Vulnerabilities Discovered by TRaViS
As a cybersecurity professional, safeguarding your digital assets from potential threats is paramount. TRaViS, an advanced External Attack Surface Management (EASM) platform by Seron Security, excels in identifying, assessing, and managing vulnerabilities across your organization's external web assets. Discover how TRaViS ensures comprehensive security coverage and peace of mind.
Book A Demo Today!
Types of Vulnerabilities Discovered
Outdated Software and Misconfigurations
- Outdated Software: TRaViS identifies outdated software versions that could be vulnerable to known exploits, ensuring your systems are always up-to-date.
- Misconfigurations: Detects improper configurations in software and systems that could be exploited by attackers, helping you correct these issues before they become security risks.
Exposed API Keys
- Publicly Accessible API Keys: TRaViS scans for API keys that are exposed publicly, which can be exploited to gain unauthorized access to your systems and sensitive data.
Learn more about the risks
API Vulnerabilities
- Authentication Issues: Identifies weak or missing authentication mechanisms in APIs, protecting your systems from unauthorized access.
- Authorization Flaws: Detects APIs that grant excessive permissions or fail to enforce proper access controls, ensuring your data is only accessible to those who should have it.
Zero-Day Vulnerabilities
- Unknown Vulnerabilities: TRaViS proactively identifies and reports zero-day vulnerabilities—those that have not yet been publicly disclosed or patched—allowing you to mitigate risks before they are exploited.
Dark Web Mentions
-
Data Leakage: Monitors the dark web for mentions of your organization's data, signaling potential data breaches or leaks that require immediate attention.
New Digital Assets
-
Unsecured New Assets: Detects newly added digital assets that may not yet be integrated into your security framework, ensuring they are secured promptly to prevent unauthorized access.
Compromised Credentials
-
Exposed Credentials: Identifies credentials that have been leaked or compromised, enabling you to take immediate action to prevent unauthorized access to your systems.
Common Vulnerabilities and Exposures (CVEs)
-
Known CVEs: Tracks known vulnerabilities in software and systems, providing detailed information to help you prioritize and address these risks effectively.
Domain Security Issues
- DNS Misconfigurations: Detects misconfigurations in DNS settings that could be exploited by attackers, ensuring your domain settings are secure.
- SSL/TLS Issues: Identifies problems with SSL/TLS certificates, such as expired certificates or weak encryption protocols, helping you maintain secure communications.
Emerging Threat Intelligence
- Threat Intelligence: TRaViS provides insights into new and emerging threats that could impact your organization, allowing you to take proactive defense measures.
Web Application Vulnerabilities
- Cross-Site Scripting (XSS): Detects XSS vulnerabilities that could allow attackers to inject malicious scripts into your web pages, safeguarding your web applications.
- SQL Injection: Identifies SQL injection vulnerabilities that could be exploited to manipulate databases, protecting your data from unauthorized access.
- Cross-Site Request Forgery (CSRF): Detects CSRF vulnerabilities that could allow attackers to perform unauthorized actions on behalf of your users, maintaining the integrity of your web applications.
JavaScript and Content Vulnerabilities
- JavaScript Issues: Examines JavaScript code for security vulnerabilities, such as unsafe coding practices, preventing potential exploits.
- Content Security Policy (CSP): Detects weaknesses in your CSP that could lead to content injection attacks, strengthening your web application’s defenses.
Network Vulnerabilities
- Open Ports: Identifies open network ports that could be exploited by attackers, helping you close potential entry points.
- Weak Network Configurations: Detects weak network configurations that could be targeted, ensuring your network is configured for maximum security.
External Services and Dependencies
-
Third-Party Risks: Monitors and assesses the security of external services and dependencies your organization relies on, ensuring they do not introduce vulnerabilities into your systems.
Credential Reuse and Weak Passwords
-
Password Issues: Identifies weak or reused passwords that could be easily guessed or cracked by attackers, promoting stronger password policies across your organization.
Benefits of TRaViS

Integration
Seamless Compatibility
Integrate effortlessly with your existing security tools and technologies.
Risk
Assessment
Custom Fit Solutions
Detailed risk analysis and mitigation strategies to reduce your risk exposure.
Scalable
Flexible and
Scalable
Scale seamlessly to meet the security needs of any organization size.

Accessible
Pricing
Affordable
Plans
Choose from a variety of pricing plans to fit your organization's budget.
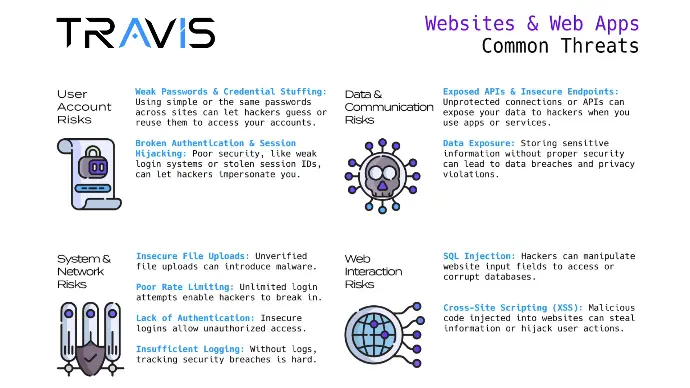
Want to learn more about common threats and vulnerabilities?
Websites & Web Apps Common Threats
Explanation: SQL Injection occurs when an attacker manipulates input fields, such as forms or URL parameters, to execute malicious SQL queries. This can give them unauthorized access to your database, allowing them to view, modify, or delete sensitive data.
