM) Framework (Diagram Above)
- Asset Discovery & Mapping
Leverage TRaViS's automated discovery to uncover hidden digital assets, shadow IT, and new endpoints across your environment. - Exposure Detection
Analyze these assets for vulnerabilities, weak configurations, and exposed APIs. TRaViS continuously scans for emerging threats, bringing real-time insights into your dashboard. - Risk-Based Prioritization
Using the TRaViS Threat Prioritization Algorithm, vulnerabilities are ranked by severity, business impact, and exploitability, allowing your team to address the most urgent issues first. - Mitigation Mobilization
Deploy mitigation strategies and patch management systems through TRaViS integrations with third-party tools (SIEM, SOAR). This stage focuses on remediating prioritized risks effectively. - Remediation Validation
Once mitigations are applied, TRaViS validates and monitors these fixes through automated testing and continuous vulnerability reassessment, ensuring a robust security posture.
What is EASM (External Attack Surface Management)?

External Attack Surface Management (EASM) focuses on discovering, monitoring, and managing all externally exposed digital assets such as websites, IP addresses, APIs, and third-party services. As businesses expand their online presence, they inadvertently create a larger attack surface, which could be exploited by cybercriminals.
The core functionality of EASM includes:
- Discovering new digital assets that may be publicly exposed but not currently monitored.
- Monitoring external assets for vulnerabilities such as exposed APIs, credentials, or misconfigurations.
- Reducing the risk of unauthorized access by continuously scanning your organization's public-facing infrastructure.
What is ASM (Attack Surface Management)?

Attack Surface Management (ASM) is a broader term that encompasses the identification and monitoring of both internal and external digital assets. Unlike EASM, which only focuses on external assets, ASM covers the entire attack surface—both internal networks and publicly exposed systems.
ASM solutions, like TRaViS ASM, provide comprehensive visibility and monitoring across your digital footprint, enabling organizations to:
- Map internal and external assets and their vulnerabilities.
- Monitor the attack surface continuously for any potential threats.
- Prioritize vulnerabilities based on risk factors such as exploitability and impact.
Key Differences Between CTEM, EASM, and ASM
Core Functionality
- CTEM delivers continuous threat assessments and vulnerability management.
- EASM focuses solely on external asset management and discovery.
- ASM is a more comprehensive solution that covers both internal and external attack surfaces.
Use Cases
- CTEM is ideal for organizations that require constant vigilance against emerging threats.
- EASM is tailored for companies concerned about their external exposure and the risks associated with public-facing systems.
- ASM is suited for organizations with complex IT environments, needing both internal and external coverage.
Role in Vulnerability Management
- CTEM ensures that vulnerabilities are identified and prioritized in real-time.
- EASM helps companies minimize their exposure by discovering public-facing risks.
- ASM provides comprehensive coverage, ensuring that all assets—internal and external—are monitored and protected.
Integration with Other Tools
- CTEM integrates seamlessly with SIEM and SOAR tools to automate response to high-risk threats.
- EASM connects to external monitoring tools, offering a clear picture of your external exposure.
- ASM works across various internal and external systems, offering integration with SIEMs, threat intelligence platforms, and more.
TRaViS ASM: A Comprehensive Cybersecurity Solution

TRaViS ASM, from Seron Security, merges the capabilities of CTEM, EASM, and ASM into a single platform that offers end-to-end security management. It allows organizations to manage their entire attack surface effectively by monitoring both internal systems and public-facing infrastructure. TRaViS ASM goes beyond just identifying vulnerabilities; it provides actionable intelligence, enabling security teams to take proactive measures.
Core Features of TRaViS ASM:
- Continuous Asset Discovery: Automatically detect new assets across your digital landscape.
- Vulnerability Prioritization: Focus on high-risk vulnerabilities based on exploitability and business impact.
- Dark Web Monitoring: Gain insight into potential risks by tracking dark web mentions and data leaks.
- Exposed API Detection: Identify API keys or endpoints inadvertently exposed to the public.
- Comprehensive Reporting: Generate detailed reports to support compliance and risk management efforts.
Real-World Examples

Consider a global retail organization managing thousands of domains and subdomains. By using TRaViS ASM, the organization can continuously monitor its vast digital landscape, identifying misconfigurations and vulnerable assets as they appear. Additionally, the Dark Web Monitoring feature has alerted the team to leaked credentials, allowing for rapid remediation before any damage occurs.
Another example is a financial institution that recently expanded its cloud infrastructure. Through TRaViS ASM, the institution identified and mitigated several vulnerabilities in their API infrastructure, preventing potential exploitation.
Why CTEM, EASM, and ASM Are Essential for CISOs

For CISOs and cybersecurity professionals, these tools are essential for maintaining a proactive security posture. Each solution addresses a different aspect of the modern attack surface, and TRaViS ASM integrates all three into a cohesive, actionable platform.
Benefits for CISOs:
- CTEM ensures constant vigilance, providing real-time insights into emerging threats.
- EASM enables external risk reduction by identifying vulnerabilities in public-facing systems.
- ASM offers a comprehensive view, allowing CISOs to manage risks across all digital assets.
Frequently Asked Questions (FAQs)
Q: How does CTEM differ from traditional vulnerability assessments?
A: CTEM provides continuous monitoring and threat exposure analysis, while traditional vulnerability assessments are usually periodic and less responsive to emerging threats.
Q: What assets are covered under EASM?
A: EASM focuses on external assets such as websites, domains, APIs, IP addresses, and third-party services that are publicly exposed.
Q: How does TRaViS ASM integrate with existing cybersecurity tools?
A: TRaViS ASM integrates with SIEM, SOAR, and other security management platforms to provide a unified security posture and streamline the vulnerability management process.
Q: What role does Dark Web Monitoring play in TRaViS ASM?
A: Dark Web Monitoring alerts organizations to potential leaks or exposures of sensitive data that could be found on the dark web, allowing for immediate remediation.
Conclusion
Understanding the differences between CTEM, EASM, and ASM is essential for developing a well-rounded security strategy. Each approach serves a unique purpose, and when integrated, they provide a comprehensive solution for managing and mitigating risks across an organization’s digital landscape. With TRaViS ASM, you can bring all three technologies together in one platform, ensuring complete visibility and control over your cybersecurity efforts.
See the Unseen with TRaViS ASM

Is your attack surface fully secured? Explore how TRaViS ASM can provide comprehensive protection for your organization.