Example: An e-commerce website allows users to search for products. If the search input is not properly sanitized, an attacker could enter a SQL command like ' OR '1'='1 which could return all data from the database instead of just relevant search results.
Explanation: XSS attacks involve injecting malicious scripts into webpages, which are then executed in the browsers of other users. This can lead to data theft, session hijacking, or unauthorized actions on behalf of the user.
- Persistent XSS: The injected script is stored on the server and affects every user that accesses the targeted page.
Example: A social media post containing malicious code could execute when viewed by other users, capturing their session cookies. - Reflected XSS: The malicious script is embedded in a URL and only affects users who click on that specific link.
Example: A phishing email contains a link that, when clicked, executes a script that steals login credentials. - DOM-based XSS: The attack manipulates the Document Object Model (DOM) on the client side rather than the server side.
Example: A search bar on a website processes input directly in the browser, allowing an attacker to inject a script that modifies the page's content or behavior.
Explanation: This vulnerability occurs when authentication mechanisms are poorly implemented, allowing attackers to gain unauthorized access to user accounts or session data.
- Session Hijacking: Attackers can steal or manipulate session IDs to impersonate users.
Example: If a session ID is exposed in a URL, an attacker could use it to take over the session and perform actions as the authenticated user. - Credential Stuffing: Attackers use automated tools to try large numbers of username and password combinations, exploiting users who reuse credentials across multiple sites.
Example: An attacker gains access to a list of leaked credentials from another site and uses them to access your web app, assuming users have reused passwords. - Weak Password Policies: Insufficient password requirements make it easier for attackers to guess or brute force passwords.
Example: Allowing users to set simple passwords like "password123" increases the risk of unauthorized access.
Explanation: APIs that are not properly secured can expose sensitive data or functionality to attackers. This can happen through insecure endpoints, lack of authentication, or poor rate limiting.
- Insecure Endpoints: Attackers can exploit open API endpoints to access data or services.
Example: An API endpoint allows users to retrieve account information without verifying their identity, leading to data exposure. - Lack of Authentication: APIs that do not require proper authentication leave your system open to unauthorized access.
Example: An API that doesn't verify user tokens can be accessed by anyone who knows the endpoint URL. - Poor Rate Limiting: Without limits on API requests, attackers can overwhelm your system with automated queries.
Example: An attacker sends thousands of requests per second to an API, leading to a denial of service.
Explanation: Without comprehensive logging, detecting and responding to security incidents becomes much more difficult. This can delay critical interventions and increase the impact of an attack.
Example: A data breach goes unnoticed for months because there were no logs of suspicious login attempts or data transfers.
Explanation: Data exposure occurs when sensitive information is not properly protected, leading to unauthorized access. This can result from insecure storage, lack of encryption, or improper access controls.
Example: Storing user passwords in plaintext rather than hashing them leaves them vulnerable to theft and misuse if the database is compromised.
Explanation: Allowing users to upload files without proper validation can introduce malware or other harmful content into your system.
Example: A user uploads a seemingly harmless image file, but it contains malicious code that executes when the file is processed by the server.
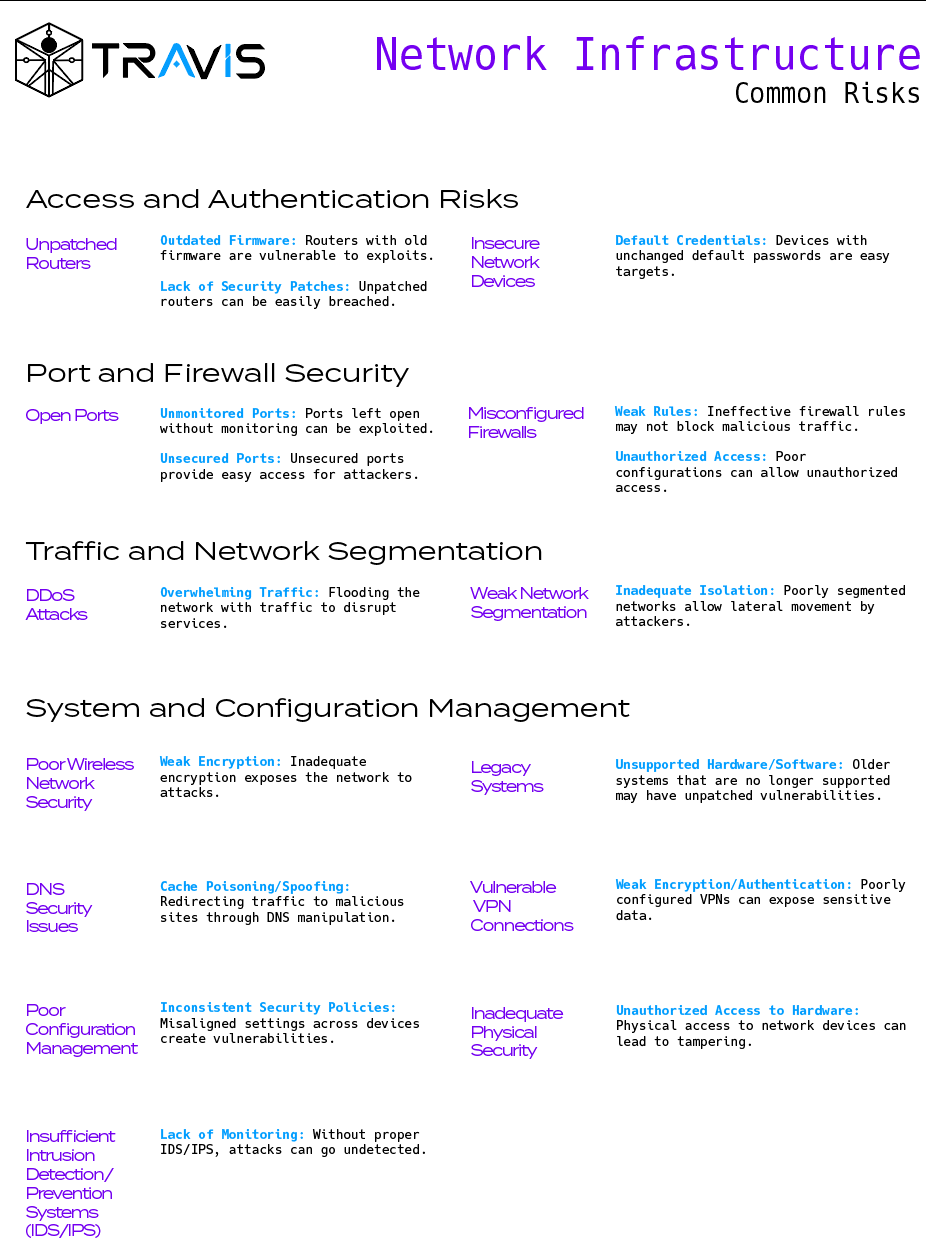
Explanation: Access and authentication risks involve vulnerabilities that allow unauthorized users to gain access to network resources. These risks often stem from weak authentication mechanisms, outdated devices, or insufficient security patches, which can be exploited by attackers to breach a network's defenses. Ensuring secure access controls, regularly updating devices, and enforcing strong authentication protocols are critical to mitigating these risks.
Unpatched Routers
Explanation: Outdated firmware or lack of security patches make routers vulnerable to known exploits, allowing attackers to easily gain access to the network.
Example: A small business uses an outdated router with no recent firmware updates, which is exploited by an attacker to gain unauthorized access to their internal network.
Insecure Network Devices
Explanation: Devices with unchanged default passwords or weak authentication mechanisms are easy targets for attackers.
Example: A company leaves default credentials on network switches, enabling a hacker to log in and manipulate network traffic.
Explanation: Port and firewall security pertains to the protection of network entry points and the rules governing traffic flow. Open ports and misconfigured firewalls can provide attackers with opportunities to access sensitive systems and data. Effective port management, constant monitoring, and well-configured firewall rules are essential to prevent unauthorized access and to block malicious traffic.
Open Ports
Explanation: Ports left open without monitoring can be used by attackers to exploit services running on those ports.
Example: An open port on a web server is not monitored, allowing an attacker to discover and exploit a vulnerable service running on that port.
Misconfigured Firewalls
Explanation: Ineffective firewall rules may allow unauthorized traffic, exposing the network to various attacks.
Example: A firewall is misconfigured, allowing inbound traffic on unnecessary ports, which leads to unauthorized access to internal systems.
Explanation: Traffic and network segmentation involves dividing a network into isolated segments to control the flow of traffic and limit the spread of attacks. Poor segmentation can allow attackers to move freely within the network after gaining access. Proper segmentation reduces the attack surface and ensures that compromised systems do not provide a gateway to other critical areas of the network.
DDoS Attacks
Explanation: Overwhelming the network with excessive traffic disrupts services, making them inaccessible to legitimate users.
Example: A company’s e-commerce site is targeted by a DDoS attack, flooding the network and making the site unavailable to customers.
Weak Network Segmentation
Explanation: Poorly segmented networks enable attackers to move laterally within the network, gaining access to more systems.
Example: A poorly segmented network allows an attacker who compromised a guest network to access critical internal systems.
Explanation: System and configuration management focuses on maintaining consistent security settings across all network devices and ensuring that systems are up to date. Vulnerabilities can arise from legacy systems, weak encryption, misconfigurations, or inadequate physical security. Effective management ensures that devices operate with aligned security policies and are resilient against potential exploits.
Poor Wireless Network Security
Explanation: Inadequate encryption and security measures expose wireless networks to unauthorized access.
Example: A retail store’s wireless network uses weak encryption, allowing a nearby attacker to intercept and access customer data transmitted over the network.
Legacy Systems
Explanation: Older systems that are no longer supported may have unpatched vulnerabilities that can be exploited.
Example: A manufacturing plant continues to use an old operating system on their control systems, which is vulnerable to a well-known exploit.
Vulnerable VPN Connections
Explanation: Poorly configured VPNs can expose sensitive data by failing to encrypt or authenticate connections properly.
Example: An employee connects to the company’s network using an outdated VPN with weak encryption, allowing an attacker to intercept and view sensitive data.
DNS Security Issues
Explanation: DNS manipulation can redirect users to malicious sites, compromising sensitive data.
Example: An attacker uses DNS spoofing to redirect traffic from a bank’s website to a fake site, collecting login credentials from unsuspecting users.
Poor Configuration Management
Explanation: Inconsistent security settings across devices create vulnerabilities that can be exploited.
Example: A company's network devices have different security policies, leading to gaps that an attacker can exploit to gain access to sensitive data.
Inadequate Physical Security
Explanation: Physical access to network devices or servers can lead to tampering, data theft, or other security breaches.
Example: An unauthorized person gains physical access to a server room and installs a device that captures and transmits sensitive information.
Insufficient Intrusion Detection/Prevention Systems (IDS/IPS)
Explanation: Without proper IDS/IPS, malicious activities can go undetected, increasing the risk of successful attacks.
Example: A network without IDS/IPS fails to detect a series of brute-force login attempts, resulting in a successful breach of a critical system.
Endpoints & Devices Common Threats
Endpoints and devices refer to the various hardware and software components within a network that users interact with directly, such as computers, smartphones, servers, and other connected devices. These endpoints are critical parts of a network's security infrastructure, as they can be the primary targets for attacks if not properly secured.
Malware is a broad term that encompasses various types of malicious software designed to harm, exploit, or otherwise compromise a computer system. Understanding the different types of malware is essential for recognizing potential threats and implementing appropriate defenses.
Malware
- Explanation: Malware refers to any software intentionally designed to cause damage to a computer, server, client, or network.
- Example: A user downloads what appears to be a legitimate application, but it secretly installs malware that monitors their keystrokes, leading to stolen credentials.
Viruses
- Explanation: A virus is a type of malware that attaches itself to a legitimate program and spreads to other programs and files on the system.
- Example: An employee unknowingly opens an infected email attachment, causing a virus to spread through the company's network, corrupting files.
Trojans
- Explanation: Trojans are malicious programs disguised as legitimate software, tricking users into installing them.
- Example: A user downloads a "free" game from a shady website, but it's actually a Trojan that opens a backdoor into their system, allowing unauthorized access.
Worms
- Explanation: Worms are a type of malware that replicate themselves and spread across networks without needing human interaction.
- Example: A worm exploits a vulnerability in the network’s operating system, rapidly spreading and consuming network resources, causing a major slowdown.
Ransomware
- Explanation: Ransomware is a type of malware that encrypts a user’s data and demands payment to restore access.
- Example: A healthcare provider's systems are encrypted by ransomware, and the attackers demand a large sum of money to restore access to patient records.
Managing software and ensuring timely updates are critical in protecting systems from vulnerabilities that attackers can exploit. Unpatched or outdated software can leave an organization exposed to threats that have already been addressed in newer versions.
Unpatched Software
- Explanation: Software that has not been updated with the latest security patches is vulnerable to known exploits.
- Example: A company continues to use an unpatched version of their CRM software, which is later exploited by hackers using a known vulnerability to steal customer data.
Exploitation of Known Vulnerabilities
- Explanation: Attackers often target known vulnerabilities in software to gain unauthorized access or cause damage.
- Example: An outdated web application is exploited by attackers who use a well-known SQL injection vulnerability to access the database.
Lack of Updates
- Explanation: Failing to regularly update software can leave systems vulnerable to attacks that have already been mitigated by newer versions.
- Example: A retailer fails to update their point-of-sale system, and attackers exploit an old vulnerability to siphon off credit card data.
Legacy Software
- Explanation: Legacy software refers to outdated applications that are no longer supported, making them vulnerable to attacks.
- Example: A manufacturing company relies on legacy software that is no longer supported, and a critical vulnerability is discovered and exploited by cyber criminals.
Password security is vital to protecting accounts and systems from unauthorized access. Weak, easily guessable, or reused passwords can provide an easy entry point for attackers.
- Weak Passwords
- Explanation: Passwords that are easy to guess or crack provide minimal security and are easily compromised.
- Example: An employee uses "password123" for their company email, and it is quickly guessed by an attacker who gains access to sensitive company communications.
- Easily Guessable
- Explanation: Passwords that follow common patterns or use personal information can be easily guessed by attackers.
- Example: An executive uses their birthdate as their password, making it easy for a hacker to guess and access their account.
- Reused
- Explanation: Using the same password across multiple accounts increases the risk that a single breach could lead to further compromises.
- Example: A user’s credentials are stolen from a compromised social media site, and because they used the same password for their email, the attackers gain access to it as well.
- Unchanged Default Credentials
- Explanation: Default credentials provided by manufacturers are widely known and should be changed immediately to prevent unauthorized access.
- Example: A new router is installed in an office but the default admin password is not changed, allowing a hacker to log in and alter the network settings.
Protecting data is crucial to maintaining privacy and security. Data encryption and safeguarding against extortion tactics like ransomware are key components of a robust cybersecurity strategy.
- Encryption of Data
- Explanation: Encryption converts data into a coded format that can only be read by someone with the decryption key, protecting it from unauthorized access.
- Example: A company's customer database is encrypted, ensuring that even if the data is stolen, it remains unreadable without the decryption key.
- Demands for Payment
- Explanation: Ransomware attacks often involve demands for payment in exchange for decrypting data or restoring access to systems.
- Example: A small business's accounting records are encrypted by ransomware, and the attackers demand a bitcoin payment to unlock the files.
Email Systems Common Threats
Email systems are an essential communication tool for individuals and organizations, but they also serve as a primary vector for cyberattacks. Due to their widespread use and direct access to users, email systems are frequently targeted by attackers aiming to distribute malware, steal sensitive information, or trick users into performing harmful actions. Common threats include phishing attacks, social engineering, and the distribution of malicious software like viruses and ransomware. To protect email systems, it's crucial to implement strong security measures such as spam filtering, user education, and regular software updates. Recognizing and understanding the various threats associated with email systems is key to maintaining the integrity and security of communications within any organization.

Phishing and social engineering attacks are methods used by cyber criminals to deceive individuals into revealing sensitive information or taking actions that compromise security. These tactics often involve impersonating legitimate entities or creating a sense of urgency to manipulate the victim.
- Phishing Attacks
- Explanation: Phishing attacks involve sending fraudulent emails that appear to come from a reputable source, tricking recipients into providing sensitive information or clicking malicious links.
- Example: An employee receives an email that looks like it’s from their bank, asking them to verify their account information. The link leads to a fake website designed to steal their login credentials.
- Malicious Emails
- Explanation: Malicious emails are messages designed to deliver harmful content, such as links to phishing sites, malware, or other security threats.
- Example: A user receives an email with a subject line claiming they have won a prize. The email contains a link that, when clicked, installs malware on their computer.
- Social Engineering
- Explanation: Social engineering involves manipulating individuals into performing actions or divulging confidential information by exploiting human psychology rather than technical vulnerabilities.
- Example: An attacker calls an employee pretending to be from the IT department, convincing them to share their password under the guise of performing system maintenance.
- Impersonation
- Explanation: Impersonation in emails involves pretending to be someone the recipient trusts, such as a colleague, boss, or partner, to trick them into taking harmful actions.
- Example: A CEO receives an email that looks like it's from their CFO, urgently requesting a wire transfer. The email is actually from an attacker impersonating the CFO.
Fraudulent and deceptive content in emails is designed to mislead recipients into believing the message is legitimate. This content can take various forms, such as spoofed email addresses, fake domains, or misleading links, all aimed at tricking the recipient into divulging information or downloading malicious software.
Deceptive Links
- Explanation: Deceptive links are URLs in emails that appear legitimate but redirect the user to malicious websites designed to steal information or install malware.
- Example: An email claims to be from a popular online store with a link to "track your order." The link actually leads to a phishing site that steals the user's login information.
Fraudulent Attachments
- Explanation: Fraudulent attachments are files sent via email that are disguised as legitimate documents but contain harmful software, such as malware or ransomware.
- Example: An employee receives an email with an attachment labeled as an "invoice." Opening the attachment installs ransomware on their computer, encrypting all their files.
Email Spoofing
- Explanation: Email spoofing involves forging the sender's address in an email to make it appear as though it’s coming from a trusted source, leading the recipient to believe the message is genuine.
- Example: A company receives an email that looks like it’s from a trusted vendor, requesting payment. The email address is spoofed, and the payment is sent to the attacker.
Forged Sender Addresses
- Explanation: Forged sender addresses are used in emails to trick recipients into thinking the message is from someone they know or trust. This tactic is often used in phishing and other deceptive schemes.
- Example: An email appears to be from a company's IT department, asking employees to reset their passwords. The sender’s address is forged, leading employees to a fake password reset page.
Fake Domains
- Explanation: Fake domains are look-alike URLs that closely resemble legitimate websites but are controlled by attackers to capture sensitive information or spread malware.
- Example: An employee receives an email from "paypa1.com," a domain that looks similar to "paypal.com," asking them to confirm their account details. The fake domain is used to steal their login information.
Malware and harmful software can be distributed through email attachments or links. These programs are designed to infiltrate systems, steal data, or cause damage. Understanding the different types of harmful software helps in recognizing and preventing such threats.
- Malware Attachments
- Explanation: Malware attachments are files included in emails that contain malicious software, which can infect the recipient’s computer when opened.
- Example: An HR employee opens an email attachment titled "Job Application" that installs a keylogger, capturing all the employee’s keystrokes, including passwords.
- Viruses and Trojans
- Explanation: Viruses are a type of malware that replicates and spreads by infecting other files, while Trojans disguise themselves as legitimate software to gain access to the system.
- Example: An employee downloads a free software update from an email, but it’s a Trojan that opens a backdoor for attackers to access the company network.
- Ransomware
- Explanation: Ransomware encrypts the victim's data, demanding payment to restore access. It is often distributed through email attachments or links.
- Example: A user opens an email attachment labeled "Invoice," which installs ransomware that locks all the files on their computer, demanding payment for the decryption key.
- Spyware
- Explanation: Spyware is software that secretly monitors and collects information about the user’s activities, often used to steal sensitive data.
- Example: An employee clicks on a link in a phishing email, unknowingly installing spyware that monitors their browsing activity and captures login credentials.
- Adware
- Explanation: Adware is software that automatically displays or downloads unwanted advertisements, often bundled with free software or distributed through deceptive emails.
- Example: After opening an email attachment, a user’s computer is flooded with pop-up ads, slowing down their system and potentially leading to more harmful malware.
Protecting data is crucial to maintaining privacy and security. Data encryption and safeguarding against extortion tactics like ransomware are key components of a robust cybersecurity strategy.
- Encryption of Data
- Explanation: Encryption converts data into a coded format that can only be read by someone with the decryption key, protecting it from unauthorized access.
- Example: A company's customer database is encrypted, ensuring that even if the data is stolen, it remains unreadable without the decryption key.
- Demands for Payment
- Explanation: Ransomware attacks often involve demands for payment in exchange for decrypting data or restoring access to systems.
- Example: A small business's accounting records are encrypted by ransomware, and the attackers demand a bitcoin payment to unlock the files.
Cloud Services - Common Risks and Threats
Cloud services have become integral to modern businesses, providing scalable and flexible computing resources. However, the migration to cloud environments introduces various risks and threats. These risks can range from data breaches and exposure of sensitive data to vulnerabilities in cloud storage and access controls. Understanding these risks is essential for organizations to protect their cloud infrastructure and maintain the confidentiality, integrity, and availability of their data.

Data security in cloud services involves protecting sensitive information from unauthorized access, breaches, and exposure. Given the vast amount of data stored in the cloud, maintaining strong encryption, access controls, and monitoring is crucial to safeguarding this data from potential threats.
- Data Breaches
- Explanation: A data breach occurs when unauthorized individuals gain access to confidential data stored in the cloud, often resulting in financial loss, legal penalties, and damage to an organization's reputation.
- Example: A cloud storage provider experiences a breach where hackers gain access to thousands of customer records, including personal and financial information.
- Exposure of Sensitive Data
- Explanation: Sensitive data can be unintentionally exposed due to misconfigurations or inadequate security measures, making it accessible to unauthorized users.
- Example: An employee accidentally configures a cloud storage bucket to be publicly accessible, exposing sensitive customer data to the internet.
- Lack of Encryption
- Explanation: Without proper encryption, data stored or transmitted in the cloud is vulnerable to interception and unauthorized access, as attackers can easily read unencrypted data.
- Example: A company stores sensitive customer data in the cloud without encryption, and a hacker intercepts the data during transmission, gaining access to confidential information.
Proper storage and access control are vital to preventing unauthorized access to cloud resources. Misconfigurations, weak passwords, and insufficient controls can lead to vulnerabilities that attackers can exploit to gain unauthorized access to cloud data and systems.
- Misconfigured Storage
- Explanation: Misconfigurations in cloud storage can lead to unintentional exposure of data, making it accessible to unauthorized users or the public.
- Example: A company misconfigures its cloud storage settings, inadvertently making private documents accessible to anyone with the link.
- Publicly Accessible Storage Buckets
- Explanation: Publicly accessible storage buckets are cloud storage containers that have been configured to allow public access, often unintentionally, leading to potential data exposure.
- Example: An organization’s storage bucket containing sensitive employee records is accidentally set to public, allowing anyone on the internet to download the files.
- Unauthorized Access
- Explanation: Unauthorized access refers to individuals gaining access to cloud resources or data without proper authorization, often due to weak security controls or misconfigurations.
- Example: A former employee still has access to the company's cloud services and uses their credentials to download confidential business plans.
- Insufficient Access Controls
- Explanation: Insufficient access controls can lead to unauthorized users gaining access to sensitive data or resources, as not all users are appropriately restricted.
- Example: A company fails to enforce strict access controls, allowing a low-level employee to access sensitive financial records in the cloud.
- Weak Passwords
- Explanation: Weak passwords used to access cloud services can be easily guessed or cracked, leading to unauthorized access to sensitive data and systems.
- Example: An employee uses a simple password, such as "password123," for their cloud account, which is easily guessed by an attacker who then accesses the company’s cloud resources.
APIs and endpoints are critical components of cloud services that allow communication between different systems. However, if not properly secured, they can become entry points for attackers to exploit and gain unauthorized access to cloud resources.
- API Vulnerabilities
- Explanation: APIs are interfaces that allow different software systems to communicate, but they can contain vulnerabilities that attackers can exploit to gain unauthorized access or manipulate data.
- Example: An attacker exploits an insecure API endpoint in a cloud service, allowing them to retrieve confidential customer information from the database.
- Exposed Credentials
- Explanation: Exposed credentials, such as API keys or access tokens, can be exploited by attackers to gain unauthorized access to cloud services, leading to data breaches or system compromise.
- Example: A developer accidentally uploads an API key to a public GitHub repository, allowing attackers to use the key to access and manipulate the company’s cloud resources.
- Insecure Endpoints
- Explanation: Insecure endpoints refer to network entry points that are not adequately protected, making them vulnerable to attacks that can compromise the security of the entire cloud environment.
- Example: A cloud service’s endpoint lacks proper authentication mechanisms, allowing an attacker to gain access to the service and extract sensitive information.
Effective system and performance management is crucial to maintaining the security and reliability of cloud services. Issues such as improper rate limiting and error handling can lead to vulnerabilities that attackers can exploit, affecting the overall performance and security of cloud-based systems.
- Improper Rate Limiting
- Explanation: Rate limiting controls the number of requests a user can make to a service in a given time period. Improper rate limiting can allow attackers to overwhelm a system with excessive requests, leading to denial-of-service attacks or system overloads.
- Example: A cloud service fails to implement proper rate limiting, allowing an attacker to flood the service with requests, causing it to crash and become unavailable to legitimate users.
- Improper Error Handling
- Explanation: Improper error handling can expose sensitive information or provide attackers with clues about vulnerabilities in the system, leading to further exploitation.
- Example: A cloud-based application displays detailed error messages that reveal the structure of the underlying database, which an attacker uses to launch a SQL injection attack.
Protecting data is crucial to maintaining privacy and security. Data encryption and safeguarding against extortion tactics like ransomware are key components of a robust cybersecurity strategy.
- Encryption of Data
- Explanation: Encryption converts data into a coded format that can only be read by someone with the decryption key, protecting it from unauthorized access.
- Example: A company's customer database is encrypted, ensuring that even if the data is stolen, it remains unreadable without the decryption key.
- Demands for Payment
- Explanation: Ransomware attacks often involve demands for payment in exchange for decrypting data or restoring access to systems.
- Example: A small business's accounting records are encrypted by ransomware, and the attackers demand a bitcoin payment to unlock the files.
IoT Devices - Common Risks and Threats
The proliferation of Internet of Things (IoT) devices has introduced numerous benefits to both consumers and businesses, offering convenience and automation. However, these devices also present significant security challenges due to their often limited processing power, lack of built-in security features, and the sheer volume of connected devices. The risks associated with IoT devices include insecure connections, weak authentication, and vulnerabilities that can be exploited by attackers to hijack devices, launch distributed attacks, or participate in DDoS attacks.

IoT devices often rely on wireless connections to communicate with each other and with central systems. If these connections are not secure, they can be intercepted by attackers, leading to data breaches or unauthorized control of the devices. Ensuring that data is encrypted both in transit and at rest is critical to maintaining the integrity and confidentiality of the information.
- Insecure Connections
- Explanation: Insecure connections between IoT devices and networks can be intercepted by attackers, allowing them to access or manipulate the data being transmitted.
- Example: A smart home security system communicates with the homeowner’s smartphone over an unsecured Wi-Fi network, allowing an attacker to intercept the communication and gain control of the system.
- Lack of Encryption
- Explanation: Without encryption, data transmitted between IoT devices and networks is vulnerable to interception and unauthorized access, exposing sensitive information.
- Example: A wearable fitness tracker sends health data to the cloud without encryption, making it easy for attackers to intercept and steal the data.
- Unencrypted Data
- Explanation: Data stored or transmitted by IoT devices that is not encrypted can be easily accessed by attackers, leading to data breaches and unauthorized access to sensitive information.
- Example: A smart thermostat stores user preferences in an unencrypted format, allowing an attacker to access and alter the settings to their advantage.
Authentication is the process by which IoT devices verify the identity of users or other devices before granting access. Weak authentication mechanisms can allow unauthorized access to the device, leading to potential exploitation. Additionally, firmware vulnerabilities, outdated firmware, and unpatched exploits are common issues that can leave IoT devices exposed to attacks.
- Weak Authentication
- Explanation: IoT devices with weak authentication mechanisms, such as default or easily guessable passwords, are susceptible to unauthorized access.
- Example: A smart lock uses a default password that is never changed, allowing an attacker to gain access to the homeowner's property.
- Firmware Vulnerabilities
- Explanation: Firmware vulnerabilities are weaknesses in the low-level software that runs IoT devices, which can be exploited by attackers to gain control of the device or extract sensitive information.
- Example: An IoT camera has a firmware vulnerability that allows attackers to remotely view its feed and access recorded footage without the owner’s consent.
- Outdated Firmware
- Explanation: Outdated firmware may contain known vulnerabilities that have been fixed in newer versions, but if the device is not updated, it remains susceptible to attacks.
- Example: A connected medical device has not received a firmware update in years, making it vulnerable to a known exploit that could allow an attacker to manipulate its functionality.
- Unpatched Exploits
- Explanation: Unpatched exploits are security flaws in IoT devices that have been identified but not yet addressed by the manufacturer, leaving the device vulnerable to attacks.
- Example: A smart refrigerator has an unpatched exploit that allows attackers to remotely control its functions, potentially leading to spoiled food and energy waste.
IoT devices, due to their often limited security measures, can be hijacked by attackers and used for malicious purposes. This includes being part of a botnet for launching distributed attacks or participating in Distributed Denial of Service (DDoS) attacks. These activities can cause widespread disruption and damage to other systems and networks.
- Botnet Infections
- Explanation: A botnet is a network of compromised devices controlled by an attacker, often used to carry out large-scale attacks such as DDoS. IoT devices are frequently targeted due to their weak security.
- Example: An attacker compromises thousands of smart home devices, turning them into a botnet that is used to launch a DDoS attack on a major website, causing it to crash.
- Hijacked Devices
- Explanation: Hijacked devices are IoT devices that have been taken over by attackers, who can use them for unauthorized activities such as spying, launching attacks, or accessing other systems.
- Example: A baby monitor is hijacked by an attacker, allowing them to listen in on private conversations and even speak through the device’s speaker.
- Distributed Attacks
- Explanation: Distributed attacks involve multiple compromised devices being used simultaneously to attack a target, often overwhelming the target’s defenses and causing system failures.
- Example: A coordinated attack using compromised IoT devices floods an online service with traffic, causing it to become unavailable to legitimate users.
- DDoS Participation
- Explanation: DDoS (Distributed Denial of Service) attacks involve overwhelming a target with a flood of internet traffic, often using hijacked IoT devices as the source of the traffic.
- Example: An IoT-enabled coffee maker is compromised and used as part of a larger botnet to participate in a DDoS attack, contributing to the shutdown of an e-commerce website.
Protecting data is crucial to maintaining privacy and security. Data encryption and safeguarding against extortion tactics like ransomware are key components of a robust cybersecurity strategy.
- Encryption of Data
- Explanation: Encryption converts data into a coded format that can only be read by someone with the decryption key, protecting it from unauthorized access.
- Example: A company's customer database is encrypted, ensuring that even if the data is stolen, it remains unreadable without the decryption key.
- Demands for Payment
- Explanation: Ransomware attacks often involve demands for payment in exchange for decrypting data or restoring access to systems.
- Example: A small business's accounting records are encrypted by ransomware, and the attackers demand a bitcoin payment to unlock the files.
Dark Web - Common Risks and Threats
The Dark Web is a hidden part of the internet that is not indexed by traditional search engines and is often used for illegal activities. It serves as a marketplace for cybercriminals to buy and sell stolen data, exploit kits, and hacking tools. The anonymity provided by the Dark Web allows criminals to exchange techniques, coordinate attacks, and sell intellectual property and company secrets. Understanding the risks associated with the Dark Web is crucial for organizations to protect themselves from data breaches, intellectual property theft, and other forms of cybercrime.

Want to learn more? Click the tabs to learn about :
- Stolen and Exposed Data
- Exploitation Tools and Vulnerabilities
- Cybercriminal Communities
The Dark Web is a hub for trading stolen and exposed data, including login credentials, personal information, and company secrets. Data that is leaked from breaches or intentionally stolen is often sold on illegal markets, where it can be used for identity theft, financial fraud, or corporate espionage.
- Stolen Credentials
- Explanation: Stolen credentials, such as usernames and passwords, are frequently sold on the Dark Web. These credentials can be used for unauthorized access to accounts and systems.
- Example: A hacker sells a list of stolen email addresses and passwords on the Dark Web, which are then used by other criminals to access bank accounts and commit fraud.
- Leaked from Breaches
- Explanation: Data that has been compromised in a breach often finds its way to the Dark Web, where it is sold to the highest bidder.
- Example: A major retailer suffers a data breach, and the personal information of millions of customers is leaked and subsequently sold on Dark Web forums.
- Sold on Illegal Markets
- Explanation: The Dark Web hosts illegal markets where cybercriminals buy and sell stolen data, including credit card information, medical records, and other sensitive data.
- Example: A cybercriminal purchases a batch of stolen credit card numbers from an illegal market on the Dark Web and uses them for fraudulent purchases.
- Data Leaks
- Explanation: Data leaks involve the unauthorized release of sensitive information, often due to negligence or intentional acts, which are then made available on the Dark Web.
- Example: An insider at a company leaks proprietary business plans, which are posted on a Dark Web forum for other criminals to exploit.
- Exposed Personal Data
- Explanation: Personal data such as Social Security numbers, addresses, and phone numbers can be exposed on the Dark Web, leading to identity theft and other forms of fraud.
- Example: A hacker publishes a database of Social Security numbers on the Dark Web, which is used by criminals to open fraudulent credit accounts in victims' names.
- Company Secrets
- Explanation: Sensitive corporate information, such as trade secrets or internal communications, can be stolen and sold on the Dark Web, leading to significant business risks.
- Example: A competitor purchases stolen proprietary technology designs on the Dark Web and uses them to gain an unfair advantage in the market.
- Intellectual Property
- Explanation: Intellectual property, such as patents, trademarks, and copyrights, can be stolen and sold on the Dark Web, leading to significant financial and reputational damage for the affected companies.
- Example: A pharmaceutical company’s drug formula is stolen and sold on the Dark Web, allowing other companies to produce and sell the drug illegally.
The Dark Web is a marketplace for various tools and kits that cybercriminals use to exploit known vulnerabilities in software and systems. These tools are often pre-packaged and easy to use, making it possible for even low-skilled attackers to launch sophisticated attacks.
- Exploit Kits
- Explanation: Exploit kits are collections of tools and scripts designed to take advantage of specific vulnerabilities in software or systems, often sold on the Dark Web to enable attacks.
- Example: A cybercriminal purchases an exploit kit from the Dark Web that targets a known vulnerability in a popular web browser, allowing them to compromise users’ devices when they visit a malicious website.
- Pre-packaged Attack Tools
- Explanation: Pre-packaged attack tools are ready-made kits that allow cybercriminals to launch attacks with minimal effort. These tools are often available for purchase on the Dark Web.
- Example: An attacker buys a pre-packaged phishing kit from the Dark Web, which includes email templates and a fake login page, enabling them to easily launch a phishing campaign.
- Targeted at Known Vulnerabilities
- Explanation: Tools and exploits sold on the Dark Web are often designed to target known vulnerabilities in widely-used software, making them highly effective in attacks.
- Example: A vulnerability in a widely-used content management system is exploited using a tool purchased on the Dark Web, allowing the attacker to deface websites or steal data.
The Dark Web serves as a gathering place for cybercriminals to share knowledge, exchange tools, and coordinate attacks. Hacking forums and other platforms on the Dark Web provide a space for criminals to learn from each other, buy and sell services, and plan coordinated attacks on targets.
- Hacking Forums
- Explanation: Hacking forums on the Dark Web are online communities where cybercriminals discuss techniques, share exploits, and offer services such as hacking for hire.
- Example: A new hacker joins a Dark Web forum to learn about the latest phishing techniques and buys a set of stolen credentials to practice with.
- Exchange of Techniques and Tools
- Explanation: Cybercriminals on the Dark Web frequently exchange techniques, tools, and tips, allowing them to improve their skills and carry out more effective attacks.
- Example: Experienced hackers on a Dark Web forum share code snippets and instructions for creating undetectable malware, helping others to enhance their attack methods.
- Coordination of Attacks
- Explanation: The anonymity of the Dark Web allows cybercriminals to coordinate large-scale attacks, such as distributed denial-of-service (DDoS) attacks or ransomware campaigns, without fear of being easily traced.
- Example: A group of hackers uses a Dark Web forum to coordinate a DDoS attack on a major financial institution, pooling their resources to overwhelm the target’s defenses.
Protecting data is crucial to maintaining privacy and security. Data encryption and safeguarding against extortion tactics like ransomware are key components of a robust cybersecurity strategy.
- Encryption of Data
- Explanation: Encryption converts data into a coded format that can only be read by someone with the decryption key, protecting it from unauthorized access.
- Example: A company's customer database is encrypted, ensuring that even if the data is stolen, it remains unreadable without the decryption key.
- Demands for Payment
- Explanation: Ransomware attacks often involve demands for payment in exchange for decrypting data or restoring access to systems.
- Example: A small business's accounting records are encrypted by ransomware, and the attackers demand a bitcoin payment to unlock the files.
TRaViS restored our faith in humanity.
Other tools find files, TRaViS discovers them.
TRaViS is a very cool piece of software. Between the speed and the various features it has, I get all the things I need in one tool.
TRaViS helped us uncover IP's to several internal machines we had exposed on the internet. If an attacker found a bug. such as an SSRF, we could have been breached easily.
TRaViS found a data leak that exposed our customers information. Better and cheaper than any other tool I've used.
TRaViS helped us discover several assets we did not know we owned - or had forgotten about
Incredible tool with a world class team. Completely impressed.
External Attack Surface Management
With TRaViS, protect your digital assets with unmatched efficiency.
Join Leading Organizations in Securing Digital Assets.
Sign Up For TRaViS Today and Start Securing Your Business.
Security for business assets is a critical aspect for companies operating online.